Secure multi-party computing data system, method and equipment and data processing terminal
A secure multi-party computing and data technology, applied in the field of information security, can solve problems such as limited blockchain space, high communication complexity, and increased node burden, so as to solve the contradiction of space on the chain, protect privacy data security, and overcome horizontal dilated effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
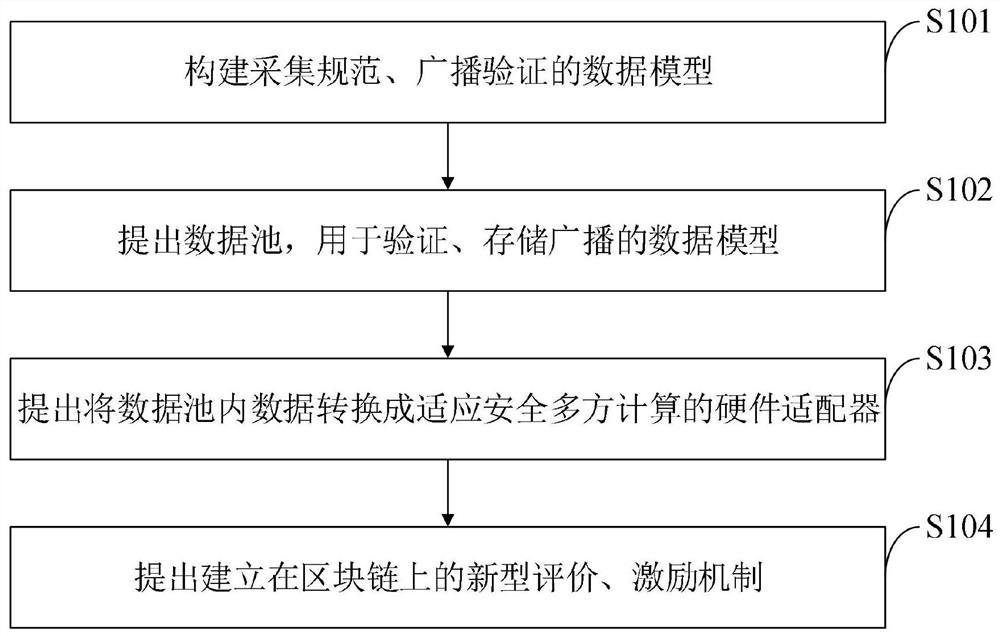
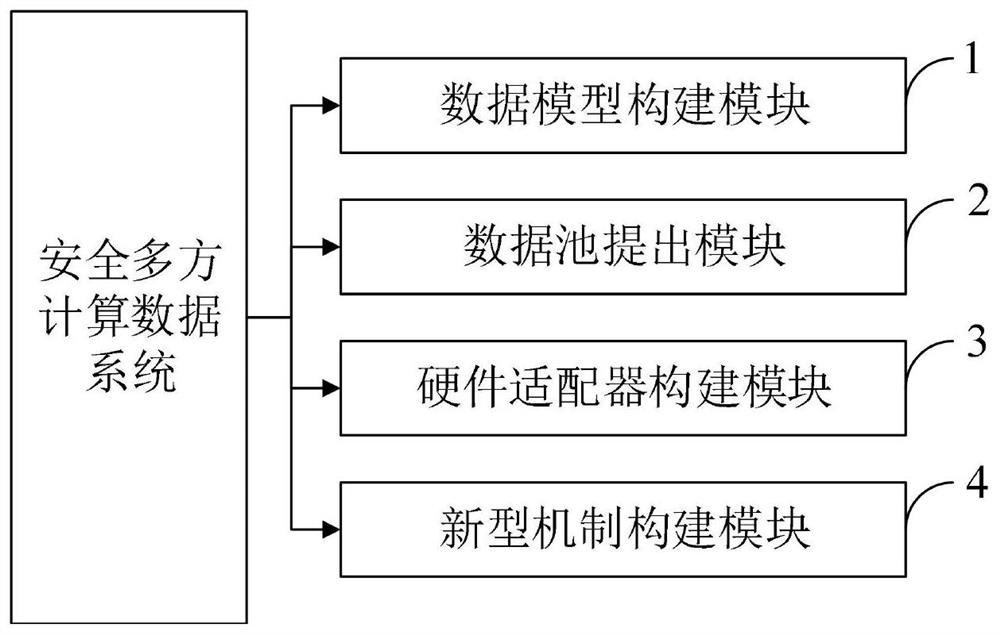
[0071] The present invention belongs to the information security technology, which discloses a security multi-party calculation protocol based on the block chain. The protocol includes a data model for building a collection specification, broadcast verification; a data pool node based on the block chain to verify the specifications of broadcast data, and store ciphertext data; propose a data pool within the data pool Adapt to the hardware adapter of the security multi-party calculation data model; proposes a new type of data quality evaluation, data flow transfer incentive mechanism. The data protocol published by the present invention is intended to protect the availability of the data, and the acquisition data can be used in ciphertext by the protocol of the present invention, and verify the ciphertext data specification by the data pool. Storage data retrieval feature; via "hardware adapter", changing data modality, so that it can make security multi-party calculations on the b...
