Method and system for testing safety switch-in protocol conformity of network terminal
A security access and network terminal technology, applied in the field of network security access protocol testing, can solve the problems of the accuracy of the benchmark equipment affecting the accuracy of the test results, the inability to give wrong positioning information, and the deviation of the test results. The results are accurate, precise positioning, and the test data is complete.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
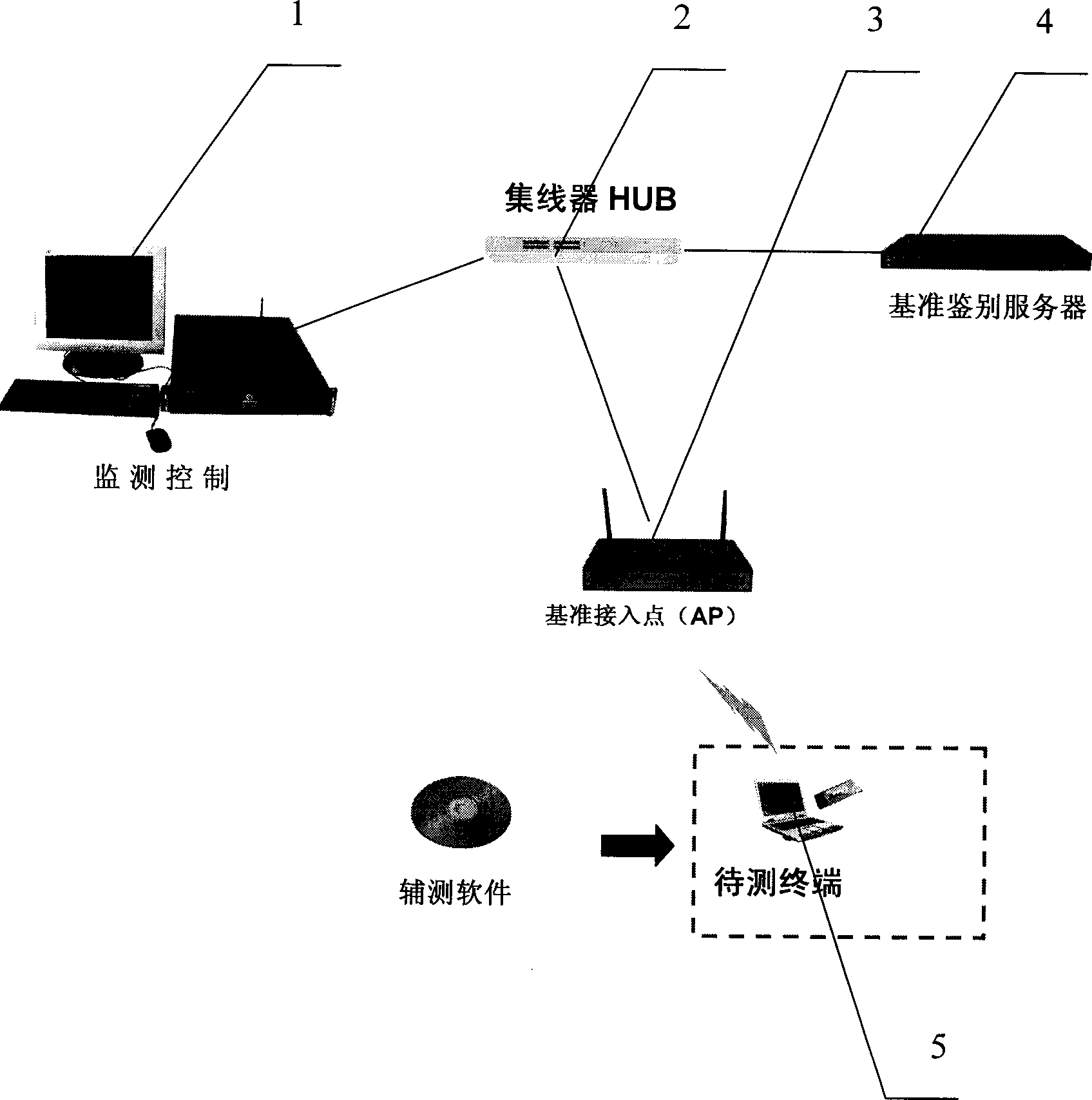
[0050] WAPI agreement or IEEE802.11i agreement all can be applicable to the method of the present invention, and its steps are as follows:
[0051] 1) Activate the secure access protocol authentication process;
[0052] 2) Capture the secure access protocol data packets generated during the authentication process;
[0053] 3) Analyze and detect the packet encapsulation format and protocol flow of the secure access protocol.
[0054] The following is a specific embodiment when the security access protocol is the WAPI protocol, and the whole specific testing process of its method is as follows:
[0055] 1) Activate the WAPI authentication process;
[0056] 2) Capture the WAPI protocol data packets that are produced in the authentication process; if the WAPI protocol data capture is incomplete, the network terminal to be tested has not passed the WAPI test, continue to process the captured data in step 3, and display the results;
[0057] The WAPI protocol packet includes: WAI...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com