Method for persisting data into memory database in request log form
A database and persistence technology, which is applied in the direction of data error detection, electrical digital data processing, special data processing applications, etc., can solve the problems of complex use, complex data relationship, and traditional database complexity.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
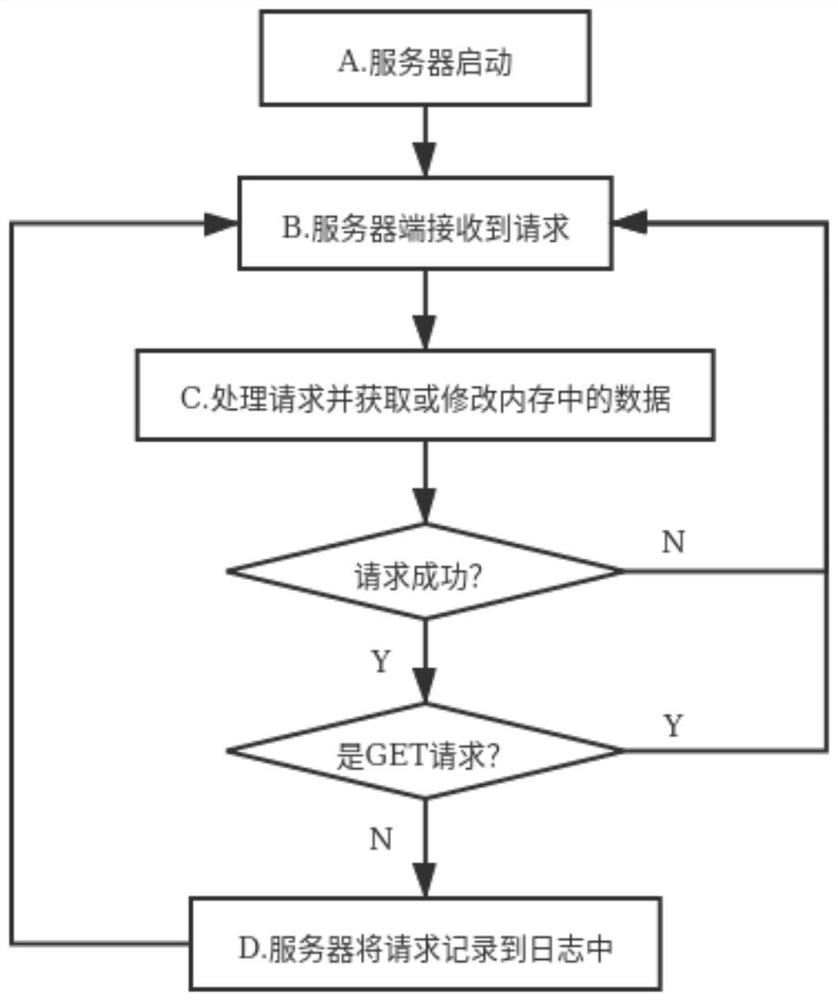
[0034] In a specific embodiment 1, such as figure 1 As shown, a method for persisting data to an in-memory database in the form of a request log includes the following steps,
[0035] A, Server startup; in this step the server starts running.
[0036] B. The server receives the client request;
[0037] C. The server side processes the request and obtains or modifies the data in the memory database; the server side processes the request sent by the client, and processing the request may need to obtain data from the memory database or modify the data in the memory database. If the request is unsuccessful, proceed to step B; if the request is a GET request, the data in the memory database has not been modified, and proceed to step B. If the request is successful and not a GET request, step D is performed.
[0038] D. The server side records the request in step C into a log.
[0039] The output result in this embodiment is a log file, which can be used for recovery of the memo...
Embodiment 2
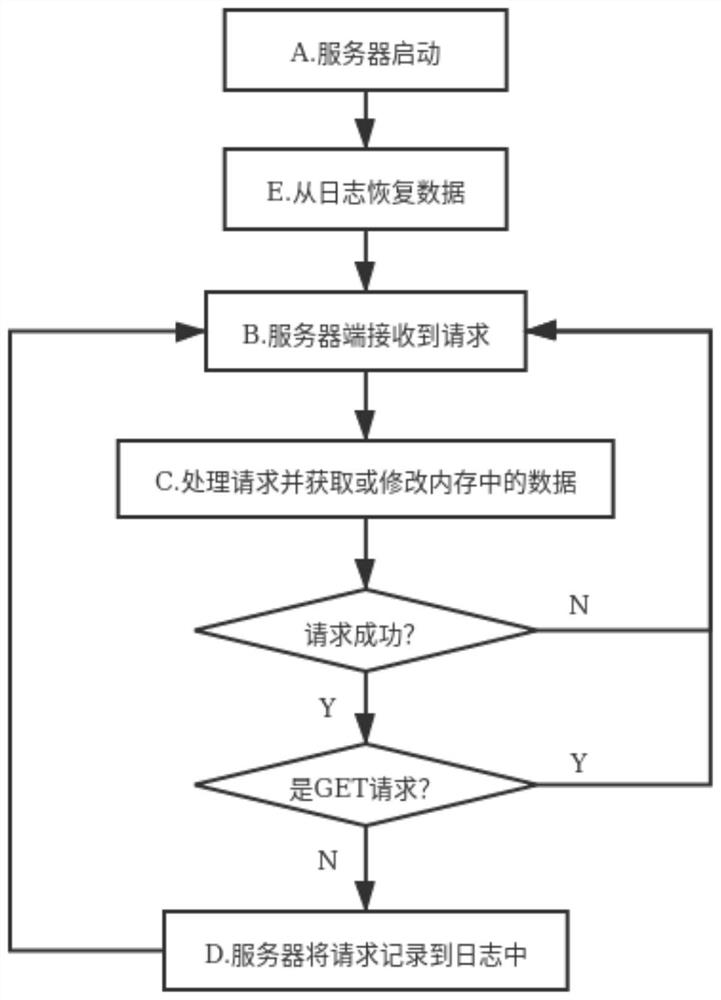
[0042] In a preferred embodiment 2, such as figure 2 As shown, a method for persisting data to an in-memory database in the form of a request log includes the following steps,
[0043] A, Server startup; in this step the server starts running.
