Carrier-free steganography method and system based on blockchain private key mapping
A block chain and private key technology, applied in the field of computer information hiding, can solve the problems that the carrier is modified in the channel transmission, the cost of resource search is large, and the efficiency of information transmission is poor.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] Below in conjunction with accompanying drawing, the present invention will be further described through embodiment.
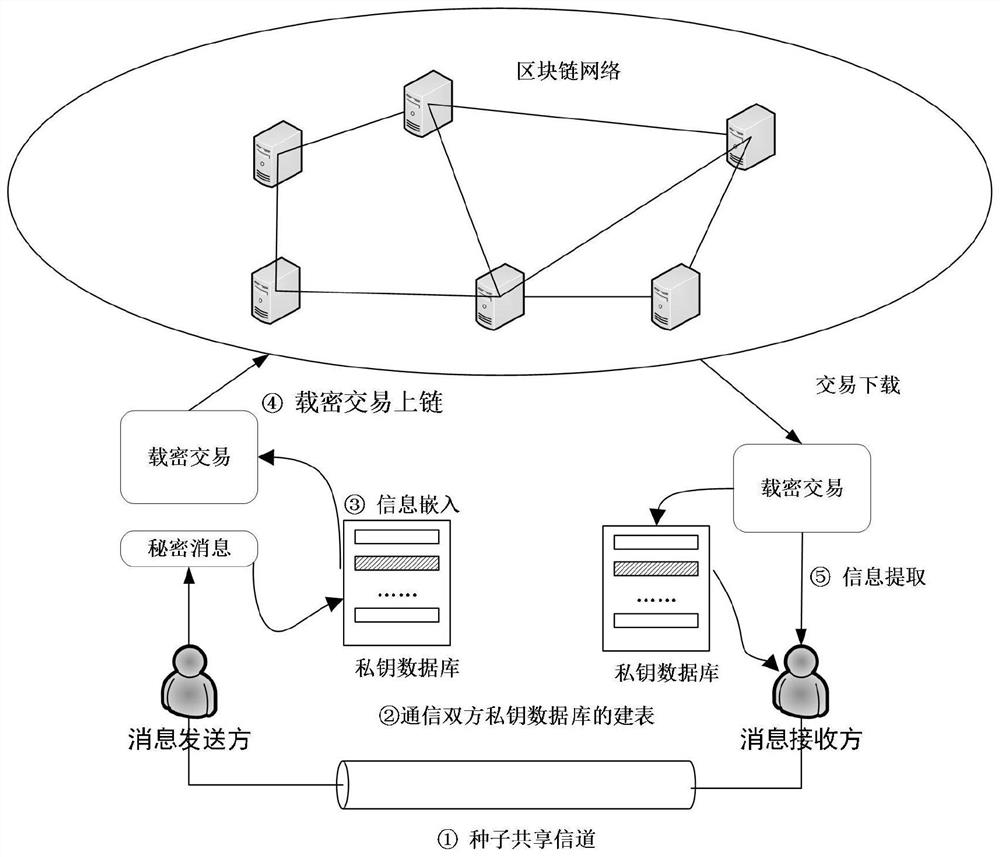
[0044] A carrierless covert communication scheme based on block chain private key mapping of the present invention comprises the following steps:
[0045] Step 1: Seed sharing: Both parties in the communication pre-generate random number seeds and communicate a unified random number generation algorithm;
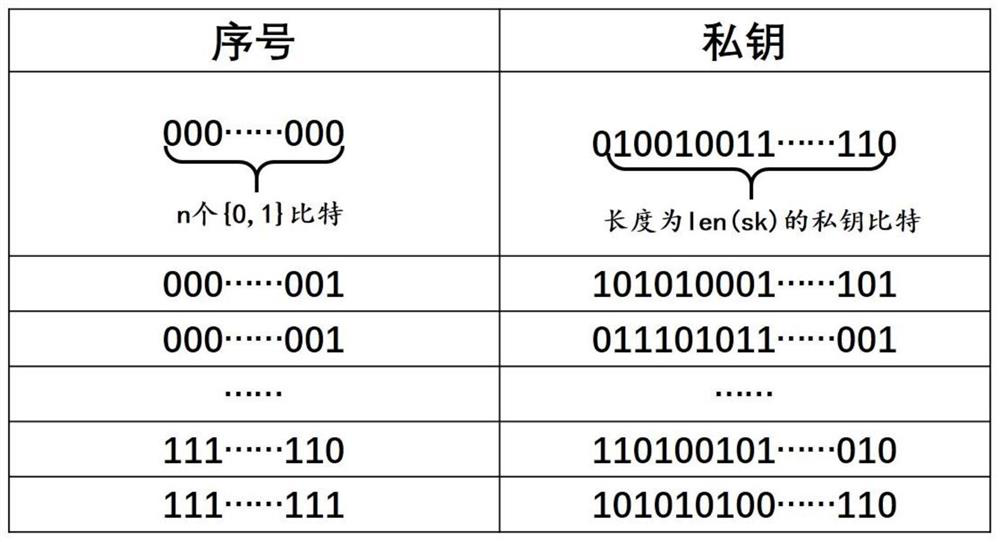
[0046] Step 2: Create a table of the private key database: the two parties establish a private key database in a certain communication, and obtain the one-to-one mapping between the secret message and the private key through the serial number;
[0047] Step 3: Information embedding: The message sender selects the corresponding private key in the private key database according to the secret message;
[0048] Step 4: Confidential transactions on the chain: The message sender obtains the corresponding public key of the selected private key through the bl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com