A non-intrusive smart speaker security forensics system and method thereof
A smart speaker, non-invasive technology, applied in transmission systems, digital transmission systems, security communication devices, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
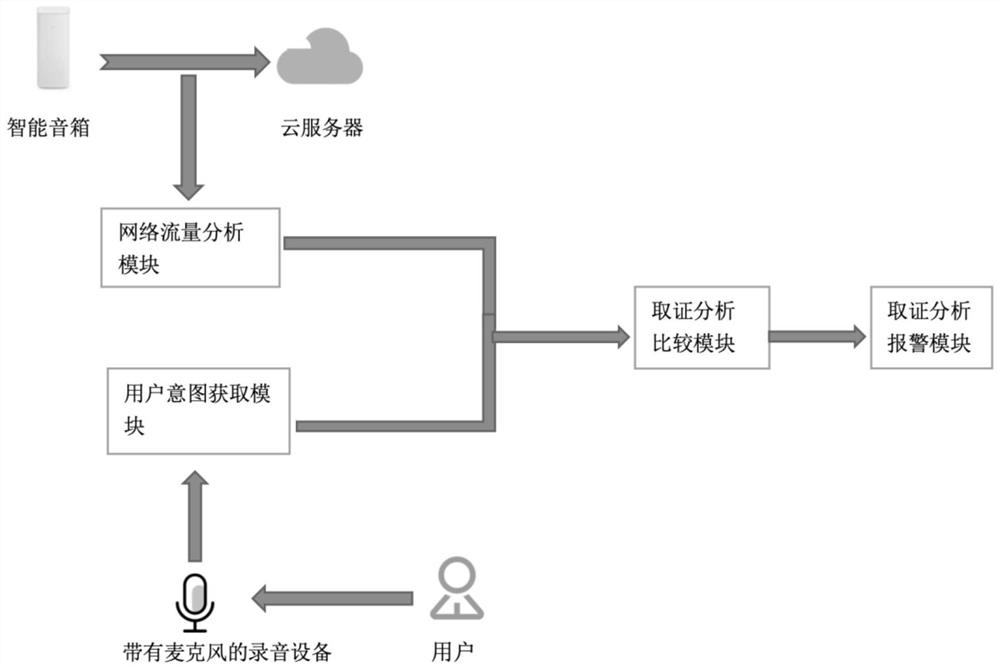
[0046] Embodiment 1: see figure 1 , a non-intrusive security forensics system for smart speakers, including a network traffic analysis module, a user intent acquisition module, and a forensic analysis module; the network traffic analysis module and the user intent acquisition module jointly provide convenience for the forensic analysis module.
[0047] The network traffic analysis module is used to monitor the network traffic between the smart speaker and the cloud server and analyze the network mode;
[0048] The user intention acquisition module is used to determine the intention of the user, that is, the operation that the user wants the smart speaker to perform;
[0049] The forensic analysis module is combined with the network traffic analysis module and the user intention acquisition module to monitor smart speaker events and collect relevant forensic relationships.
[0050] The forensic analysis module includes a comparison module between instructions and user intentio...
