Low-memory-occupancy implementation technology based on post quantum cryptography Saber algorithm
A quantum cryptography, low-memory technology, applied in the field of low-memory-occupancy key generation, can solve problems such as large memory usage and hinder deployment, and achieve the effect of reducing memory usage, low memory usage, deployment difficulty and deployment cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
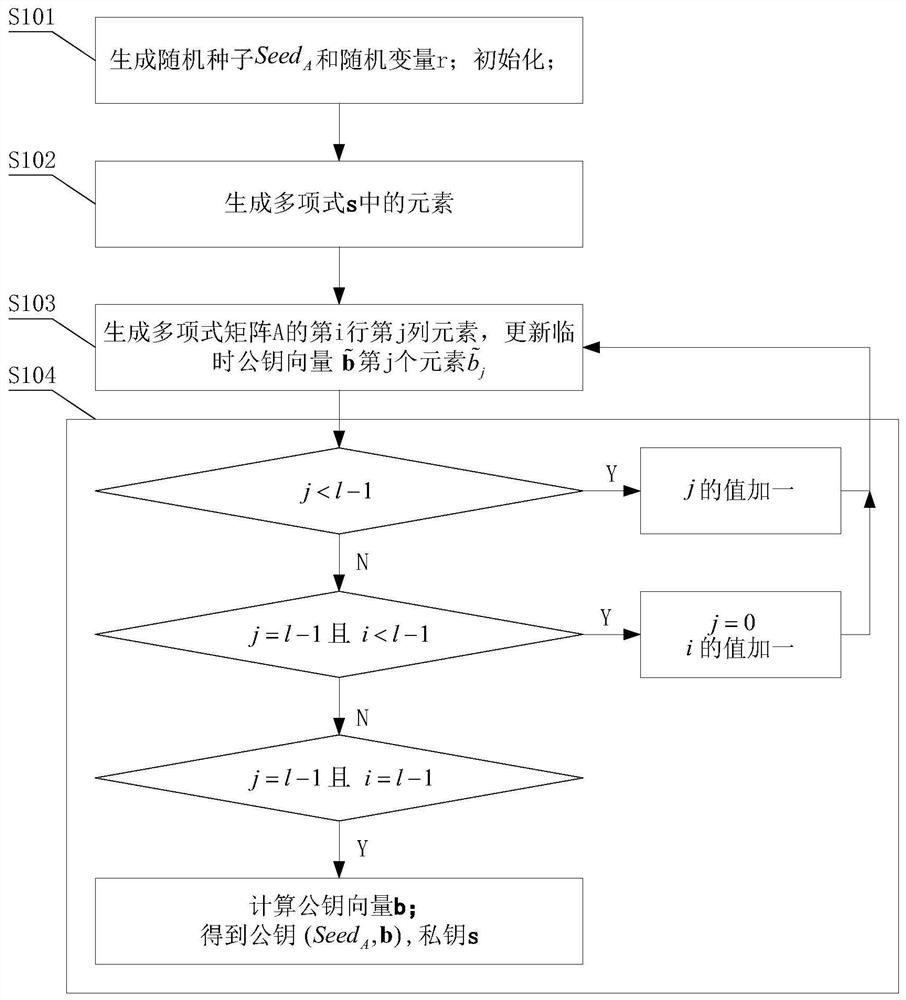
[0073] This embodiment discloses a method for generating a key with low memory occupation based on the post-quantum cryptography Saber algorithm, such as figure 1 shown, including:
[0074] S101. Generate a random seed Seed A and random variable r; initialize the index i=0, j=0 of the polynomial matrix A, and initialize the temporary public key vector All elements are 0;
[0075] Random seed Seed in this embodiment A The length of and r are both 256bits, that is, 32 bytes, where each bit is uniformly randomly selected from 0 and 1;
[0076] Step S101 only initializes the index of A, but does not allocate the space occupied by A.
[0077] S102. Generate a plurality of pseudorandom numbers according to the random variable r, and store them in the first storage unit; the size of the first storage unit is greater than or equal to the space occupied by the pseudorandom numbers corresponding to the polynomial coefficients of all elements in the polynomial vector s Space size; ...
Embodiment 2
[0103] The difference between this embodiment and Embodiment 1 is that the pseudo-random numbers corresponding to the polynomial coefficients of the elements in the polynomial vector s are generated in real time, specifically:
[0104] In the step S102, a plurality of pseudo-random numbers corresponding to the polynomial coefficients of the ith element of the polynomial vector s are first generated according to the random variable r, and stored in the third storage unit, and the space size of the third storage unit is greater than or equal to The size of the space occupied by the pseudo-random number corresponding to the polynomial coefficient of an element in the polynomial vector s; generate the i-th element s of the polynomial vector s according to the pseudo-random number in the third storage unit i ;
[0105] In this embodiment, the space size of the third storage unit is set to 256 Bytes. First, use the random variable r as an input to call the absorb() function once to...
Embodiment 3
[0109] This embodiment is an improvement made on the basis of Embodiment 2. The difference from Embodiment 2 is that the third storage unit is divided into two parts, one of which is used to store unused pseudo-random numbers and generate the next element Use, thereby reducing the discarding of data and reducing the number of calls of the squeezeblock() function. Specifically:
[0110] The space size of the third storage unit is equal to the space occupied by the pseudo-random number corresponding to the polynomial coefficient of an element in the polynomial vector s;
[0111] The third storage unit is divided into a first subunit and a second subunit, and the space size of the first subunit is the space occupied by the pseudo-random number generated by calling the pseudo-random number generation function once;
[0112] When generating the values of the elements in the polynomial vector s:
[0113] If there is a pseudo-random number in the second subunit, extract the pseud...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com