Identity authentication method fusing user multi-source sound production characteristics, storage medium and equipment
An identity authentication and user technology, applied in the field of radio frequency identification and voice authentication, can solve problems such as voice command replay attack, privacy leakage, fingerprint authentication infection risk, etc., to reduce storage and, high reliability, ensure daily use fluency effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
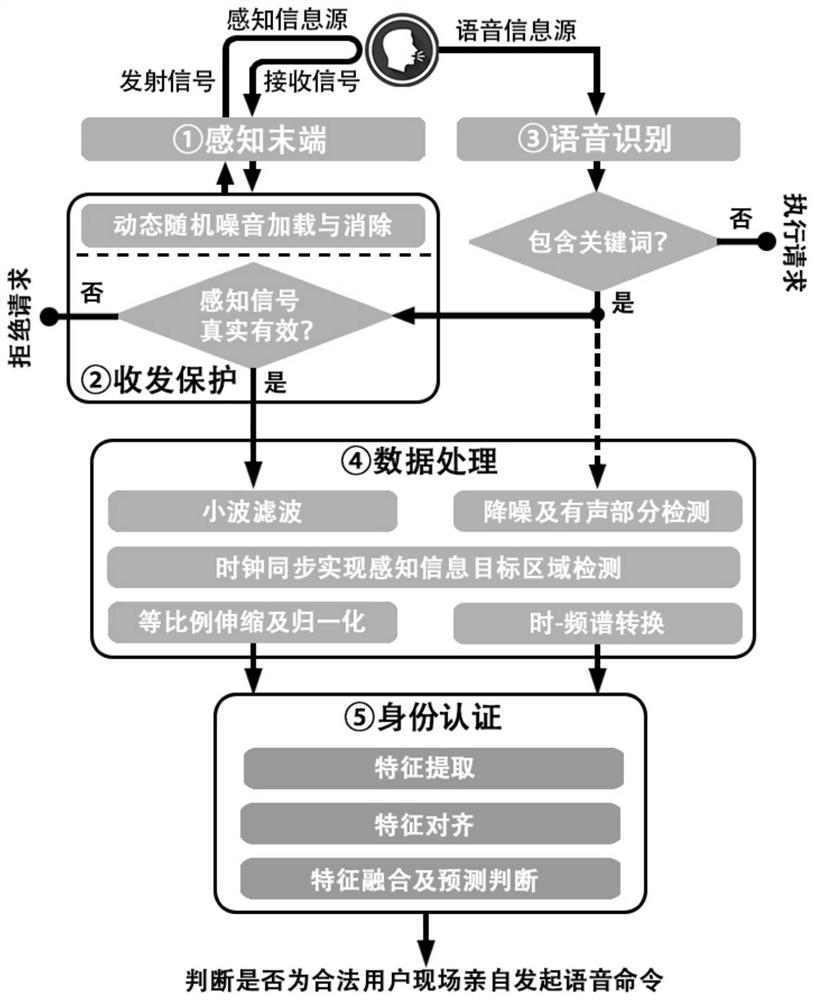
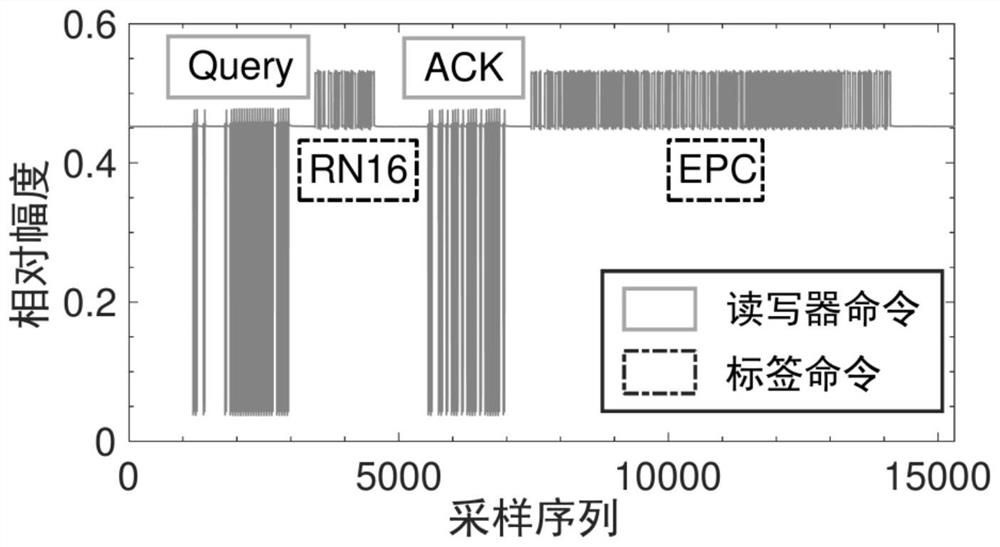
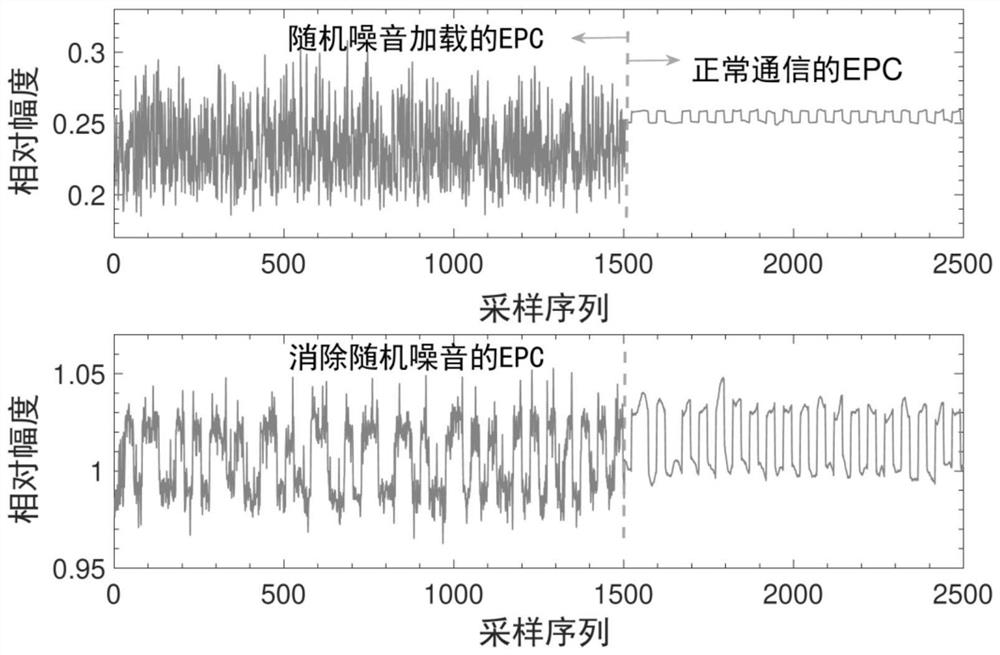
[0041]The present invention provides an identity authentication method, storage medium and equipment that integrates the user's multi-source vocalization characteristics, comprehensively considers the advantages and disadvantages and characteristics of common authentication technologies, and uses radio frequency identification (RFID) signal physical layer information to perceive the user's mouth when uttering Motion features (first source, perceptual information source), use microphones to receive voice commands from users (second source, voice information source), and by designing a dual-branch neural network, the identity features are extracted from the multi-source information of the user’s voice at the same time. Achieve fusion authentication; by designing a dynamic random noise loading and recovery mechanism at the RF transceiver end, the security risk of RF sensing signals being replayed together with voice signals by attackers is eliminated. It not only has the availability i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com