Embodiment 2
[0053] Example 2: see Figure 1-Figure 3 , a non-intrusive evidence collection method for a smart speaker security forensics system, the method includes the following steps:
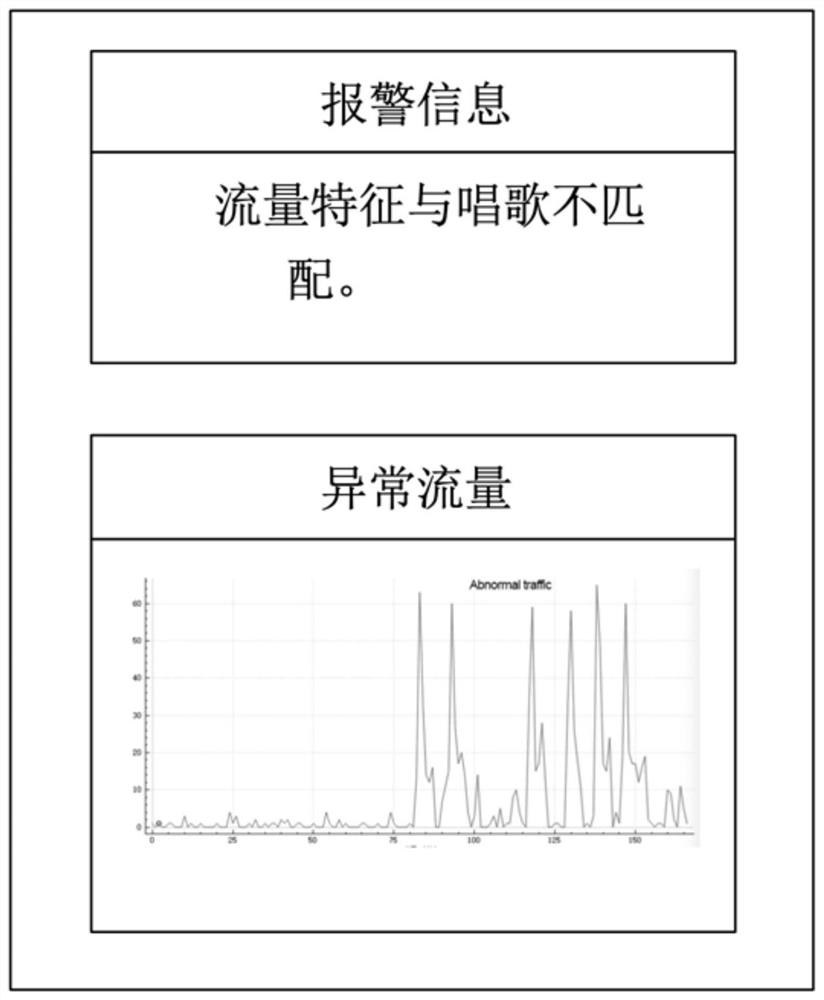
[0054] Step 1. In the stage of analyzing network traffic, a man-in-the-middle method is used to use a device with ARP spoofing software to act as a middleman to capture all network packets between the smart speaker and the cloud server. According to the captured network data packets, the network mode is extracted, and the current events of the smart speaker are deduced. Then, use the inferred events to determine whether the network traffic is consistent with the user's command and whether the smart speaker is recording the user's voice in real time;
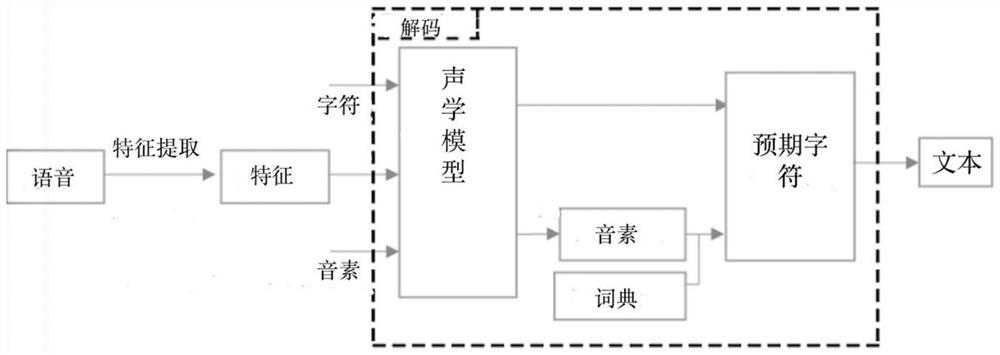
[0055] Step 2, user intent extraction stage, using a recording device with a microphone to record the conversation between the smart speaker and the user. The user's voice is converted into text in real time, and the user's intention is extracted from the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com