Power consumption attack resisting method based on cyclic shift of bit permutation and fixed permutation table
A bit permutation and permutation table technology, applied in the field of cryptographic algorithms, can solve the problems of increasing the degree of confusion, increasing the difficulty of attacks, and low resistance to power consumption attacks, and achieving the effect of high degree of confusion and increased difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
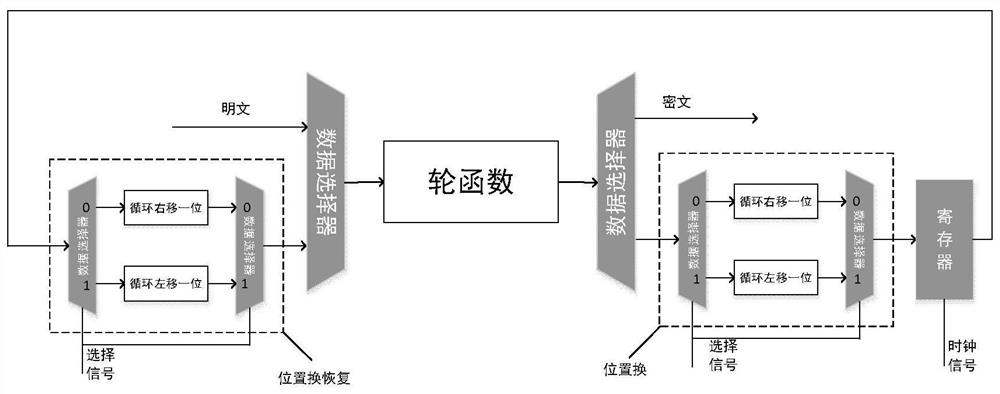
[0029] The anti-power consumption attack method based on the cyclic shift of bit permutation and fixed permutation table described in the present invention comprises steps:
[0030] (1-1) Input plaintext, when a round of calculation is completed, input different paths according to the state; if the calculation is completed, directly output the ciphertext; if the calculation is not completed, the intermediate value is bit-replaced and stored in the register;
[0031] (1-2) Before the next round of calculation starts, the bit permutation recovery operation is performed first, so that the intermediate values are restored to the original order, and subsequent calculations are performed.
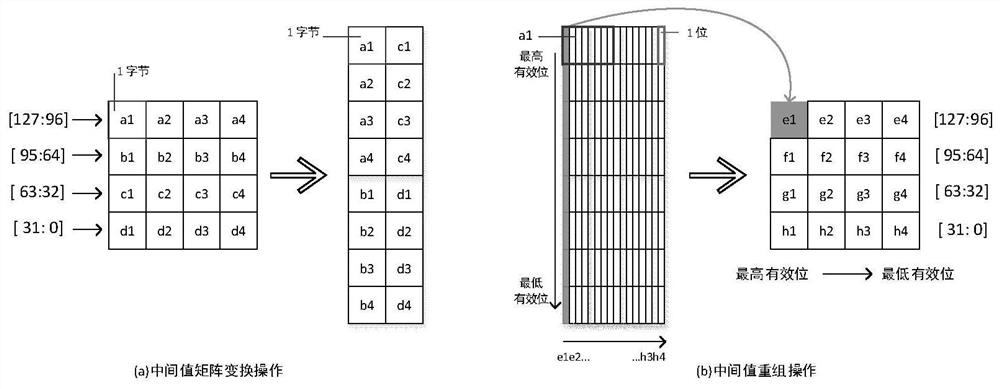
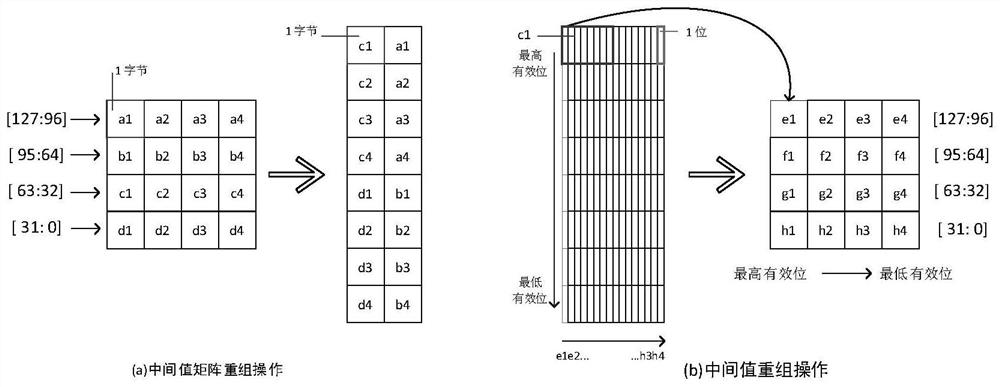
[0032] Bit permutation includes cyclic shift scheme and fixed permutation table scheme.
[0033] Such as figure 1 As shown, bit permutation ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com