Medical purpose neural network robustness verification method and system based on shell protection
A robustness verification and neural network technology, applied in the field of neural network robustness verification for medical purposes, can solve the lack of methods and systems for neural network robustness verification, to improve robustness and reduce time complexity , the effect of improving operating efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0048] This embodiment provides a method for verifying the robustness of the neural network for medical use based on shell preservation;
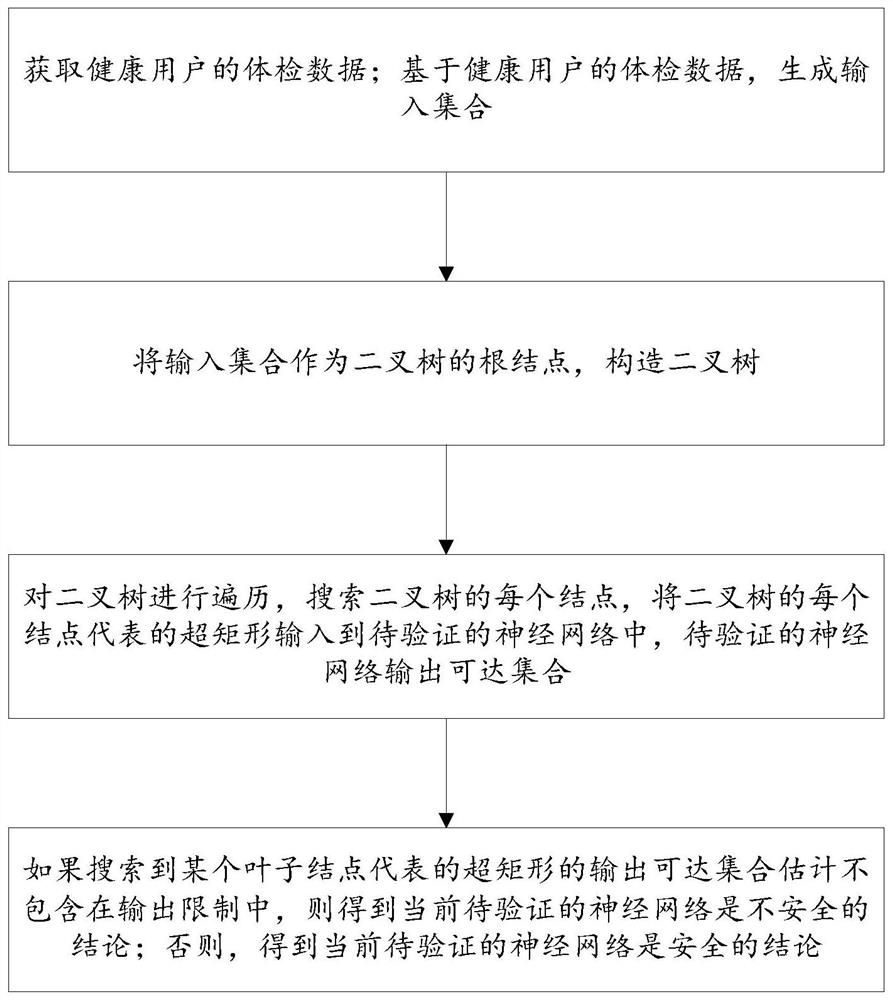
[0049] Such as figure 1 As shown, the robustness verification method of neural network for medical use based on shell preservation includes:
[0050] S101: Obtain physical examination data of healthy users; generate an input set based on the physical examination data of healthy users;
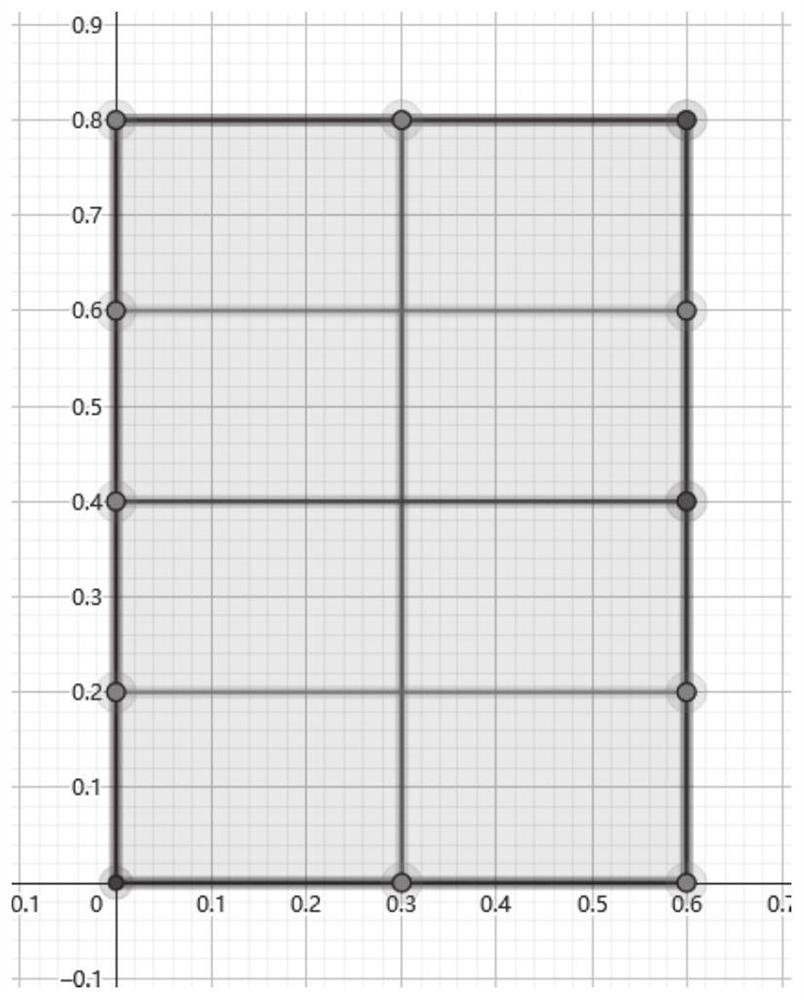
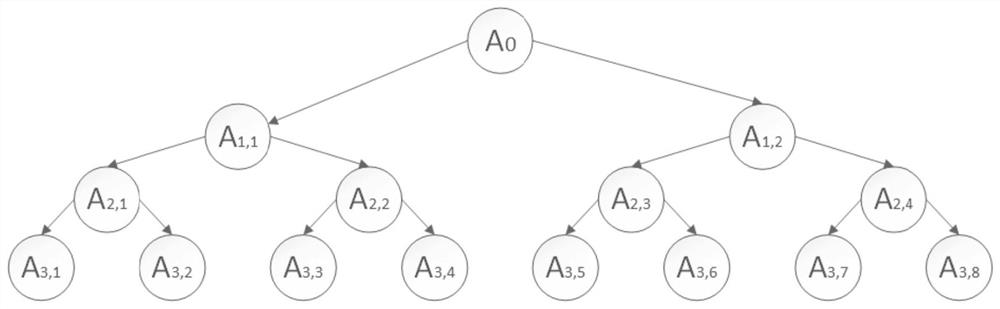
[0051] S102: Take the input set as the root node of the binary tree, each layer node is obtained by bisecting the super rectangle represented by its parent node, until the super rectangle represented by a certain layer node reaches the specified size limit, then no Continue to bisect, the current layer node is the leaf node, and obtain the binary tree for searching;
[0052] S103: Traverse the binary tree, search each node of the binary tree, input the hyperrectangle represented by each node of the binary tree into the neural network to be verified, and th...
Embodiment 2
[0174] This embodiment provides a robustness verification system for medical use neural networks based on shell preservation;
[0175] The robustness verification system of neural network for medical use based on shell preservation, including:
[0176] The input set generation module is configured to: acquire the physical examination data of the healthy user; generate the input set based on the physical examination data of the healthy user;
[0177] Binary tree construction module, which is configured to: use the input set as the root node of the binary tree, each layer of nodes is obtained by bisecting the super rectangle represented by its parent node, until the super rectangle represented by a certain layer of nodes reaches The specified size limit, then do not continue to bisect, the current layer node is the leaf node, and the binary tree for searching is obtained;
[0178] The security verification module is configured to: traverse the binary tree, search each node of t...
Embodiment 3
[0183]This embodiment also provides an electronic device, including: one or more processors, one or more memories, and one or more computer programs; wherein, the processor is connected to the memory, and the one or more computer programs are programmed Stored in the memory, when the electronic device is running, the processor executes one or more computer programs stored in the memory, so that the electronic device executes the method described in Embodiment 1 above.
[0184] It should be understood that in this embodiment, the processor can be a central processing unit CPU, and the processor can also be other general-purpose processors, digital signal processors DSP, application specific integrated circuits ASIC, off-the-shelf programmable gate array FPGA or other programmable logic devices , discrete gate or transistor logic devices, discrete hardware components, etc. A general-purpose processor may be a microprocessor, or the processor may be any conventional processor, or...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com