A privacy protection method and system based on cloud-edge-end edge computing system
An edge computing and privacy protection technology, which is applied in computing, digital data protection, computer security devices, etc., can solve the problems of not considering the privacy leakage, the inability to obtain high-precision models, and the complexity of the design of the three-tier incentive mechanism. Accelerate the task process, improve efficiency, and achieve low network latency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
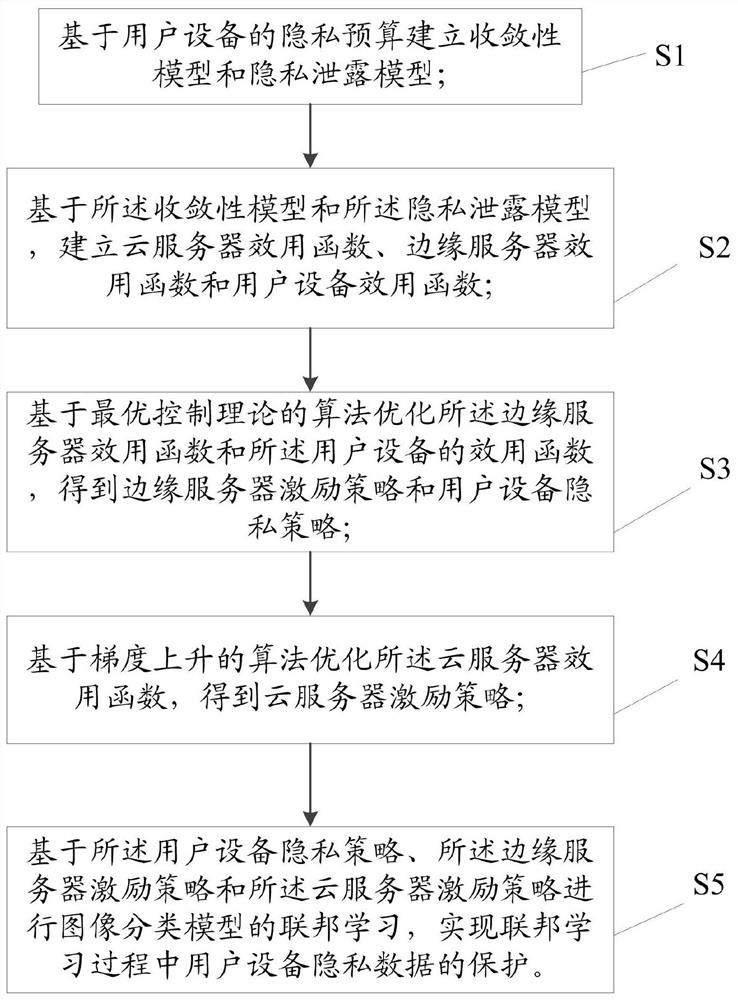
[0031] See figure 1 This embodiment provides a privacy protection method based on federal learning cloud-edge-ended edge computing system, including:
[0032] Step S1: Establish convergence model and privacy leakage model based on the privacy budget of user equipment;
[0033] The convergence model is:
[0034] Among them, λ 1 Λ 2 Λ 3 All are constants; ε i ( i.j ) Represents the privacy budget of JU JU Equipment under the i-th edge server; n represents the number of user equipment;
[0035] The privacy leakage model is:
[0036] Among them, B 1 , B 2 , C is constant; L represents the maximum value of the image classification model parameters on the user equipment; T represents the number of integrations of the image classification model on the user equipment; D represents the local image classification data set size.
[0037] Step S2: Based on the convergence model and the privacy leakage model, establish a function of cloud server utility, edge server utility functions, and us...
