Android malicious code detection method based on deep learning
A technology of malicious code detection and deep learning, applied in the direction of neural learning methods, computer security devices, instruments, etc., can solve the problems of lower detection efficiency, high time consumption, and inefficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
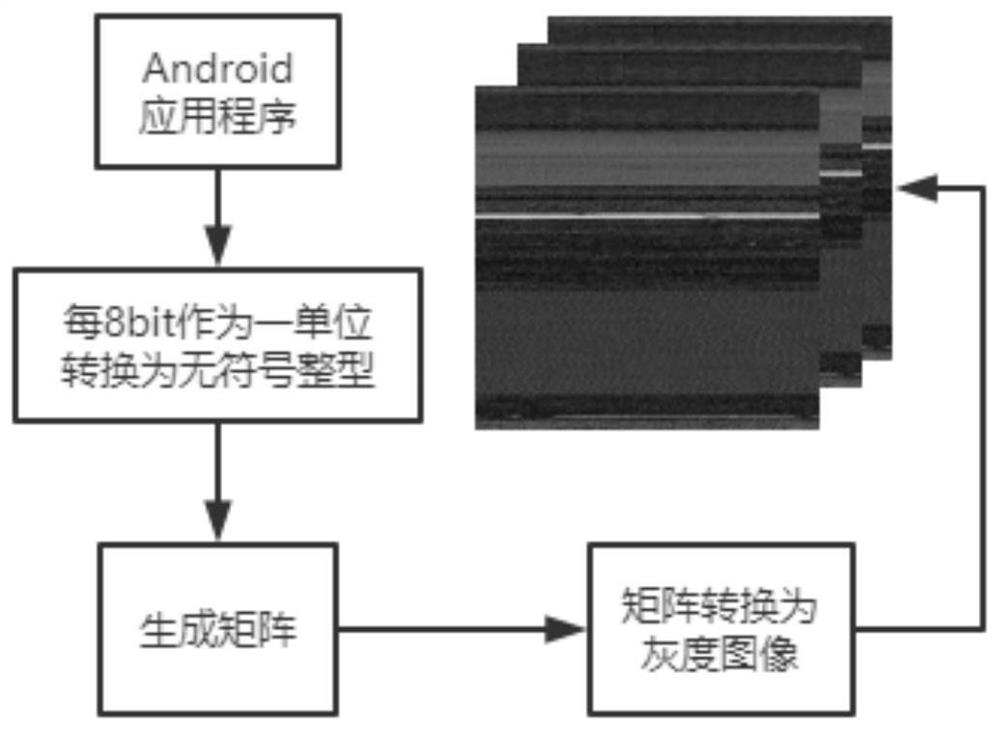
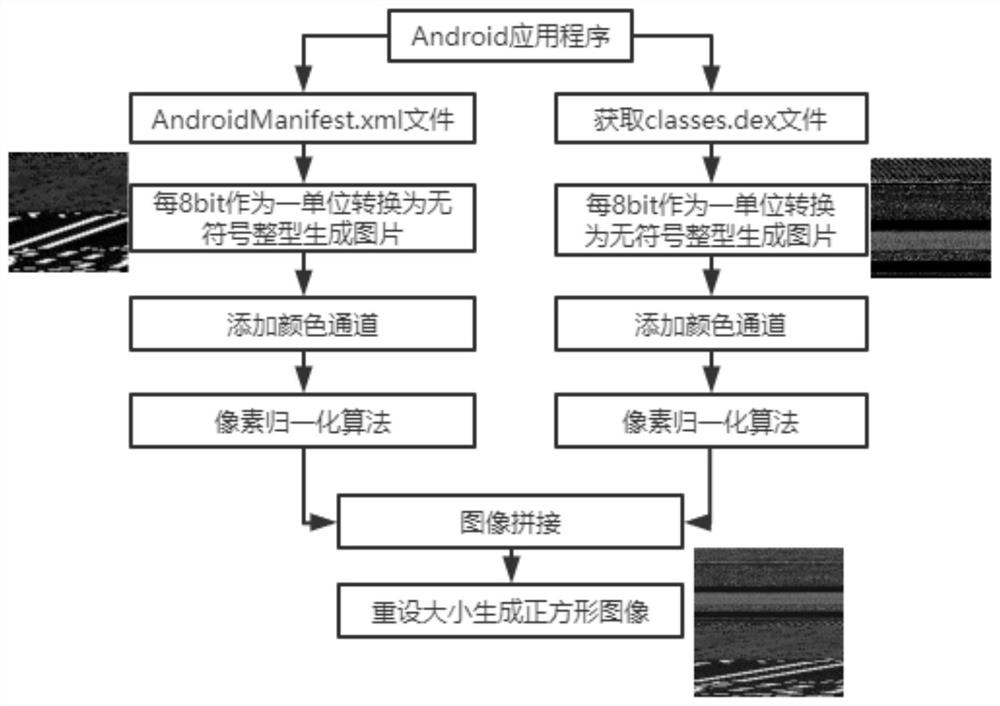
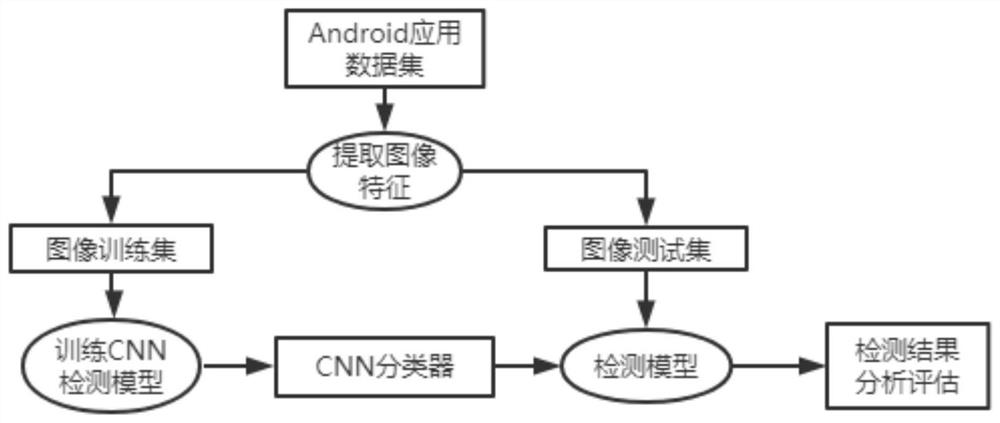
[0041] 1. The process of Android application visualization is the process of generating feature images corresponding to application binary files. Using the B2M algorithm, firstly, the program binary file corresponds to an unsigned integer vector, and then each 8bit corresponds to an unsigned integer data. According to the size of the source program file, save the unit8 vector in matrix form. In this way, a matrix with a value range of [0, 255] is obtained. This matrix generates a pixel matrix according to the value corresponding to the pixel value, and finally saves the pixel matrix as a grayscale image. In the pixel mapping process, 0 and 255 correspond to black and white, respectively. The size of the generated pixel matrix is related to the size of the source program file. The length and width values can be set in advance, or can be obtained adaptively according to the file size. After pixel matrix correspondence, a grayscale image is obtained. This time the image as...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com