Access control system and method for unstructured data in multi-tenant environment
An unstructured data and access control technology, applied in the field of data security, can solve the problems of inability to improve the access performance of large data capacity, high implementation cost, identity authentication and data desensitization, etc., to ensure high concurrency scenarios and guaranteed performance. Performance, guarantee high-speed effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
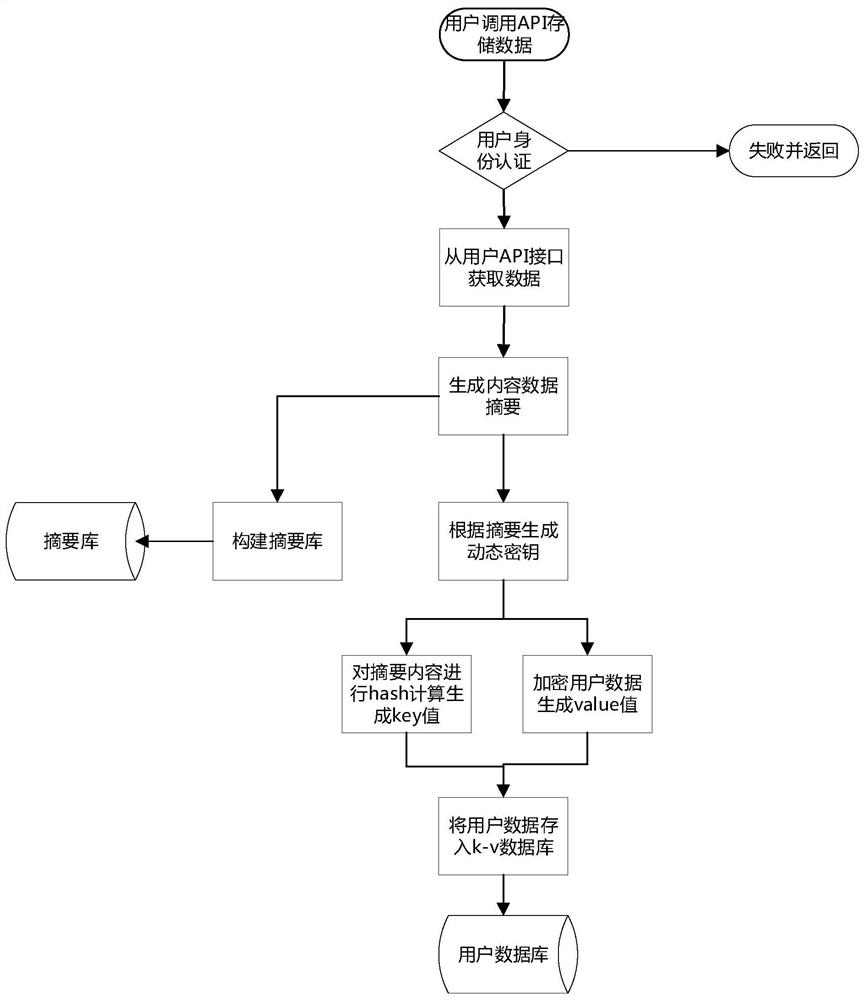
[0050] An access control method for unstructured data in a multi-tenant environment. Assuming that the user already has a CA certificate or has exchanged a public key with the server and has completed user registration, the user stores data according to the following steps:
[0051] 1. When a user initiates an unstructured data storage request, the user needs to submit data according to the API interface function setdata (username, password, timestamp, title, data, sign) set in the present invention, where username is the account name registered by the user , password is the encrypted value of the user's account password (encrypted with the user's private key), timestamp indicates the timestamp of the user's submitted data, title indicates the title of the user's data, data is the user's data object, that is, the original data submitted by the user, and sign is the user's unique logo. The sign value is the hash value of the user CA certificate or the user private key.
[0052...
