A dynamic identity certification method and system
An identity authentication and dynamic technology, applied in the field of information security authentication, can solve problems such as the inability to guarantee real-time authentication, and achieve the effects of improving security, reducing usage costs, and ensuring real-time performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0071] Taking the banking system as an example below, the present invention will be further described in detail in conjunction with the accompanying drawings.
[0072] 1. System Structure Description
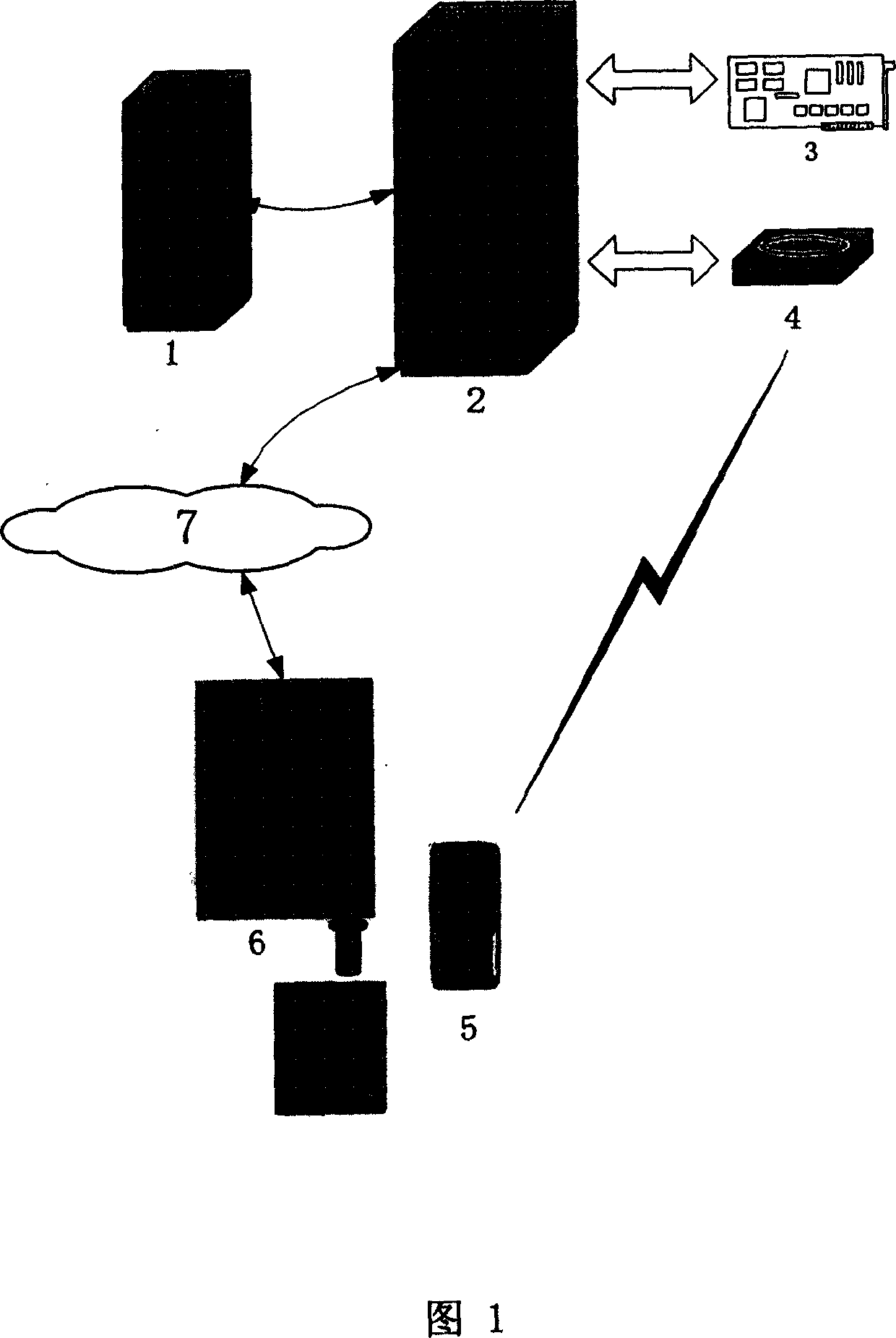
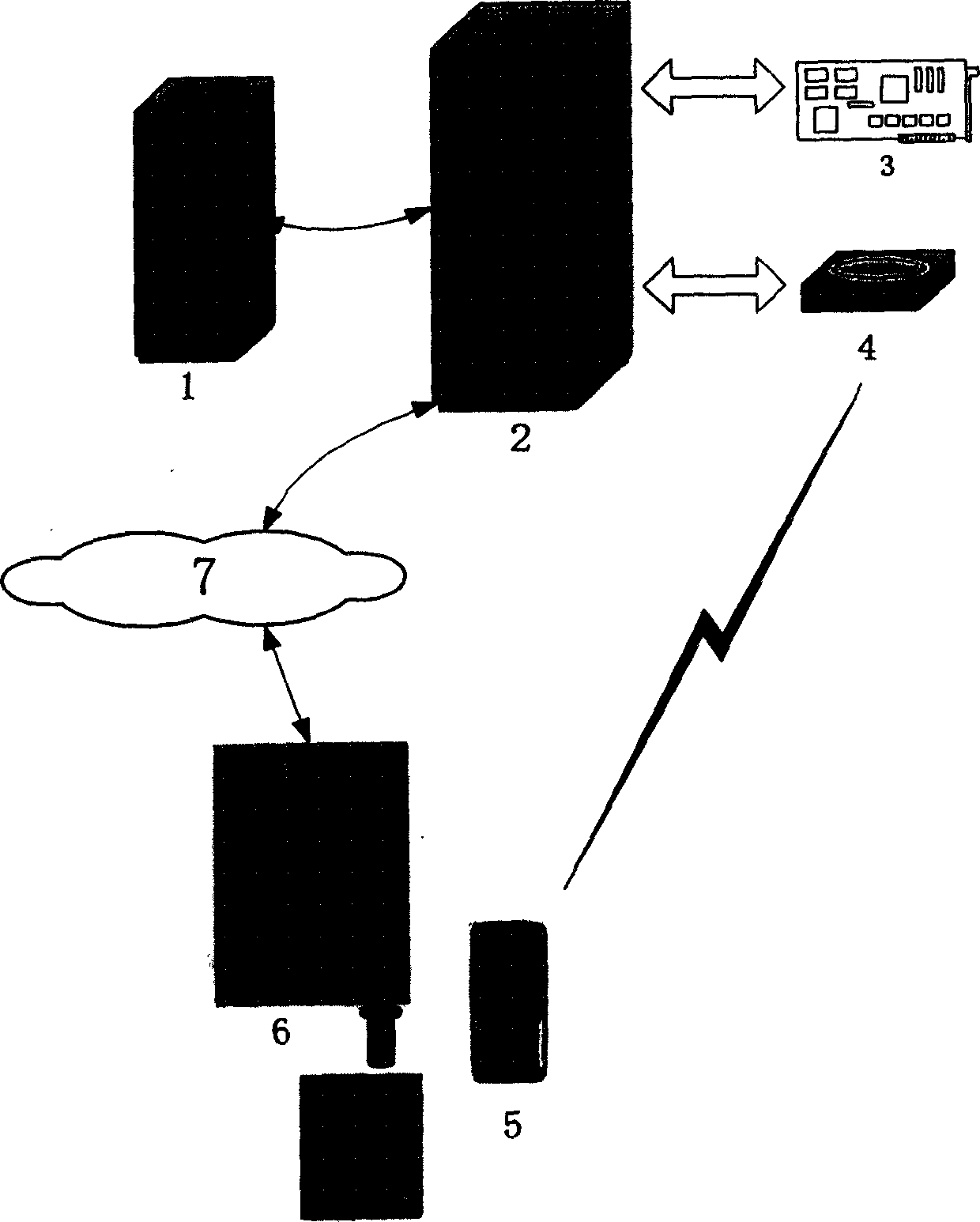
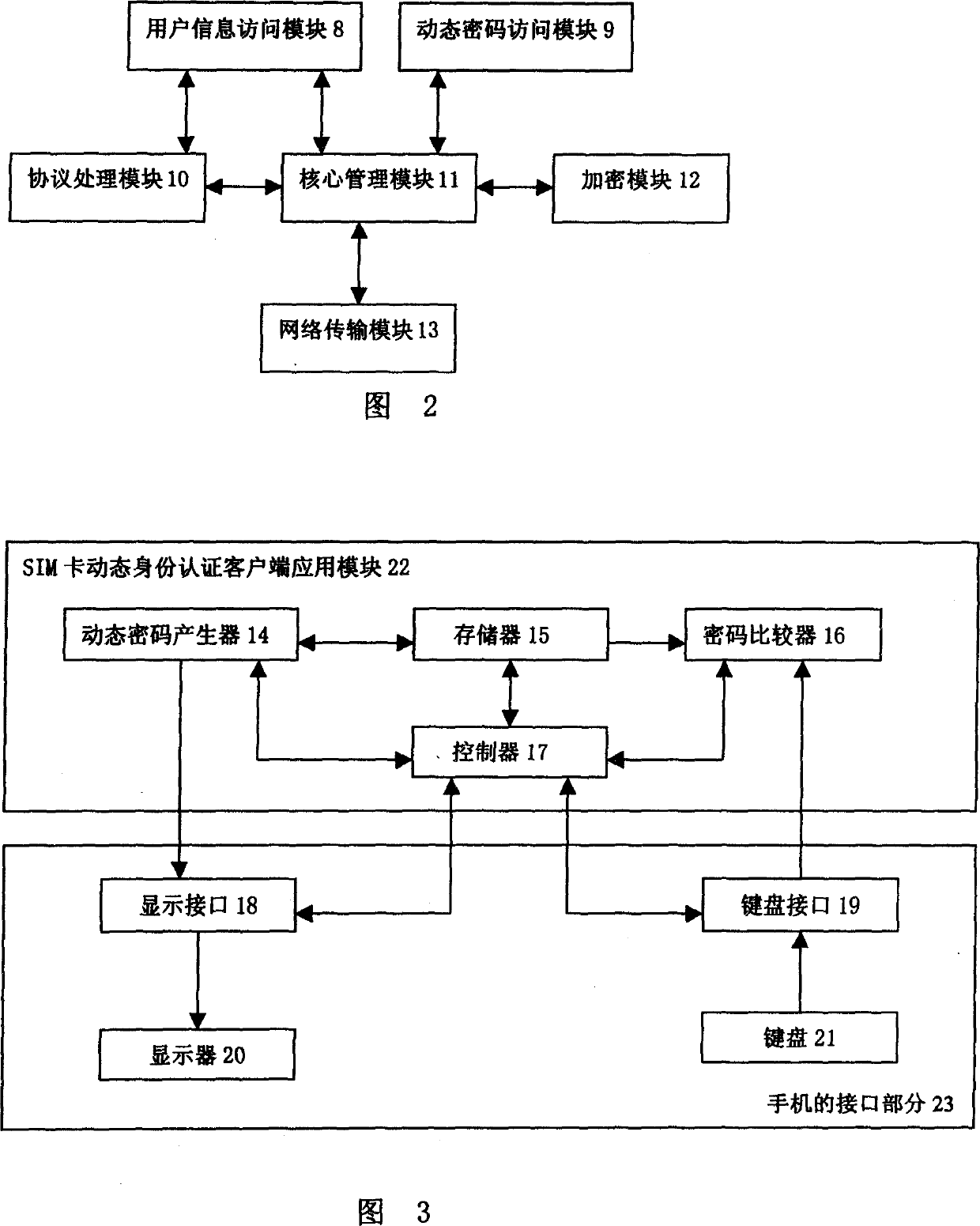
[0073] FIG. 1 is an overall structural diagram of the authentication system, including a user terminal 6, a user information server 1, an authentication server 2 and a mobile phone token 5. User information server 1 is the data server in the system, using the oracle9i database system, which stores the form set according to the identity authentication protocol, and provides each user information required in the authentication process. It includes the following fields: ID number, user ID, registration password Pr, encryption and decryption key Ke, current work password Ks (the same as the current work password stored in the mobile phone token), the sign that the account is being used ( prevent competitive attacks) and mobile phone numbers, etc. The user information server 1 rece...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com