[0044] E, recover data from the log. In this step, the server side reads the log file, and rebuilds the database in memory according to the log.
[0045] B. The server receives the client request;
[0046] C. The server side processes the request and obtains or modifies the data in the memory database; the server side processes the request sent by the client, and processing the request may need to obtain data from the memory database or modify the data in the memory database. If the request is unsuccessful, proceed to step B; if the request is a GET request, the data in the memory database has not been modified, and proceed to step B. If the request is successful and not a GET request, step D is performed.
[0047] D. The server ...
Embodiment 3
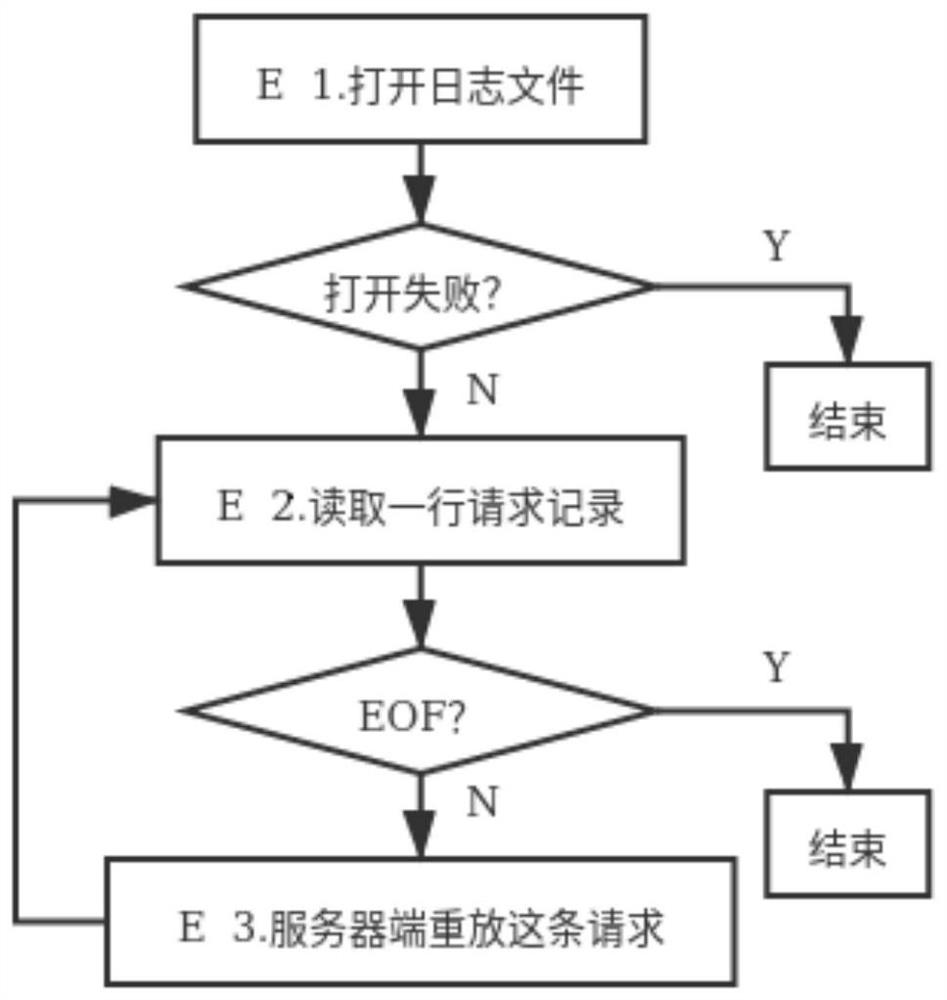
[0051] In a preferred embodiment 3, such as figure 2 and image 3 As shown, A, the server starts; in this step, the server starts to run.
[0052] E, recover data from the log. In this step, the server side reads the log file, and rebuilds the database in memory according to the log.
[0053] E1, open the log file; first open the log file, if it fails, then end step E, if it succeeds, then continue to execute step E2.
[0054] E2, read a line of requests; first read a line of requests from the log file, if EOF (end of document) occurs, then end step E, if EOF does not occur, then continue to execute step E3.
[0055] E3, the server replays the request and continues to execute E2. The server processes the read request in step E2 and generates data in the memory database.
[0056] B. The server receives the client request;
[0057] C. The server side processes the request and obtains or modifies the data in the memory database; the server side processes the request sent b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com