Intelligent networking safety analysis method based on sensing and calculation linkage
A technology of security analysis and intelligent networking, applied in the field of security analysis of intelligent networking based on sensor-computing linkage, can solve problems such as unconsidered security risks, potential safety hazards, and insufficient vulnerability analysis, so as to avoid neglect and misjudgment, and simplify the difficulty , the effect of avoiding security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to facilitate those skilled in the art to understand and implement the present invention, the present invention will be described in further detail below with reference to the accompanying drawings and embodiments. It should be understood that the embodiments described herein are only used to illustrate and explain the present invention, but not to limit it. this invention.
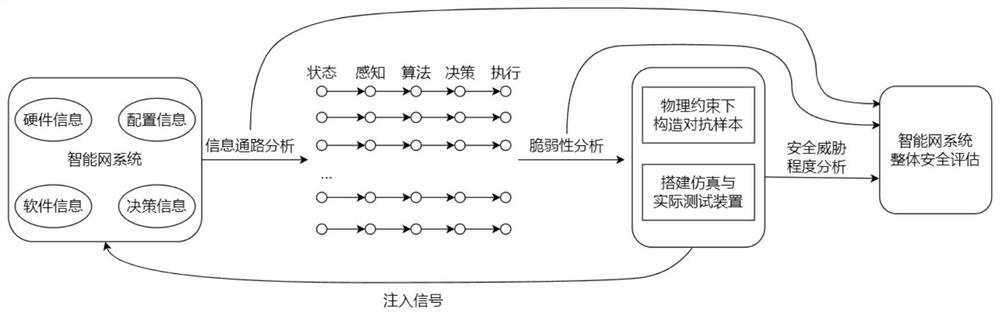
[0035] The method flow of the embodiment of the present invention, such as figure 1 shown.
[0036] The intelligent networking security analysis method based on sensory computing linkage of the present invention takes an autonomous vehicle as an example. There are many information paths in an autonomous vehicle, for example, "object → camera image → obstacle detection → driving decision model → steering / no "Steering", "Pedestrian→Lidar Capture Point Cloud→Point Cloud Classification→Driving Decision Model→Brake / Acceleration", etc. The specific analysis method includes the following steps...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com