Intelligent supervision method, device and system for network security equipment
A network security and equipment management technology, applied in the field of network information security, can solve the problems of lack of interest, uneven personnel quality and professional level, and inability to set up test services and management, so as to improve the efficiency of test services and reduce equipment management. Difficulty and the effect of automated testing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
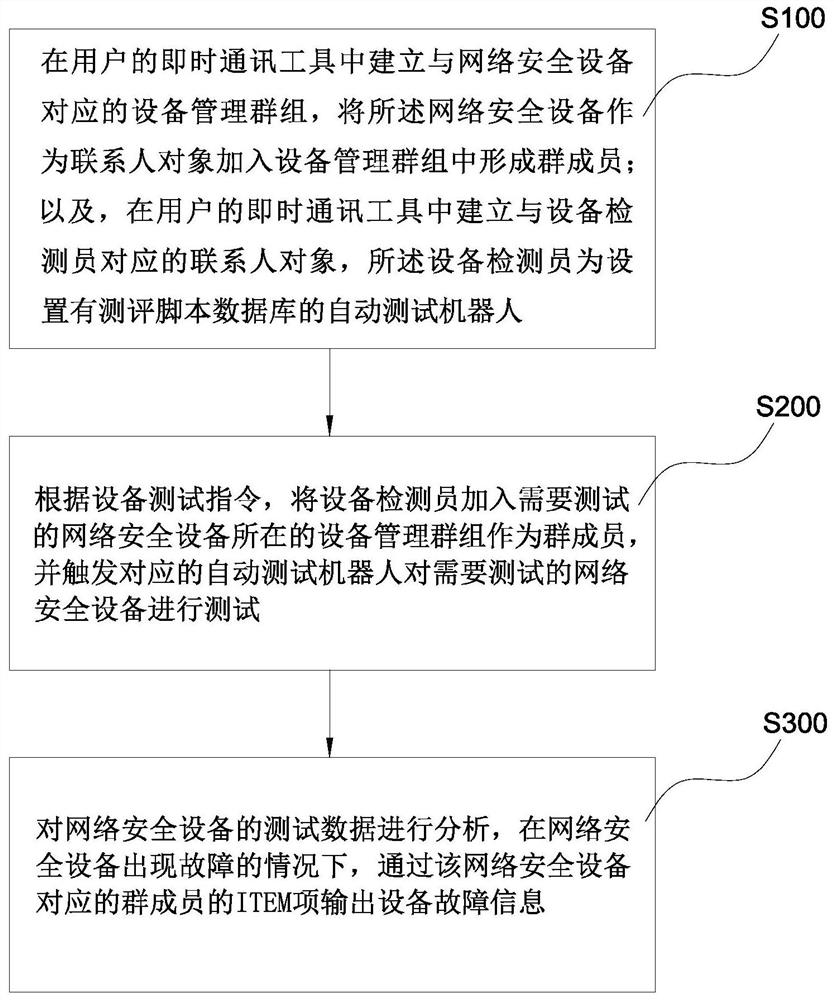
[0051] see figure 1 As shown, it is an intelligent supervision method for a network security device provided by an embodiment of the present invention. Described method comprises the steps:
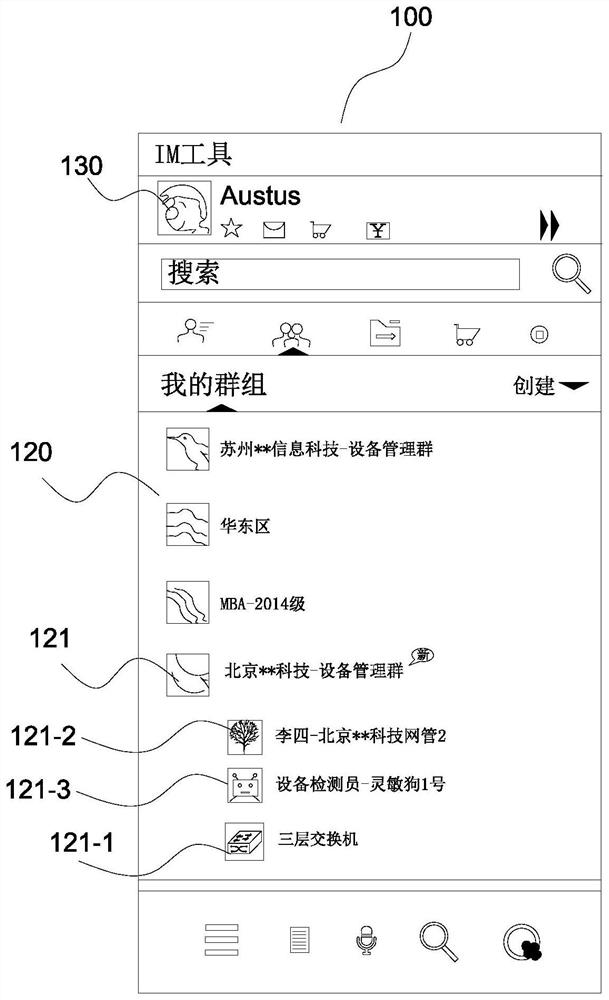
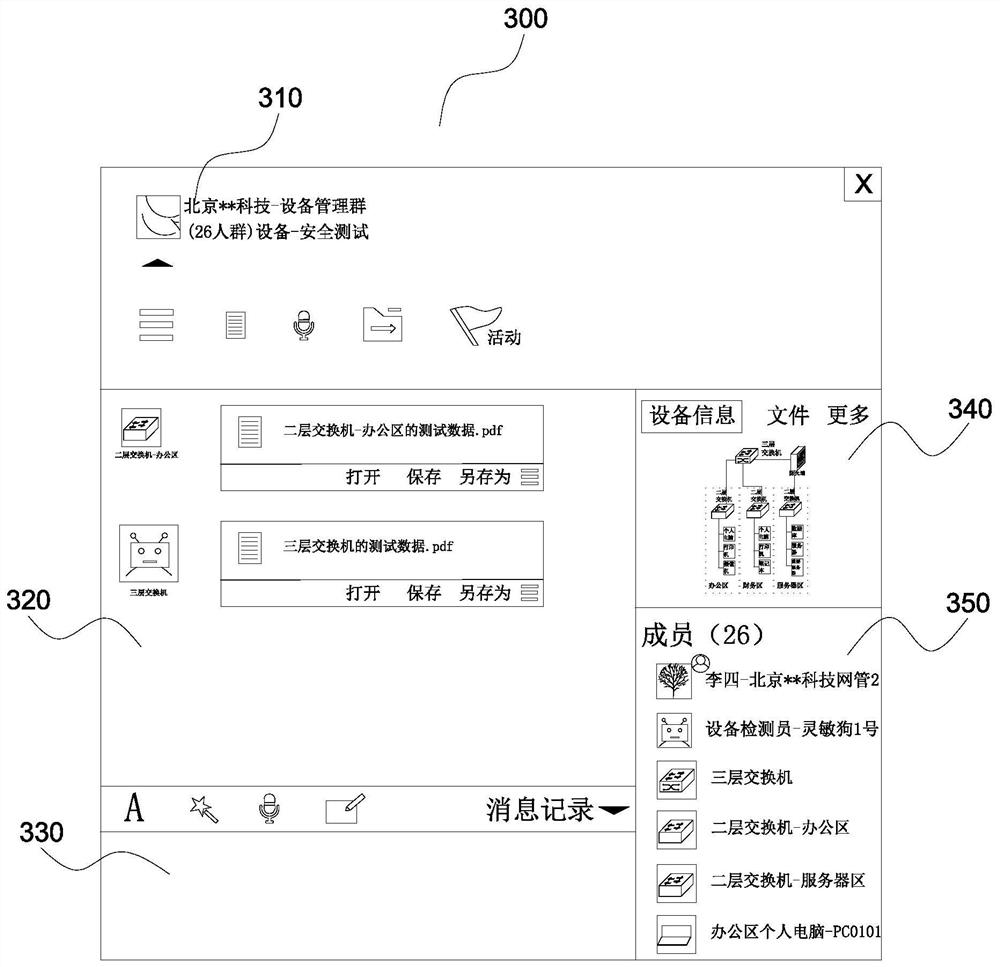
[0052] S100. Establish a device management group corresponding to the network security device in the user's instant messaging tool, and add the network security device as a contact object to the device management group to form a group member; and, in the user's instant messaging tool A contact object corresponding to an equipment inspector is established, and the equipment inspector is an automatic test robot provided with an evaluation script database.
[0053] The instant messaging tool may also be referred to as an instant messaging tool, and generally refers to a client with an instant messaging function in the field. As an example and not a limitation, the instant messaging tool may be a network version application, a PC version application or a handheld terminal APP application. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com