LDoS attack detection method based on EMDR-WE algorithm
An EMDR-WE and attack detection technology, applied in computing, computer components, pattern recognition in signals, etc., can solve problems such as low detection rate and unstable performance, and achieve high accuracy, low false alarm rate, and stability performance effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be further described below in conjunction with the accompanying drawings.
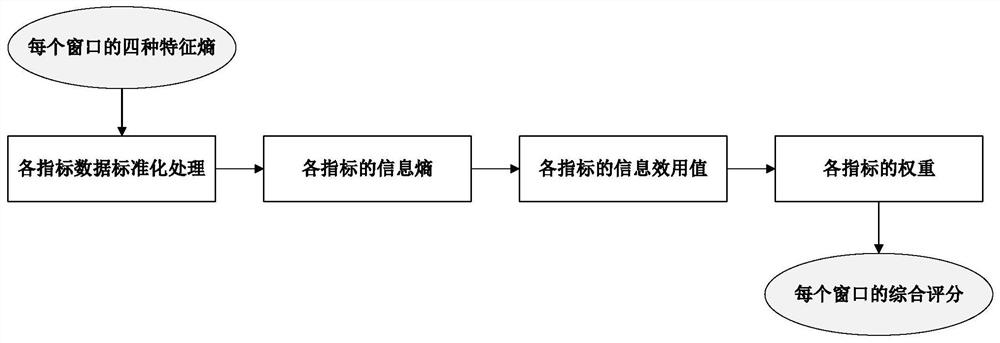
[0019] Such as Figure 4 Shown is the flowchart of the method of the present invention, the LDoS attack detection method mainly includes five steps: data sampling, data processing, feature extraction, comprehensive scoring and result evaluation.
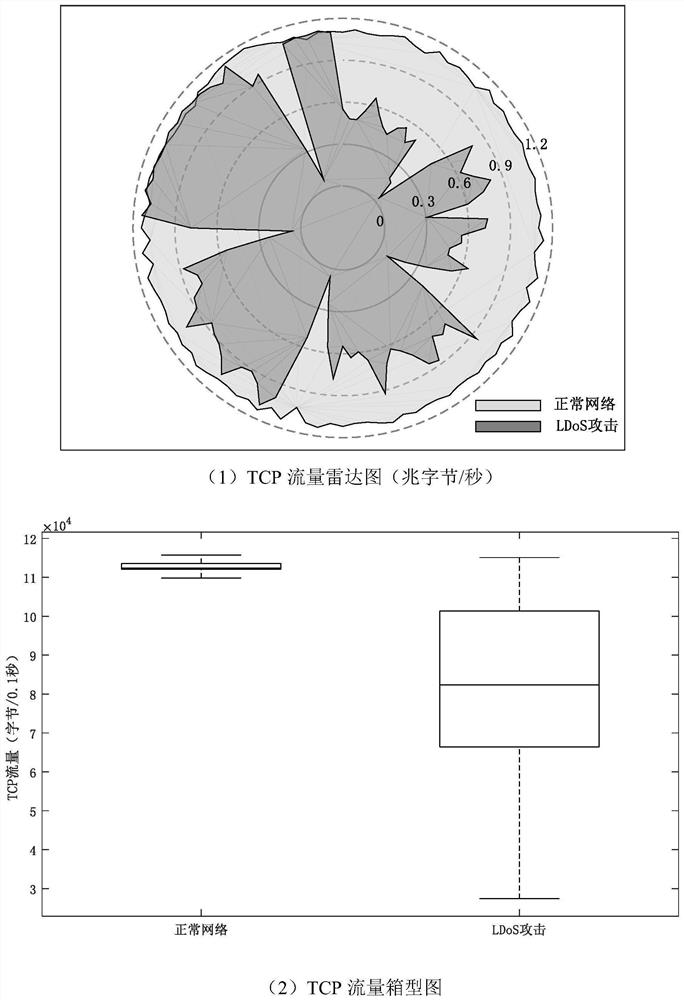
[0020] 1. Data sampling. Set a sampling point at the same unit time to collect the TCP traffic on the bottleneck link in the network to form the original TCP traffic sequence.
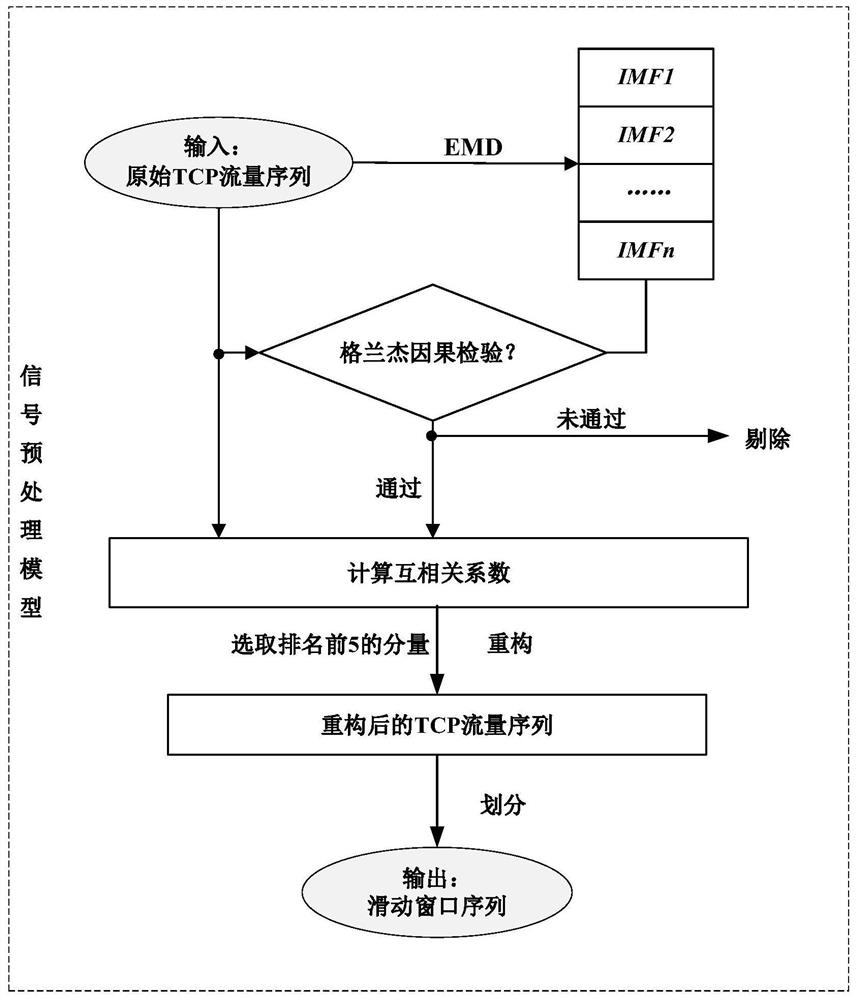
[0021] 2. Data processing. Empirical mode decomposition of the TCP traffic sequence to obtain several components, and then through Granger causality test and correlation coefficient ranking to filter the components, filter the false components and noise, linearly add the remaining components to reconstruct the TCP traffic sequence, and obtain It sets the sliding window. The above process is constructed as the signal preprocessing model of the pres...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com