Method for preventing replay attack of API (Application Program Interface)
An API interface and replay attack technology, which is applied in the computer field, can solve the problems of increased server burden and consumption, and achieve the effects of accurately identifying replay attacks, reducing overhead, and reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
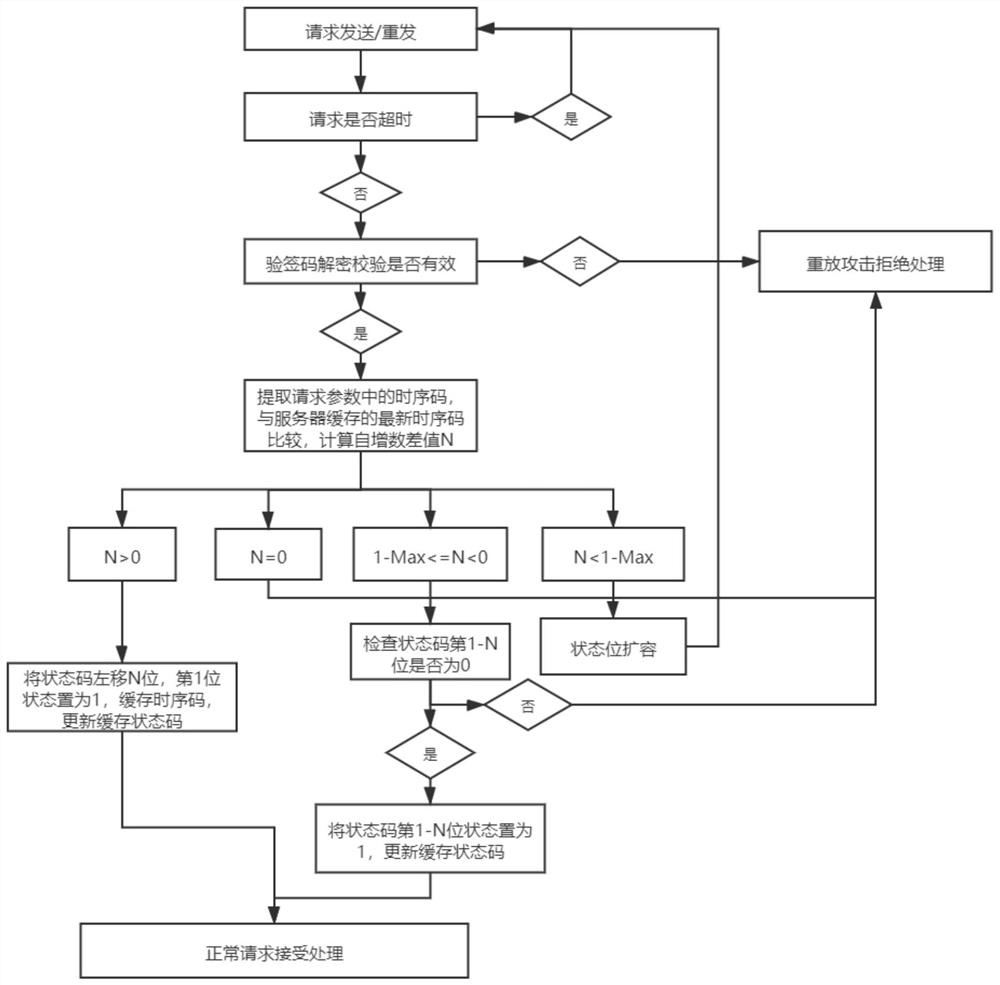
[0030] The specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings:
[0031] A method for preventing replay attacks by an API interface, characterized in that: it is characterized in that it comprises the following steps:
[0032] Step 1: When making an interface request, calibrate the time stamp of the requesting end and the server time, and calculate the difference for the requesting end to calibrate to ensure that the time of the requesting end and the server time are basically synchronized;
[0033] Step 2: Set the timeout time of the interface according to the http request framework of the requester, usually take 30 seconds as an example, the interface request time is t1, the current server time is t2, if t1>t2, it is a request with illegal parameters, if t2-t1 >=30 seconds, the interface times out, and requests from illegal interfaces and time-out interfaces are rejected. When t2-t1<30 seconds, it is con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com