Data migration method for encrypted database
A database and data technology, applied in the field of data migration of encrypted databases, can solve problems such as affecting user usage, slow data migration and transmission, and long downtime, so as to reduce wasted transmission time, improve data migration speed, and reduce user loss. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
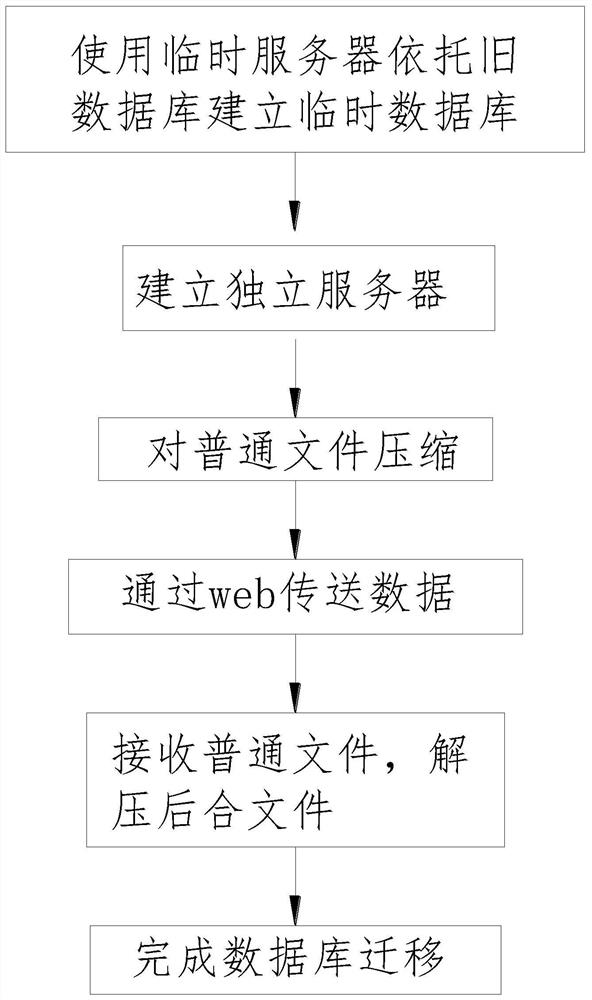
[0038] see figure 2 , a kind of data migration method for encrypted database, the data migration method of described encrypted database comprises the following steps:
[0039] (1) Use a temporary server to build a temporary database based on the old database, and switch the old server to run on the temporary server.
[0040] (2) Establish an independent server, divide common files into data, obtain several common file packages, and use the data comparison module to generate a comparison directory.
[0041] (3) Send several ordinary file packages to the storage unit in the new server through the web, and use the splicing module to splice the several ordinary file packages into an integrated file.
[0042] (4) When using the import module to import the complete file into the new database, use the update module to import the temporary file in the temporary database into the new database to complete the data migration of the encrypted database.
[0043] Specifically, in the ste...
Embodiment 2
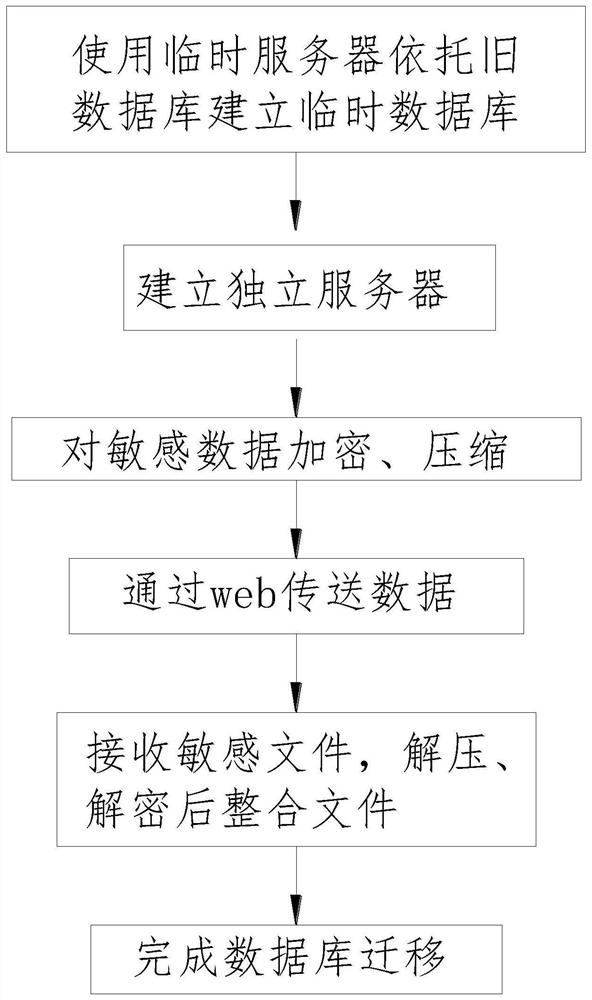
[0050] see image 3 , a kind of data migration method for encrypted database, the data migration method of described encrypted database comprises the following steps:
[0051] (1) Use a temporary server to build a temporary database based on the old database, and switch the old server to run on the temporary server.
