Secret SM9 algorithm private key distribution method, user terminal and key generation center
A key generation center and user terminal technology, applied in the field of information security, can solve the problems of cryptographic system failure, unpublished private key security application distribution process, etc., and achieve the effect of ensuring integrity and security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
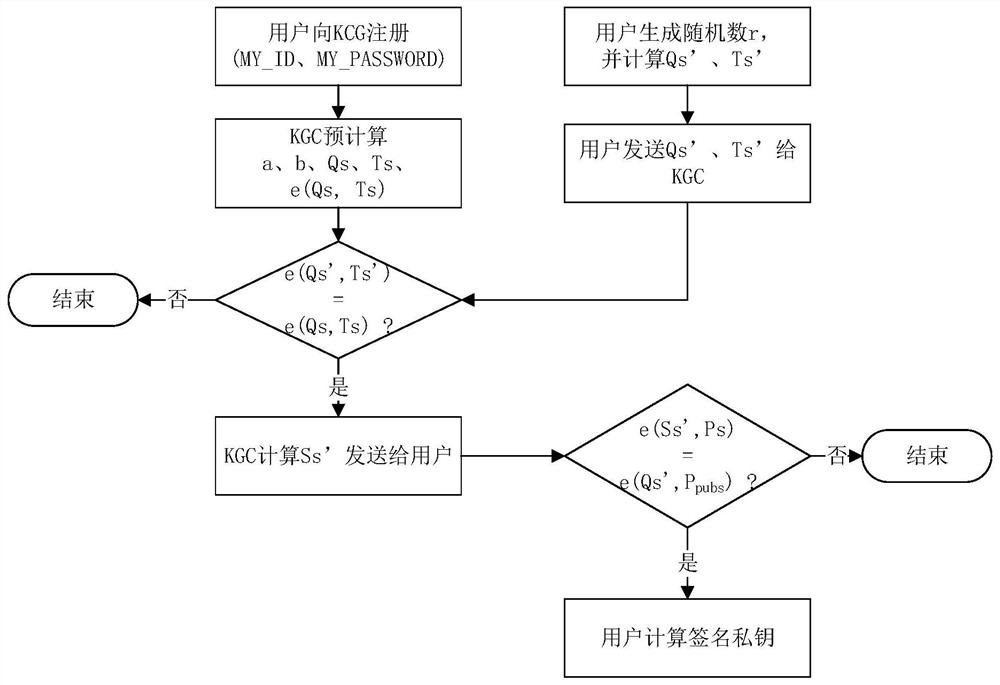
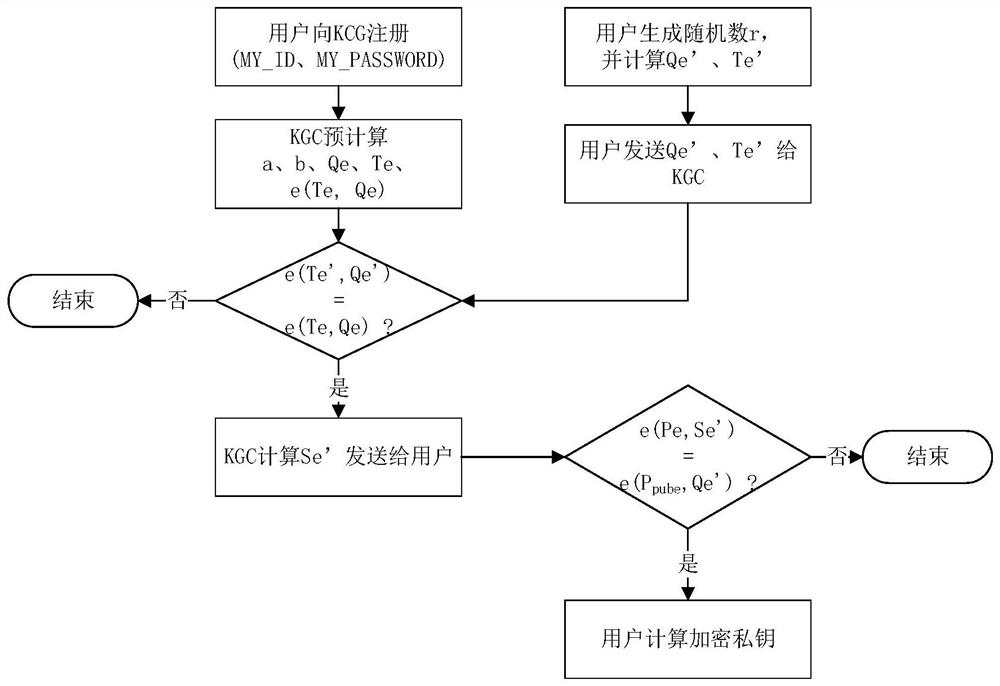
[0093] It is known in the prior art that the user's private key is generated by the key generation center KGC, and the private key is sent to the user online by the KGC. Since the private key is distributed through an untrusted public network, in order to avoid leakage of the private key, the present invention transmits the private key during the transmission process. Based on the elliptic curve discrete logarithm operation, the intermediate private key parameters are calculated using the private key factor to ensure that only the user can restore the private key from the private key parameters, and both parties have added the necessary integrity verification.
[0094] Since the method of generating the user signature private key and the encrypted private key of the SM9 algorithm is not exactly the same, the private key distribution process also needs to be treated differently. The method steps described in the present invention propose their own calculation steps for the two to...
Embodiment 2
[0148] Based on the same inventive concept as the method in Embodiment 1, a user terminal for distributing the private key of the national secret SM9 algorithm of the present invention includes:
[0149] The user registration module is used to register with the key generation center KGC and set a user password to generate corresponding user parameters;
[0150] The private key application module is used to calculate the verification parameters for private key application based on random numbers and user parameters, and send the verification parameters to KGC;
[0151] The private key receiving module is used to receive the private key parameters sent by KGC;
[0152] The private key calculation module is used to verify the private key parameters, and if the verification is correct, the private key is calculated based on the private key parameters.
[0153] The present invention also provides a key generation center for the private key distribution of the national secret SM9 a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com