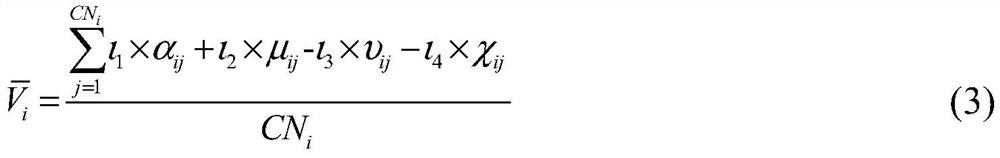A Consensus Method for Internet of Vehicles Node Consensus Based on Malicious Node Attack Detection
A malicious node and car networking technology, applied in the blockchain field, can solve the problems of high communication delay of asynchronous network nodes, no consideration of network dynamic changes, malicious node detection, etc., to improve transaction throughput, efficient detection and defense, The effect of improving consensus efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
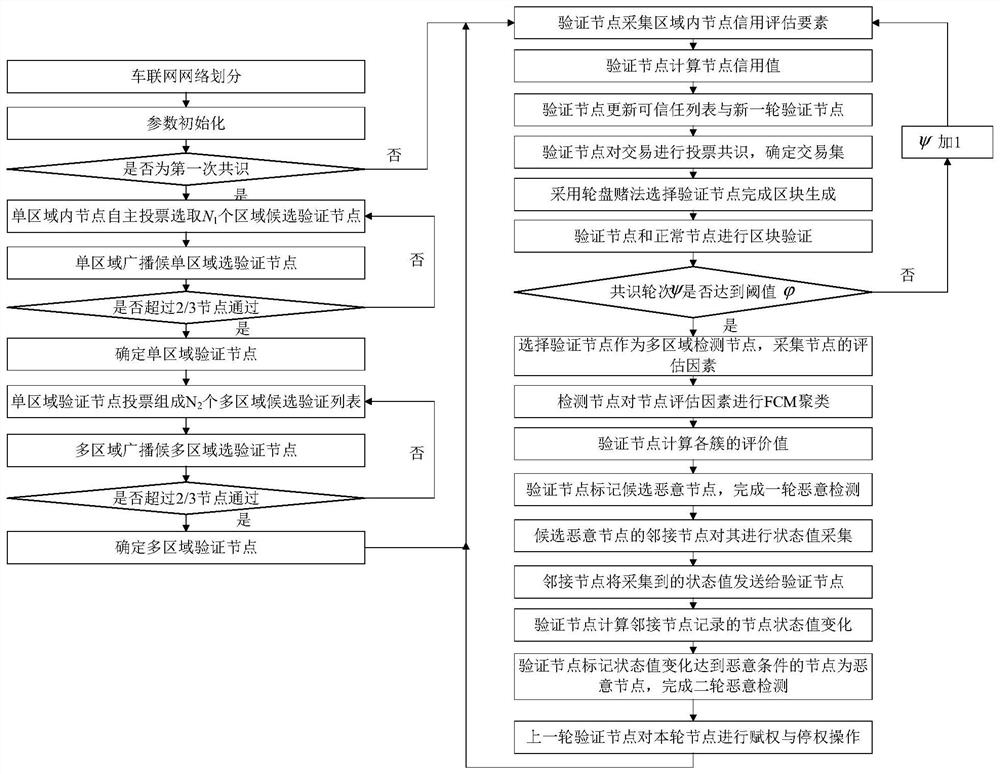
[0064] As shown in Figure 1, the present invention provides a consensus consensus method based on malicious node attack detection of IoV nodes
[0070] Step 4: Determine single-area and multi-area verification nodes through node voting; wherein,
[0076] Step 5: Verify that the node collects the credit value evaluation elements of each node in the area, and determines a trusted list; wherein,
[0077] The method for determining the trusted list specifically includes:
[0079] sc
[0085] Step 7: The verification node conducts voting consensus on the transaction in the network, and determines the transaction set; wherein,
[0086] The method for determining the transaction set specifically includes:
[0087] S7.1, each verification node continuously receives the transaction sent from the network, by verifying with the local ledger data
[0088] S7.2, after the verification node receives the transaction proposal approved by other verification nodes, it enters into the transaction can...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com