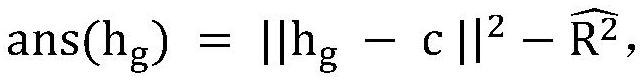Distributed system call chain and log fusion anomaly detection method
A distributed system and anomaly detection technology, applied in character and pattern recognition, response error generation, instruments, etc., can solve the problems of poor log anomaly detection technology and difficulty in distributed system anomaly detection, etc., and achieve good generalization capabilities, improved anomaly detection accuracy, and increased speed and scope
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
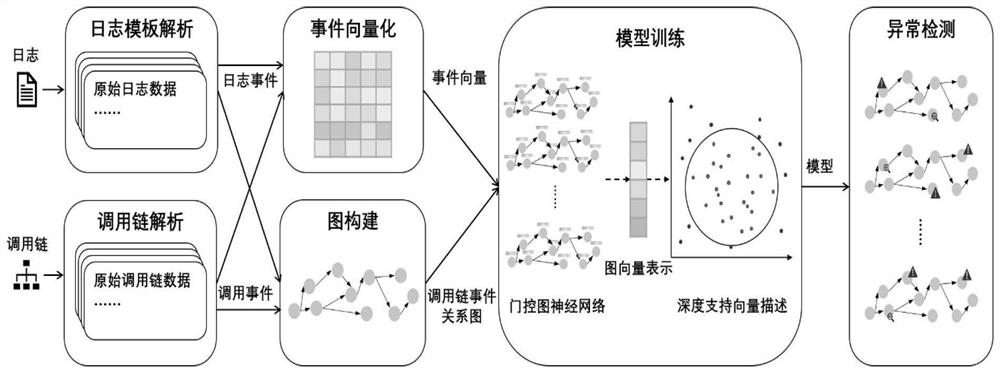
[0046] Using SkyWalking collection as the application performance monitoring platform and PyTorch as the distributed system of the deep learning framework, the distributed system call chain and log fusion anomaly detection method based on the graph neural network of the present invention are further introduced.
[0047] For anomaly detection model training, the specific process is as follows:
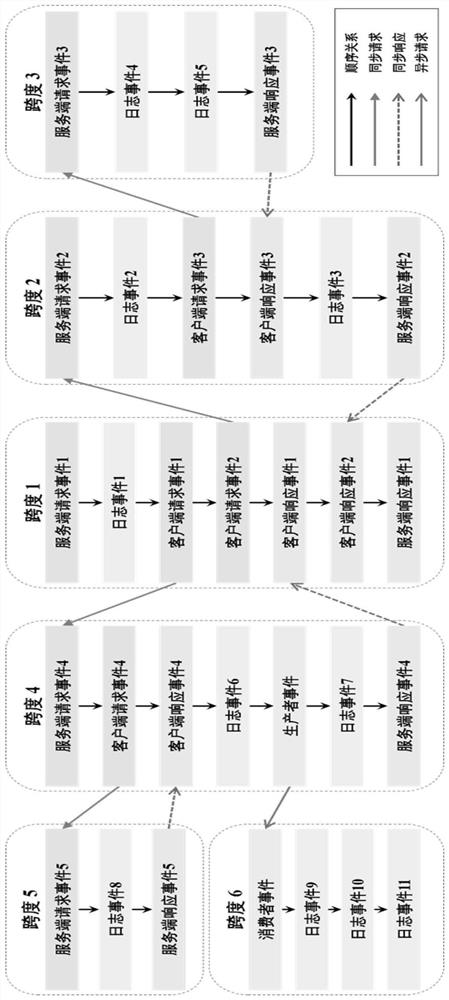
[0048] (1) Collect call chain and log data. Configure the SkyWalking agent for each program in the distributed system, set the call chain and log collection rules. The call chain and log data generated by the normal operation of the system are collected and stored in ElasticSearch as training data.
[0049] (2) Construct the data set of call chain event relationship graph. Process the collected training data in the order of steps (1) to (4), construct a corresponding call chain event relationship graph for each call chain, and use all the processed data as a graph data set for the dee...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com