[0052] (2) Establish an independent server, divide the data of sensitive data files, obtain several sensitive data packets, and use the data comparison module to generate a comparison directory. Sensitive data refers to data that may cause serious harm to society or individuals after leakage, including Personal privacy data, such as name, ID number, address, telephone number, bank account number, email address, password, medical information, educational background, etc., also includes data that is not suitable for publication by enterprises or social institutions, such as the business situation of the enterprise, the network of the enterprise structure, list of IP...
Embodiment 3
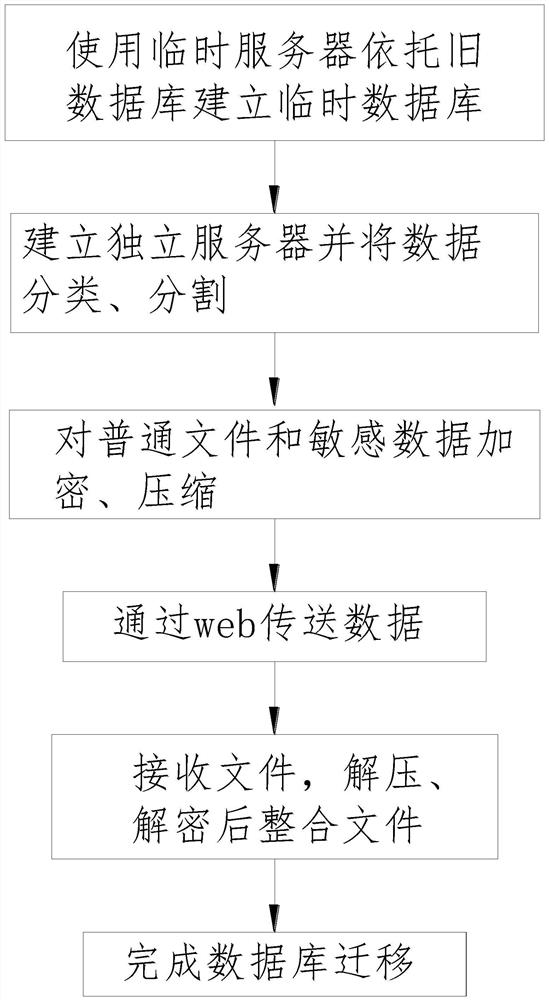
[0094] see figure 1 , a kind of data migration method for encrypted database, the data migration method of described encrypted database comprises the following steps:
[0095] (1) Use a temporary server to build a temporary database based on the old database, and switch the old server to run on the temporary server.
[0096] (2) Establish an independent server to use the data segmentation module to classify the data information in the old database, classify the data information in the old database into ordinary files and sensitive data files, and divide the sensitive data files and ordinary files into data to obtain several sensitive files. For data packages and ordinary file packages, use the data comparison module to generate a comparison directory; sensitive data refers to data that may cause serious harm to society or individuals after leakage, including personal privacy data, such as name, ID number, address, phone number, Bank account numbers, email addresses, passwords...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com