Embodiment 2
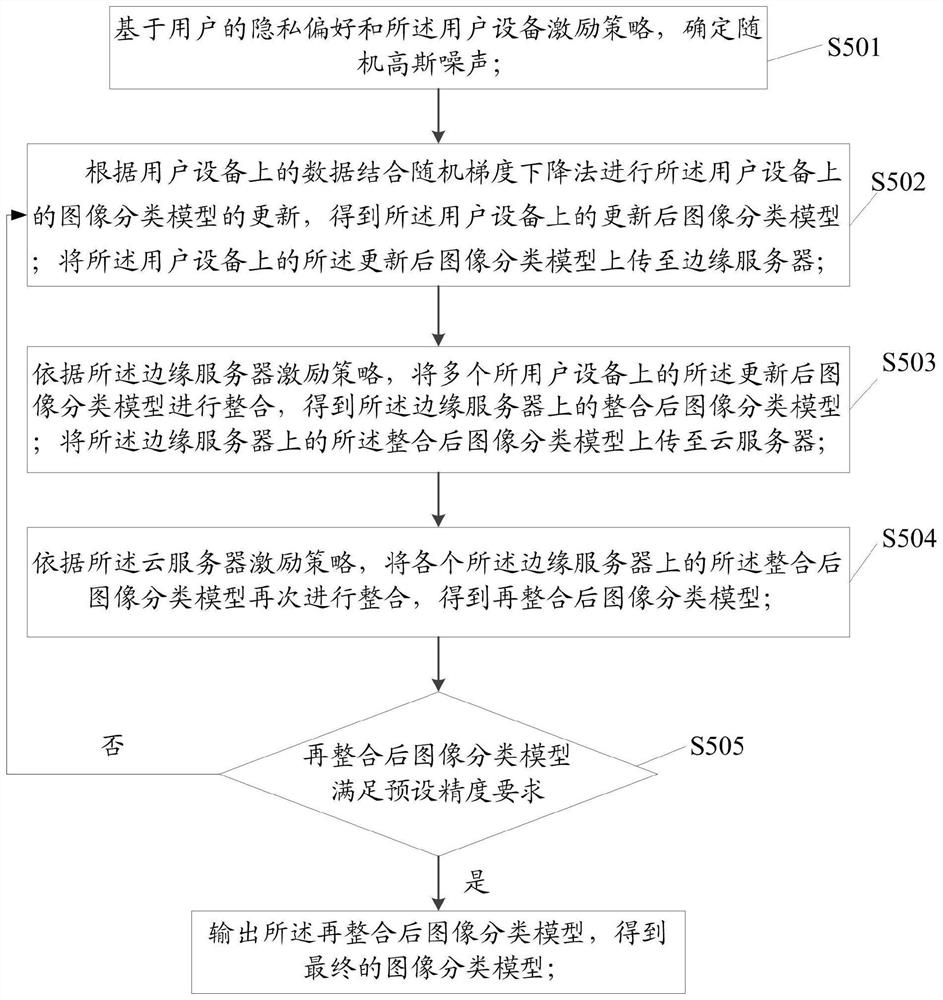
[0081] See Figure 5 This embodiment provides a privacy protection system based on federal learning cloud-edge-end calculation system, including:
[0082] Model establishment module M1, used to establish convergence models and privacy leakage models based on user equipment;
[0083] Utility function establishment module M2 for establishing a cloud server utility function, edge server utility function, and user equipment effect function based on the convergence model and the privacy leakage model;
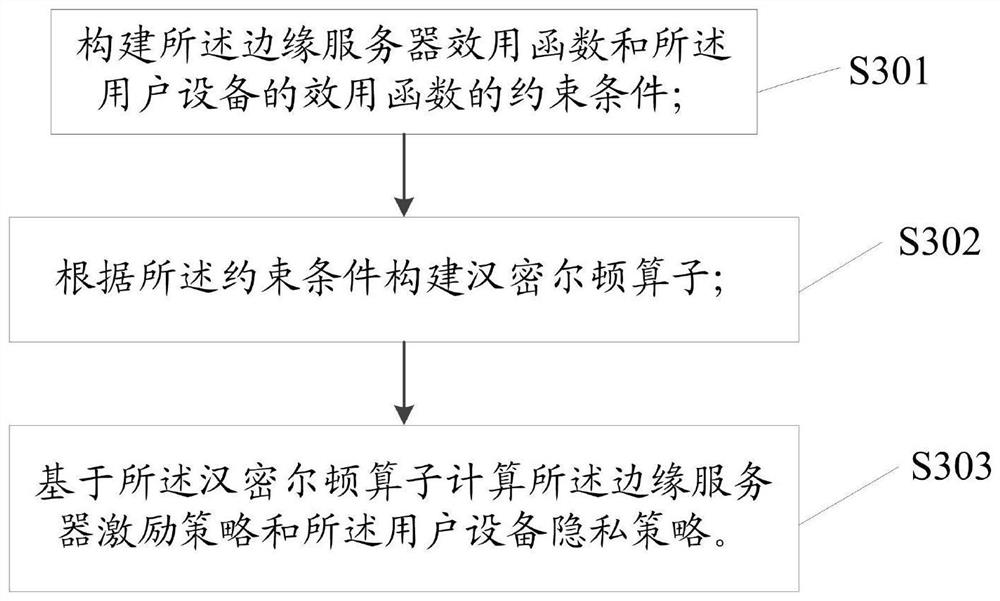
[0084] Policy Design Module M3, an algorithm based on optimal control theory, optimizing the edge server utility function and the utility function of the user equipment, resulting in edge server excitation policies and user equipment privacy policies; based on gradient rising algorithm optimization said cloud Server utility function, get cloud server incentive strategy;
[0085] Federal learning module M4, is used to implement image classification models based on the user equipment priva...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com