Embodiment 2
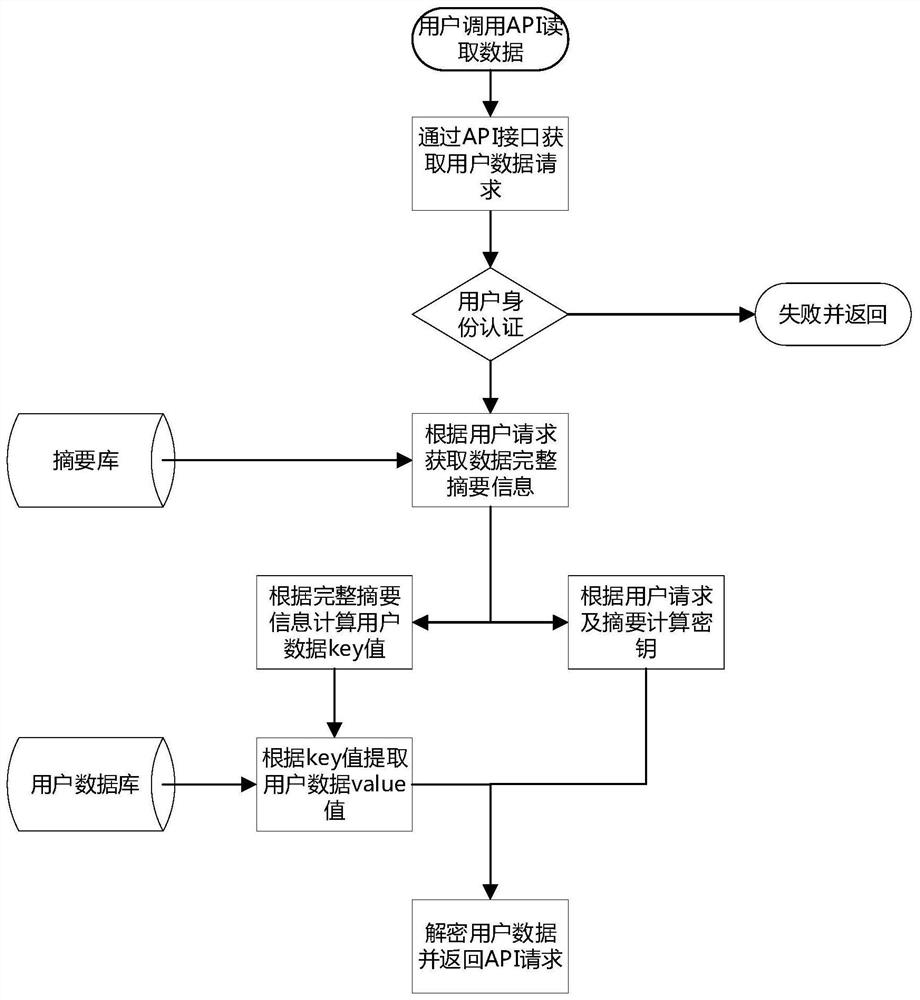
[0063] An access control system for unstructured data in a multi-tenant environment, including:
[0064] A user request acquisition module, configured to receive user data processing requests;
[0065] An identity authentication module, configured to perform user identity authentication based on user data processing requests;
[0066] A user data processing module, configured to process user data in response to passing user identity authentication;
[0067] The data processing module includes a user data storage module and a user data extraction module, and the user data processing request includes a user data storage request and a user data extraction request;
[0068] The user data storage request includes,
[0069] The data summary generation module is used to extract parameter information based on the user data storage request, generate data summary information and store it in the summary library;
[0070] A dynamic password generation module, configured to generate a d...
Embodiment 3
[0077] The embodiment of the present invention also provides an access control device for unstructured data in a multi-tenant environment, including a processor and a storage medium;
[0078] The storage medium is used to store instructions;
[0079] The processor is configured to operate according to the instructions to perform the steps of the following method:
[0080] Receive user data processing requests;
[0081] User identity authentication based on user data processing requests;
[0082] In response to passing user identity authentication, perform user data processing, including user data storage and user data extraction, the user data processing request includes user data storage request and user data extraction request, wherein:
[0083] The user data store includes:
[0084] Extract parameter information based on user data storage requests, generate data summary information and store it in the summary library;
[0085] Generate a dynamic password based on the da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com