System file protection method and device based on network security and electronic equipment
A system file and network security technology, applied in the field of network security, can solve problems such as economic loss and data damage, and achieve the effect of reducing the probability of being damaged
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
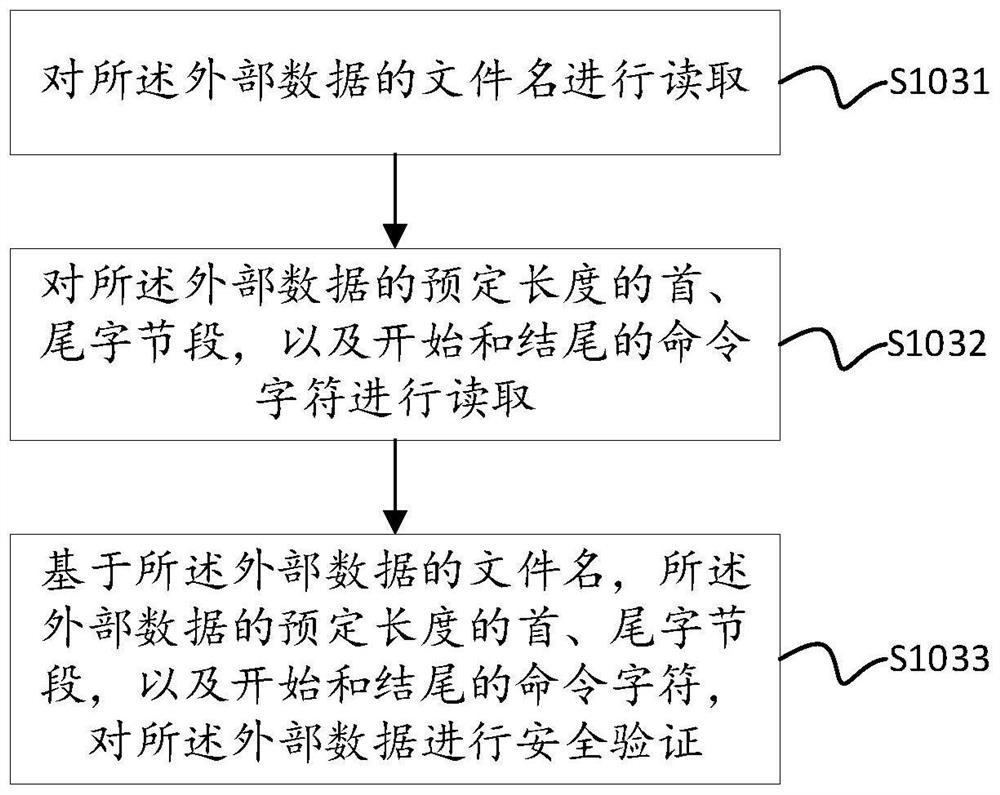
[0029]A network attack refers to an attack on the hardware, software and data in the local system by using the loopholes and security flaws in the local system. The means of attack include password intrusion, email attack, attacking other nodes through one node, network monitoring, using hacker software attack, security hole attack and port scanning attack, etc. When the system is successfully attacked by an external network, not only will the system be controlled, but also the data files in the system will be stolen, resulting in economic losses.
[0030] At present, the ways to defend against attacks include improving security awareness, using anti-virus and anti-hacking and other firewall software, setting up proxy servers, hiding your own IP address, taking anti-virus and anti-hacking as routine work, regularly updating anti-virus components, and keeping anti-virus software at permanent status, etc. Since hackers often launch attacks on specific dates, computer users shou...
