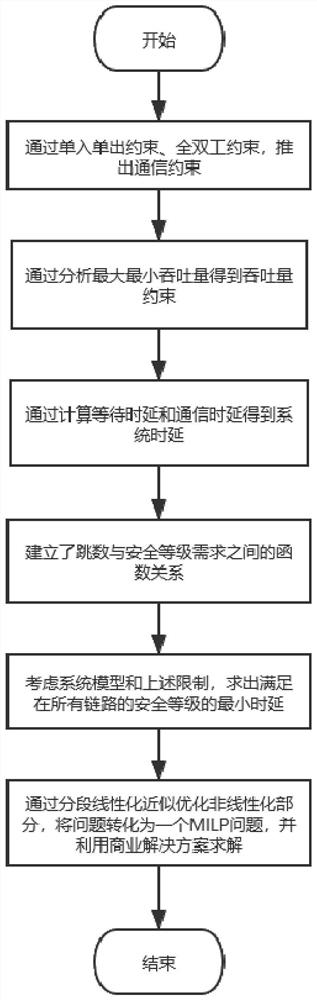
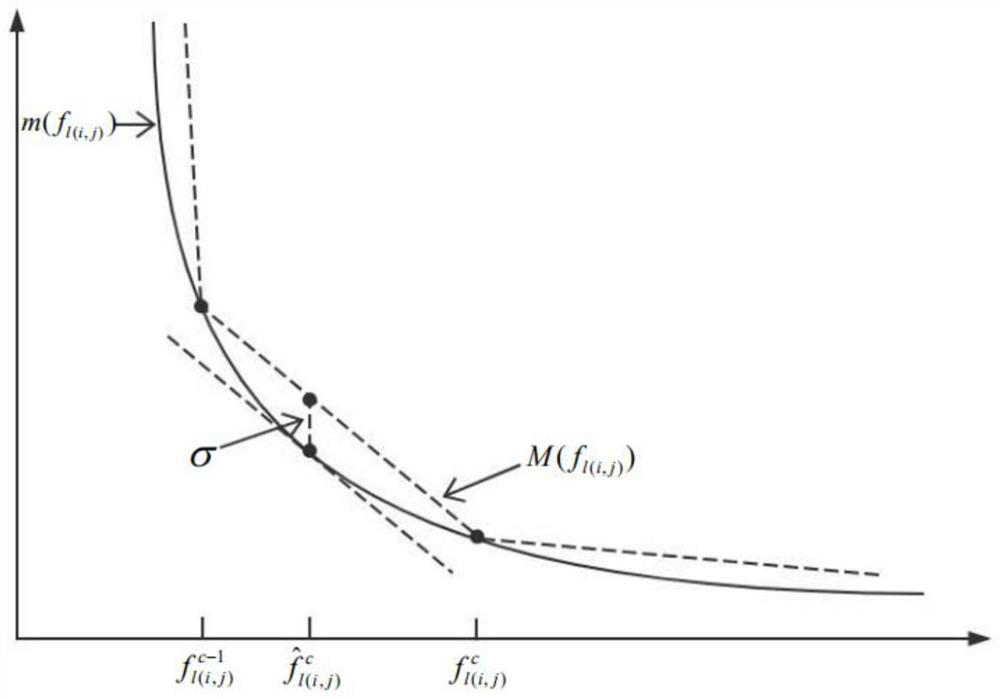
Anti-traceability security controlled network access channel resource optimal configuration algorithm
A resource-optimized and secure technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as infringement of user privacy and damage to security interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
experiment example 1
[0136] Experimental example 1: Study the influence of data packet generation rate on average delay
[0137] Experimental results such as Figure 5 As shown, first analyze the impact of the packet generation rate on the average delay. Two cases where the number of sessions are 2 and 3 respectively are considered. Generally, the time delay for simultaneous transmission of three sessions is greater than the time delay for simultaneous transmission of two sessions. We assume that the number of hops required for all sessions is 2. Under the data packet generation rate λ of [1,10], it can be easily obtained from the figure that when λ is less than or equal to 2, the delay in both cases increases slowly. When λ When it is greater than 2, the average session delay increases almost linearly with the increase of λ. This is because under light load, there are enough idle links to transmit data, and the waiting time is negligible. As the generation rate increases, the system starts to ...
