Anti-attack block cipher encryption method for multi-scene application
A technology of block cipher and encryption method, which is applied in the field of embedded microcontrollers, can solve the problem that it is difficult for attackers to obtain effective information, and achieve the effects of reducing chip area consumption, increasing difficulty, and increasing attack difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be described in detail below according to the accompanying drawings.
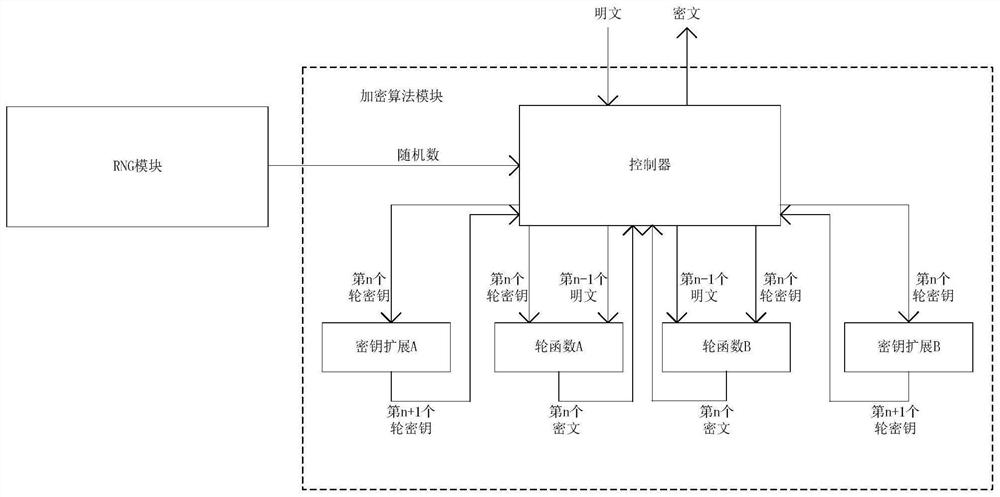
[0024] The design concept of the controller with the encryption algorithm of the anti-attack function is as follows: figure 1 Shown:
[0025] The operation process of the encryption algorithm is to first write data into the algorithm control register through the random number module, and then the controller performs the encryption operation until the operation ends. The random number module (RNG) writes random numbers into the registers in the encryption control module, and updates them when idle. After the user writes 128bit plaintext into the registers, when the encryption operation is started under the full anti-attack mode, the controller One set of random numbers will be read, according to the value of the first set of 128bit random numbers, and according to user settings, it is determined to insert k dummy rounds in the i-th round to ensure that the real encryption p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com