Embodiment 2
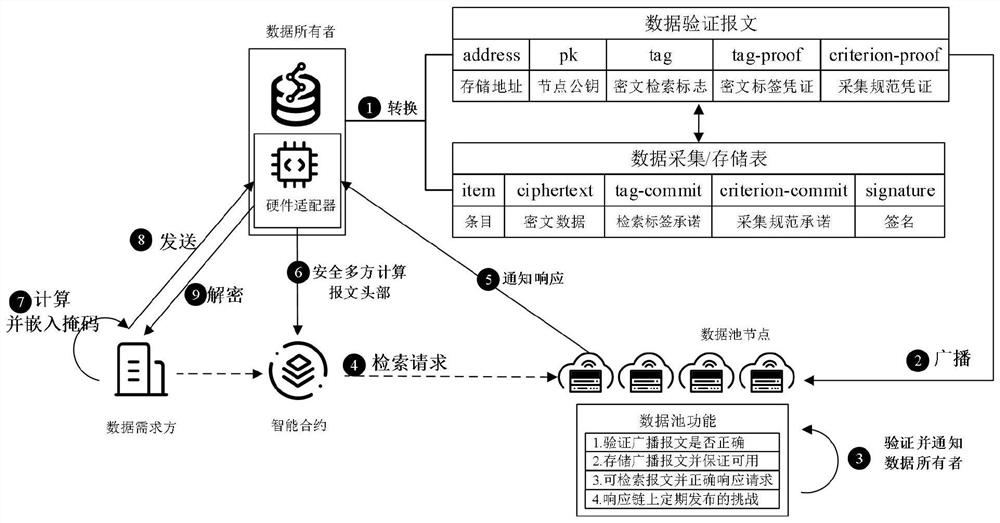
[0094] Such as image 3 As shown, the present embodiment describes the entire process of privacy data in the protocol and the device of the present invention and the entire process of the device.
[0095] Step 1: The data owner collects privacy data through the data acquisition node and converts according to the data model described in steps;
[0096] The second step, the node broadcasts the Verify request, requests to include data verification packets;
[0097] In the third step, after the data pool node receives the Verify request, if the verification is verified, the local storage space is deposited, and the Storage-Proof has been given, which will also send it to the collection node to prove that the data has been storage. The contract on the chain will send Storage-Challenge to the data pool node, and the data pool node will respond to challenges and give the Storage-Challenge-Proof Storage Proof.
[0098] In the fourth step, the data demand side needs to use the privacy data ...
Embodiment 3
[0106] With the introduction of relevant laws such as "Data Security Law" and "Personal Information Protection Law", data privacy protection is increasingly concerned about enterprises. In response to the privacy problem arising from the existing data collection, the present invention provides a secure multi-party computing data model based on the block chain to solve the privacy challenge of the data of privacy acquisition, safety usage.
[0107] In one embodiment, if Figure 4 As shown, it is the application of the model in the automotive and insurance field to protect the safety and privacy of the car data in the process of use.
[0108] The first step is to collect data from the automotive, such as the position of the car, the number of travel trajectories, the number of tech brakes, etc., these data are data that are interested in automobile manufacturers and automobile insurancemen. However, these data belong to the user's personal privacy data, and cannot be used in clear te...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com