experiment example 2
[0138] Experimental example 2: Scheduling results when link resources are scarce
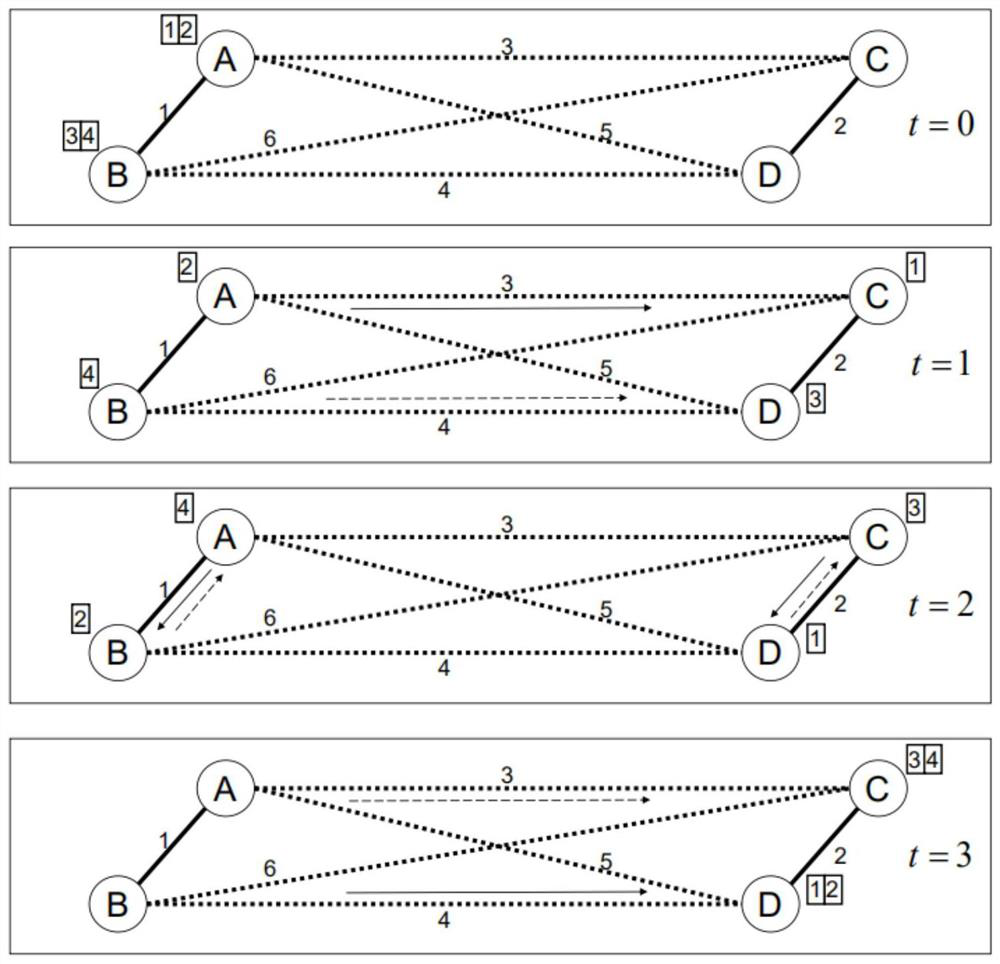
[0139] Assume that two sessions need to be provided at the same time, and the hop count requirements of the two sessions are 2 and 3 respectively. The packet generation rate of the two sessions is 6, and there are 6 available links in the network, among which links 1, 4, and 5 are internal links, and links 2, 3, and 6 are inter-environmental links.
[0140] The scheduling results under resource scarcity are as follows: Figure 6 as shown in Figure 6 In Figure a, session 1 activates the link 12 times in total. Since the minimum hop count requirement is 2 and the packet generation rate is 6, the scheduling algorithm meets the minimum hop count requirement for session 1. Similarly, Figure 5 The b diagram can also be used to draw the conclusion that the scheduling algorithm meets the minimum hop count of session 2. combine Figure 6 a map of and Figure 6 In Figure b, it can be seen that the ...
experiment example 3
[0141] Experimental example 3: Scheduling results when link resources are sufficient
[0142] Assume that two sessions need to be provided at the same time, and the hop count requirements of the two sessions are 2 and 3 respectively. The packet generation rate of both sessions is 8, and there are 10 available links in the network, among which links 1, 2, 3, 4, 5, and 6 are internal links, and links 7, 8, 9, and 10 are external links. link between.
[0143] The result is as Figure 7 As shown, we can get similar results as Figure 7 a map of and Figure 7 As shown in Figure b, the link is activated 17 times in session 1, and the link is activated 24 times in session 2. Since the minimum hop count requirements are 2 and 3 respectively, and the packet generation rate is 8, they all meet the minimum hop count of the link. constraint. Depend on Figure 7 It can be seen that in order to reduce delay and save costs, domestic links 1, 2, 3, 4, 5, and 6 are activated more times t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com