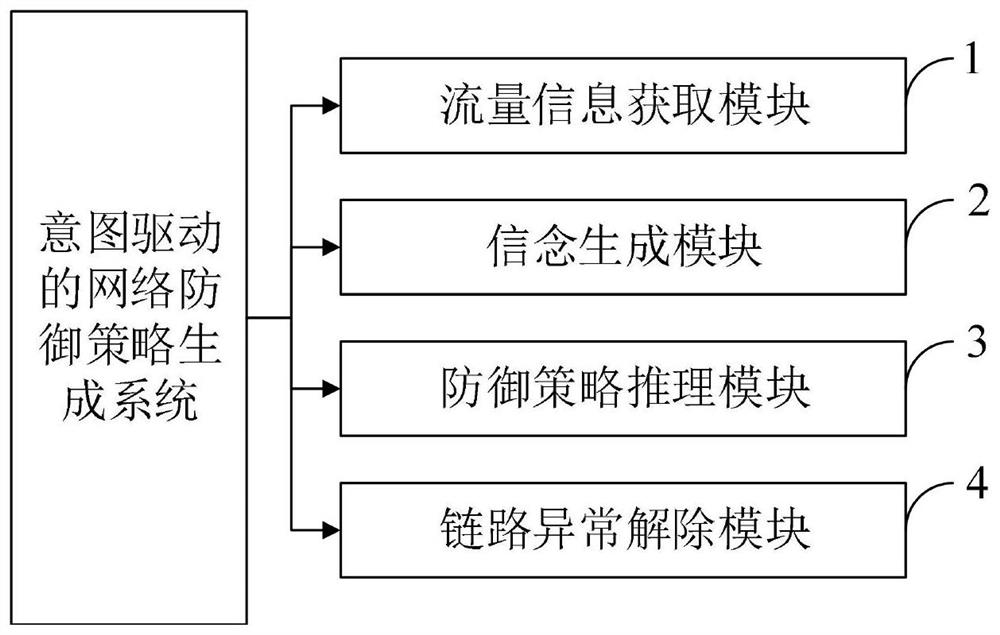
Intention-driven network defense strategy generation method, system and application
An intent and strategy technology, applied in the field of intent-driven network defense strategy generation, can solve problems such as incapacity, inflexibility, and inability to detect attacks, achieving high flexibility, maintaining network security, and improving network resilience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
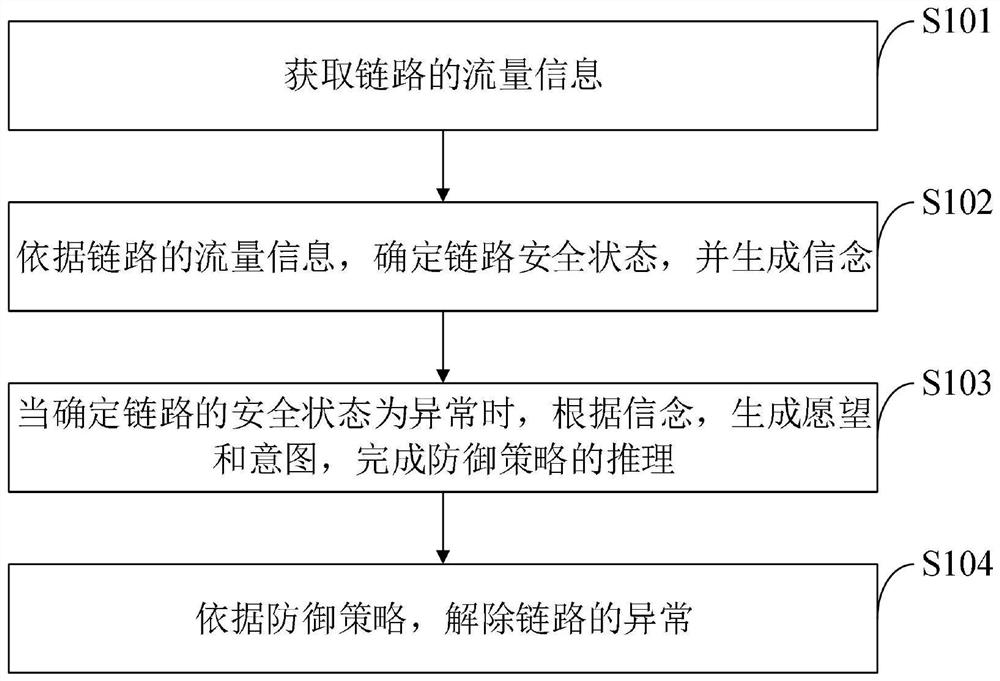
[0077] The intent-driven network defense policy generation method provided by the embodiment of the present invention includes:
[0078] Obtain the traffic information of the link;
[0079] According to the traffic information of the link, determine the security status of the link and generate beliefs;
[0080] When it is determined that the security state of the link is abnormal, according to the belief, the desire and intention are generated, and the reasoning of the defense strategy is completed;
[0081] Eliminate the abnormality of the link according to the defense strategy.
