Distributed hacker tracking system in controllable computer network
A computer network and tracking system technology, applied in the field of hacker tracking system, can solve the problems of difficult to provide tracking of the real source of hackers, application difficulties, large errors, etc., and achieve the effect of good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0131] Hereinafter, we will further illustrate the present invention through embodiments in conjunction with the accompanying drawings.
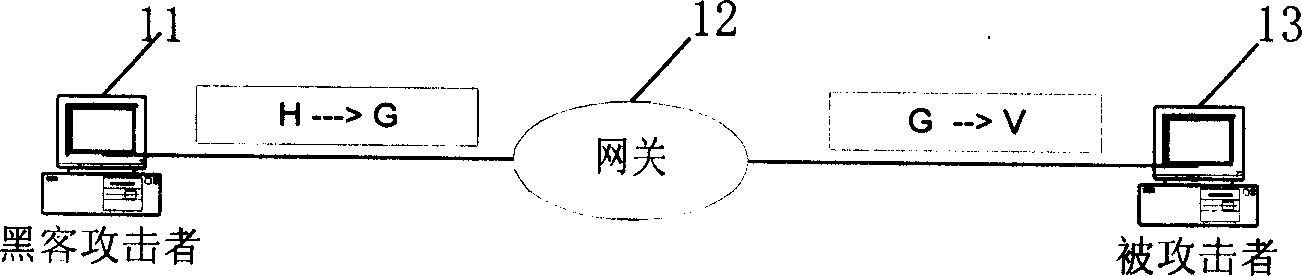
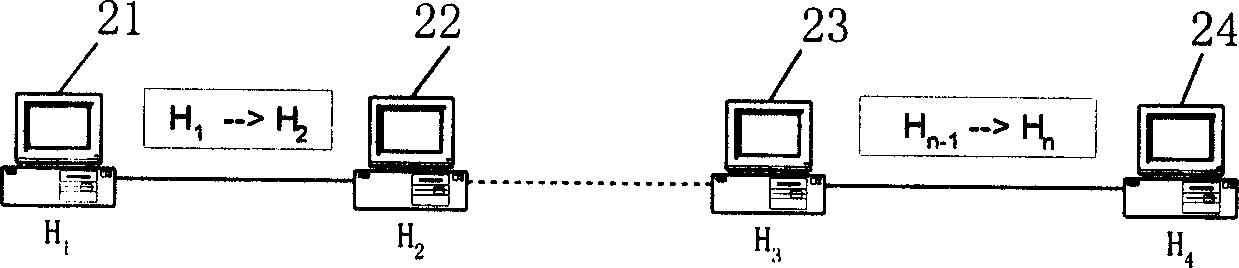
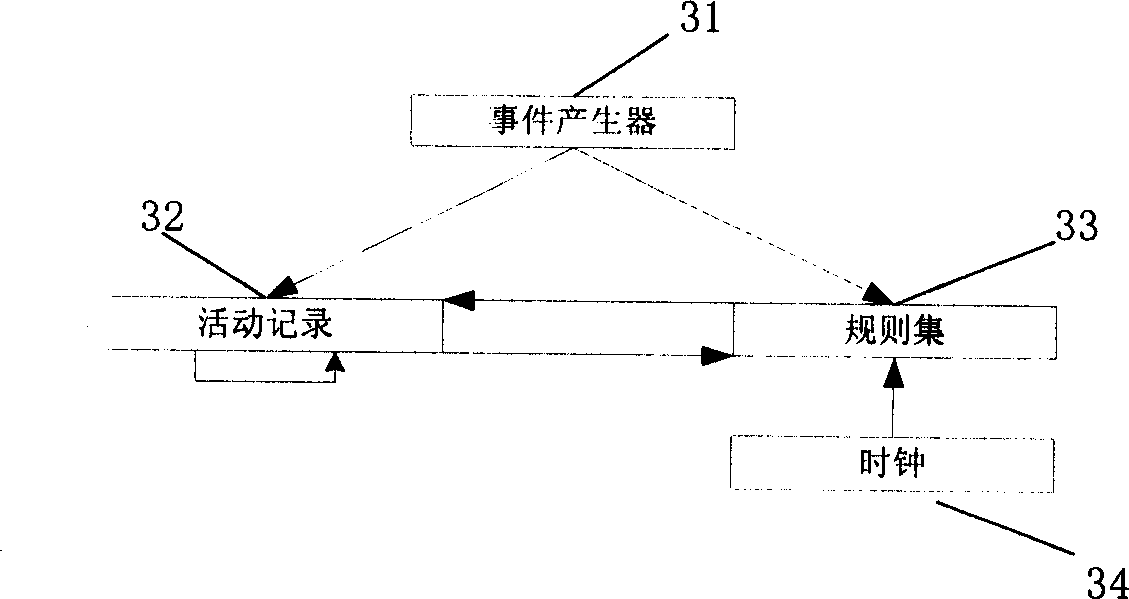
[0132] A complete hacker tracking system consists of two parts: hacker identification and hacker tracking. We use intrusion detection technology to complete hacker identification, and complete hacker tracking based on intrusion detection alarm information and data fingerprints. The hacker tracking system model we built is like Figure 5 Shown.
[0133] in Figure 5 Among them, the hacker is attacker 11, the target host being attacked is attacked 13, gateway 1 (Gateway1) 56, gateway 2 (Gateway 2) 57...Gateway n-1 (Gateway (n-1) 58. Network monitor 1(NM1)52, network monitor 2(NM2)53,...Network monitor n(NMn)54, distributed on the network path from the attacker to the attacked. The network monitor completes the monitoring of network packets And analysis, if an attack is found, it sends an alarm message to the manager manager. The manager completes ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com