Vulnerability similarity measurement method based on context semantics
A technology of similarity measurement and context, applied in code semantic understanding in the field of software engineering and software engineering, can solve the problems of high false positive rate of static vulnerability detection tools, long time-consuming, high cost of pure manual screening, etc., to maintain structural invariance, Effect of High Accuracy, High False Positive Review Service
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
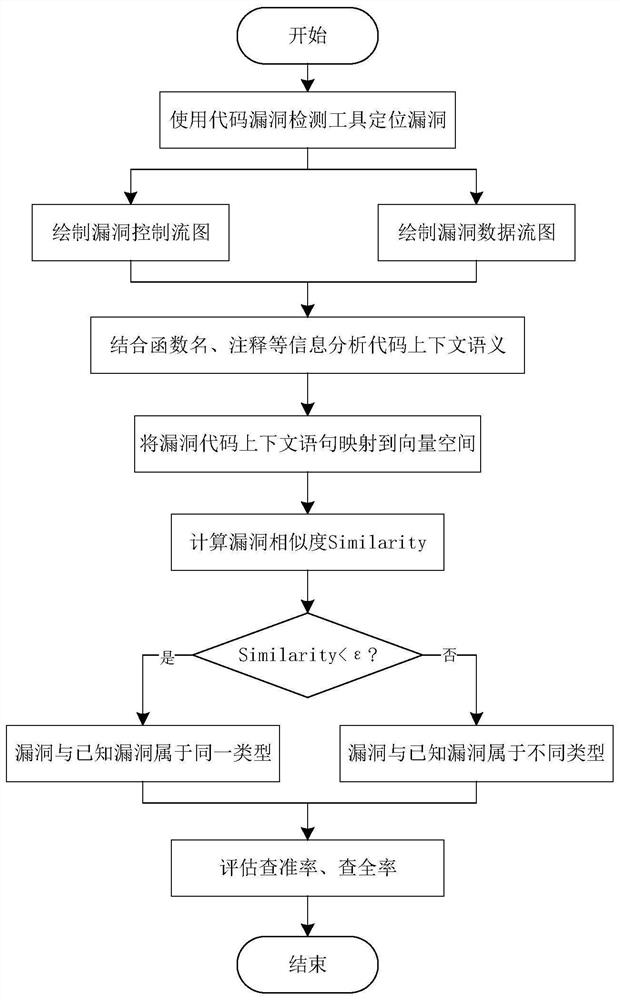
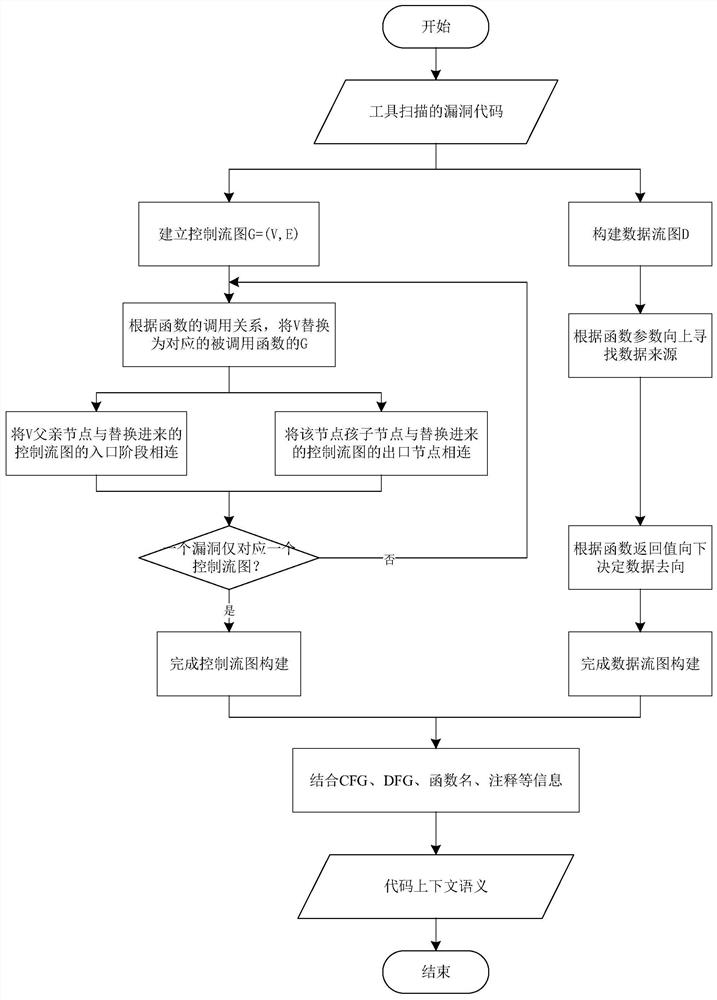
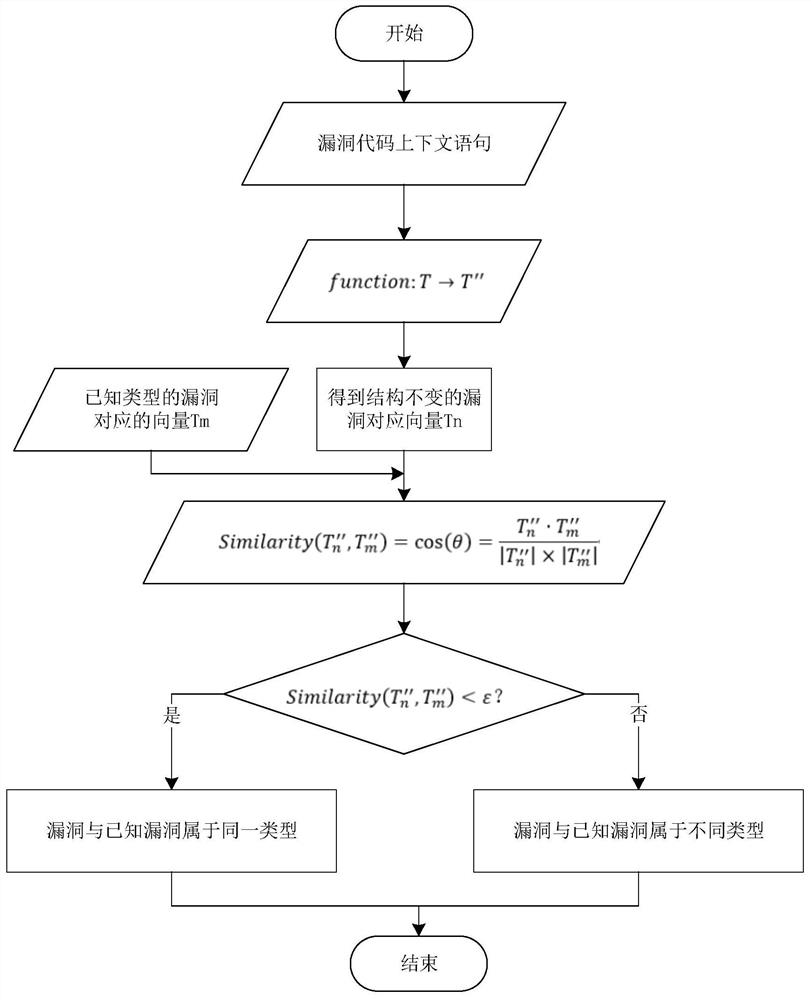
[0028] Several key technologies involved in the present invention are WALA tool, CFG, DFG, word2vec model.
[0029] 1. WALA tool
[0030] WALA is mainly used for static code analysis of Java and JavaScript, based on context-sensitive slices. In the present invention, the WALA tool is used to extract the control flow graph in the program, and according to the program data flow graph, the statement or predicate related to the code is located to assist in the semantic analysis of the code context.
[0031] 2. CFG
[0032] CFG is the Control Flow Graph, which represents all the paths traversed during the execution of a program. It expresses the possible flow of all basic block execution in a process in the form of a graph, and can also reflect the real-time execution process of a process. In the present invention, it is used to assist in building DFG and analyzing code context.
[0033] 3. DFG
[0034] DFG is a data flow graph, which describes a system from the perspective of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com