Lightweight security authentication method and device based on device fingerprint and PUF
A device fingerprint and security authentication technology, applied in the field of security authentication and the Internet of Things, can solve the problems of vulnerability to physical attacks and cloning attacks, spoofing RSSI values, secret leakage, etc., achieve low energy and silicon area, realize privacy protection, realize Effects of Restoration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0064] Device Registration: Store initial CRP for each edge IoT device (C i , R i ) and false identification (SID i ), C i Denotes the query of the i-th iteration, R i Indicates that the current C i The response of the PUF, SID i Indicates the anonymous ID of the IoT device of the i-th iteration. For each edge IoT device, the server also stores an emergency CRP list (C em ) and an emergency identification list EID to mitigate DoS attacks. The initial parameters are obtained by the server using a time-based one-time password algorithm (TOTP) and by the operator using a password. Each edge IoT device stores C i 、SID i 、C em and EID. Also we assume that device management and connection management have a pre-shared secret symmetric key k GS .
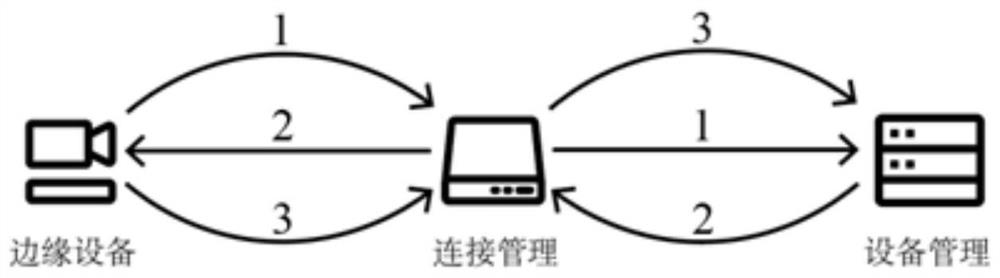
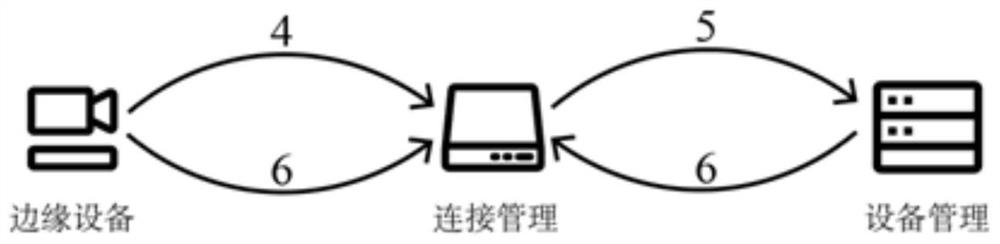
[0065] An embodiment of the present invention provides a lightweight security authentication method based on device fingerprints and PUF, such as figure 2 shown, including the following steps:
[0066] Edge IoT devices gener...
Embodiment 2
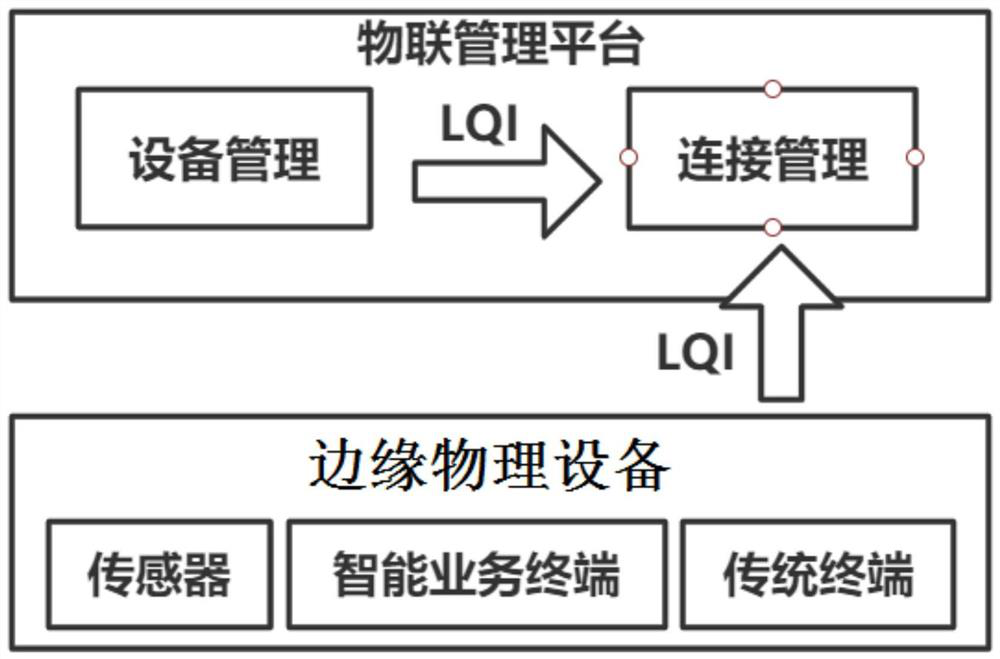
[0115] An embodiment of the present invention provides a lightweight security authentication device based on device fingerprints and PUF, such as figure 1 As shown, including: sequentially connected edge IoT devices, connection management and device management;
[0116] Edge IoT devices generate random noise N 1 , and combined with its PUF to generate the secret response R i generate message in, Indicates a false identity; the secret response R i The specific generation process is: edge IoT device ID A Query C using stored i-th iteration i and its PUF to generate the secret response R i ;
[0117] Edge IoT devices based on the message Generating Authentication Parameters I 0 =H(M 0 ||R i ), H is the hash function, and the message and authentication parameters I 0 =H(M 0 ||R i ) is sent to the device management;
[0118] Device management based on received messages Calculate the hash value I 0 ', if I 0 'with I 0 are equal, generate a random noise N 2 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com