High-security identity authentication system
An identity authentication, electronic ID card technology, applied in the direction of digital data authentication, instrument, character and pattern recognition, etc., can solve the problems of high verification cost, property security threat, easy forgery, etc., to achieve accurate results, safe data storage, authoritative reliable results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
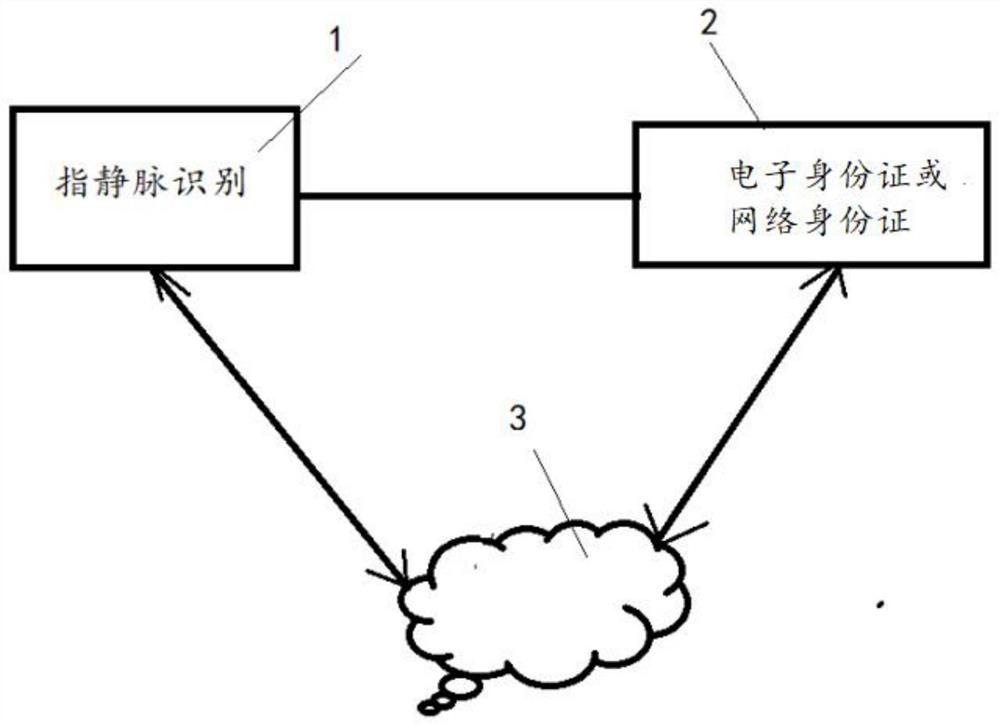
[0012] See figure 1 , a highly secure identity authentication system of the present invention, which includes a hand vein feature collection and identification system 1, an electronic ID card or a network ID card system 2 of the Ministry of Public Security, and the hand vein feature data is stored in one-to-one correspondence with the data of the Ministry of Public Security In the blockchain system 3, during the authentication process, the data obtained and verified by the hand vein feature recognition system is guaranteed to be the person’s living body, and the pre-collected and retained data of the Ministry of Public Security is used for authentication to ensure authority and reliability. .
[0013] In the high-security identity authentication system, the vein characteristics of the hand include but not limited to the vein characteristics of the fingers, the center of the palm or the back of the palm.
[0014] In the highly secure identity authentication system, the block c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com