Embodiment 2
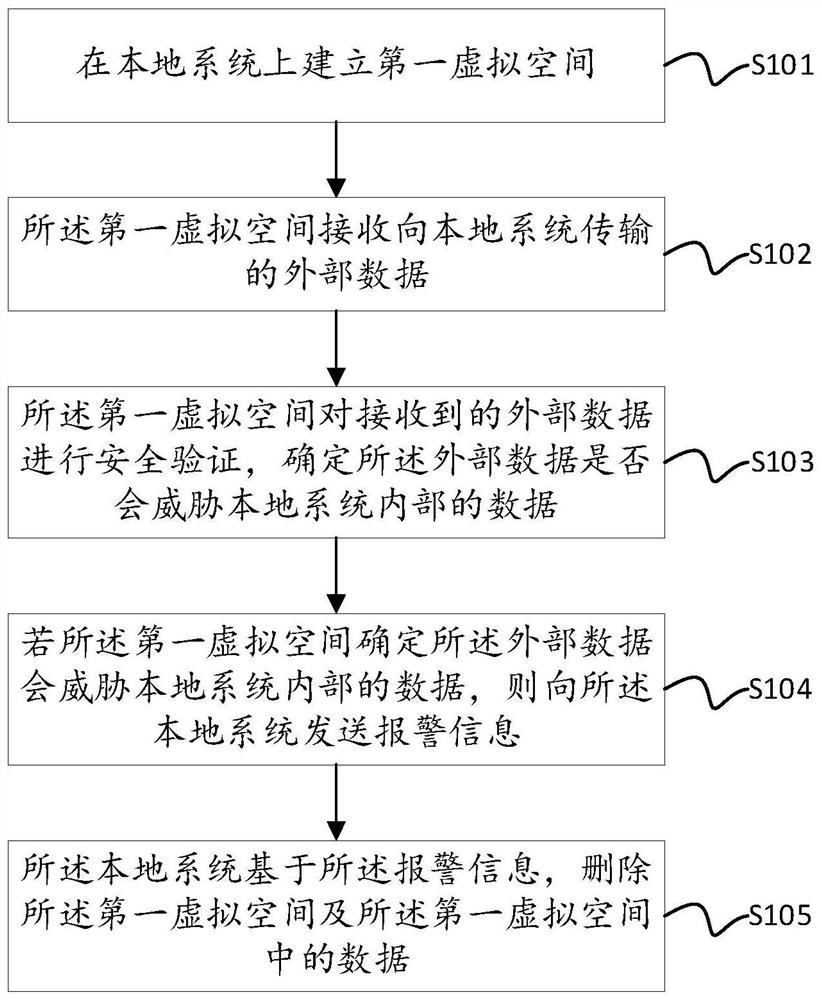
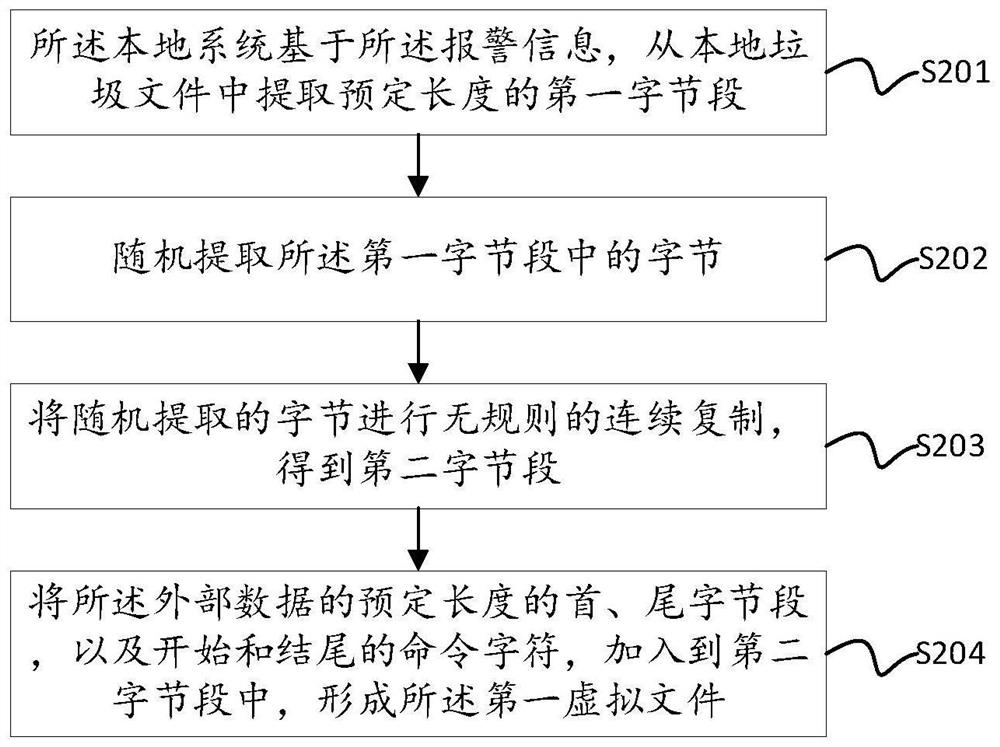
[0070] see Figure 4 , the embodiment of the present invention provides a system file protection device based on network security, including: a first virtual space establishment module 201, configured to establish a first virtual space on a local system; an external data receiving module 202, configured for the first virtual space A virtual space receives external data transmitted to the local system; the security verification module 203 is used for the first virtual space to perform security verification on the received external data, and determines whether the external data will threaten the internal data of the local system; alarm Module 204, configured to send an alarm message to the local system if the first virtual space determines that the external data will threaten the data inside the local system; the first virtual space deletion module 205 is used for the local system to The alarm information deletes the first virtual space and the data in the first virtual space. ...
Embodiment 3
[0083] see Figure 5, the embodiment of the present invention provides an electronic device, the electronic device includes: a housing 301, a processor 302, a memory 303, a circuit board 304 and a power supply circuit 305, wherein the circuit board 304 is placed in the space enclosed by the housing 301 Internally, the processor 302 and the memory 303 are arranged on the circuit board 304; the power supply circuit 305 is used to supply power to each circuit or device of the above-mentioned electronic equipment; the memory 303 is used to store executable program code; the processor 302 reads the memory 303 The executable program code stored in the computer is used to run a program corresponding to the executable program code, which is used to execute the network security-based system file protection method described in any one of the preceding embodiments.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com