[0082] According to the traffic information of the link provided by the embodiment of the present invention, the link security state is determined and the belief is generated, including:
[0083] When the input traffic of the link exceeds a given threshold, determine that the security state of the link is abnormal, and generate a new belief;
[0084] update the belief when the input traffic of th...
Embodiment 2
[0101] The intent-driven network defense policy generation method provided by the embodiment of the present invention is implemented as follows:
[0102] Obtain the traffic information of the link;
[0103] According to the traffic information of the link, determine the security status of the link and generate beliefs;
[0104] When it is determined that the security state of the link is abnormal, according to the belief, the desire and intention are generated, and the reasoning of the defense strategy is completed;
[0105] According to the defense strategy, remove the link abnormality.
[0106] According to the link traffic information provided by the embodiment of the present invention, the link security state is determined, and a belief is generated:
[0107] When it is detected that the input traffic in the link exceeds the given threshold, the link is in an abnormal state at this time, and the belief overUsage(link) is generated, where the belief overUsage(link) indica...
Embodiment 3
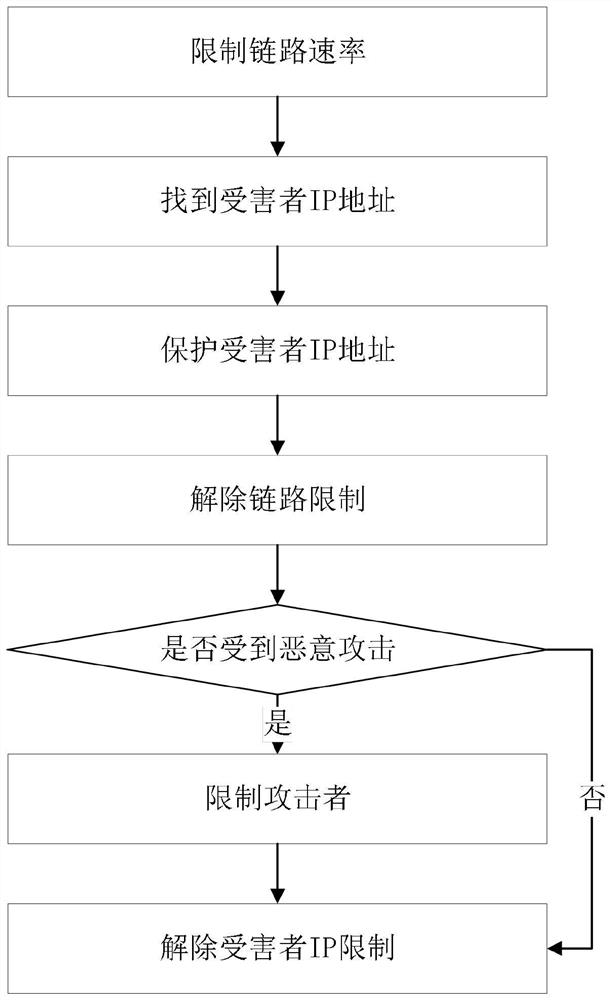
[0128] like image 3 As shown, the defense process of the intent-driven network defense policy generation method provided by the embodiment of the present invention includes:
[0129] Step 1: Limit the link rate.
[0130] After it is detected that the security state of the link becomes abnormal, that is, after the belief overUsage(link) is detected, in order to ensure the security of the link before finding out whether it is maliciously attacked, a rate limit is applied to the traffic entering the link. processing to keep the traffic in the link within an acceptable range, that is, generate a desire attackPrevented(link), generate an intent limitLinkRate(link) according to this desire, and after the intent is completed, generate a new belief linkRateLimited(link)( Indicates that the rate of traffic entering the link has been limited), specifically setting a Rate parameter, and then passing the rate limiting ability of the proxy, so that the traffic entering the link is the pe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com