Electronic mail system and method based on CPK safety authentication
An email and security authentication technology, applied in electrical components, transmission systems, digital transmission systems, etc., can solve the problems of low efficiency, slow processing speed, large storage space, etc., so as to achieve no storage space occupation, increased processing speed, The effect of improving operational efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
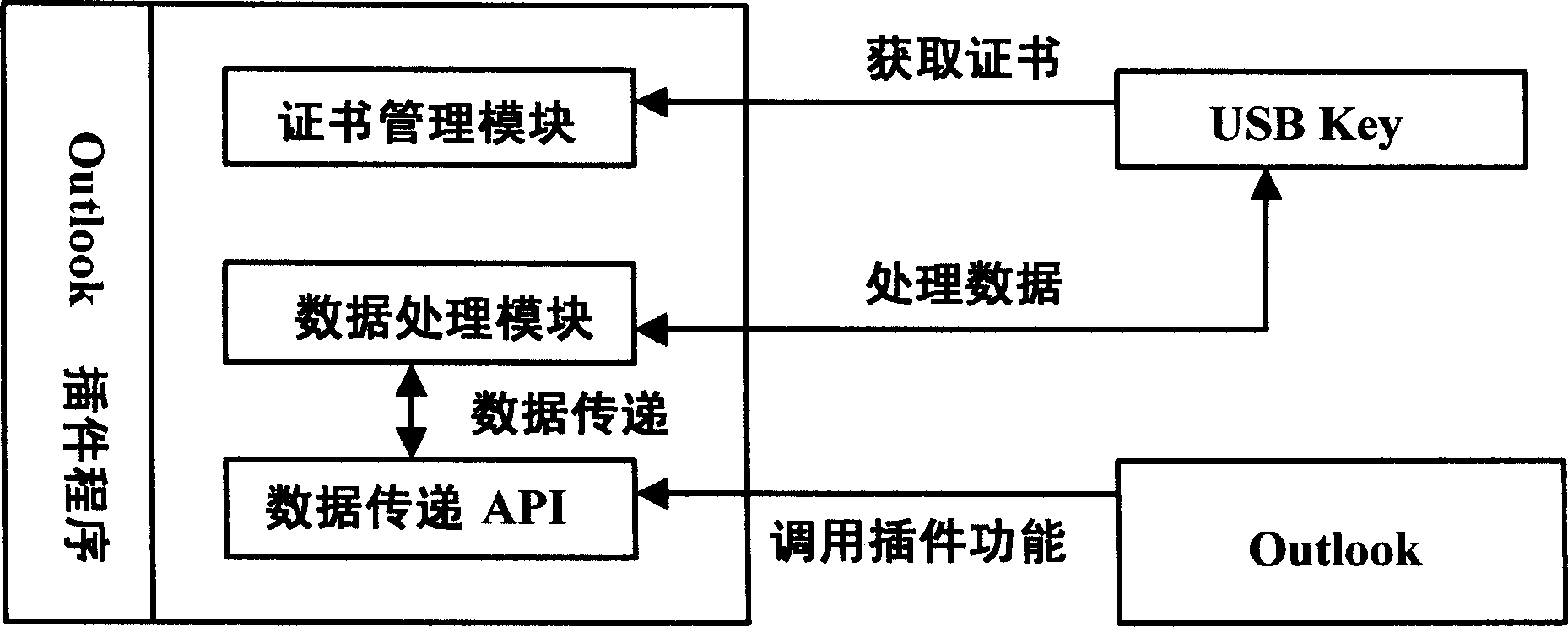
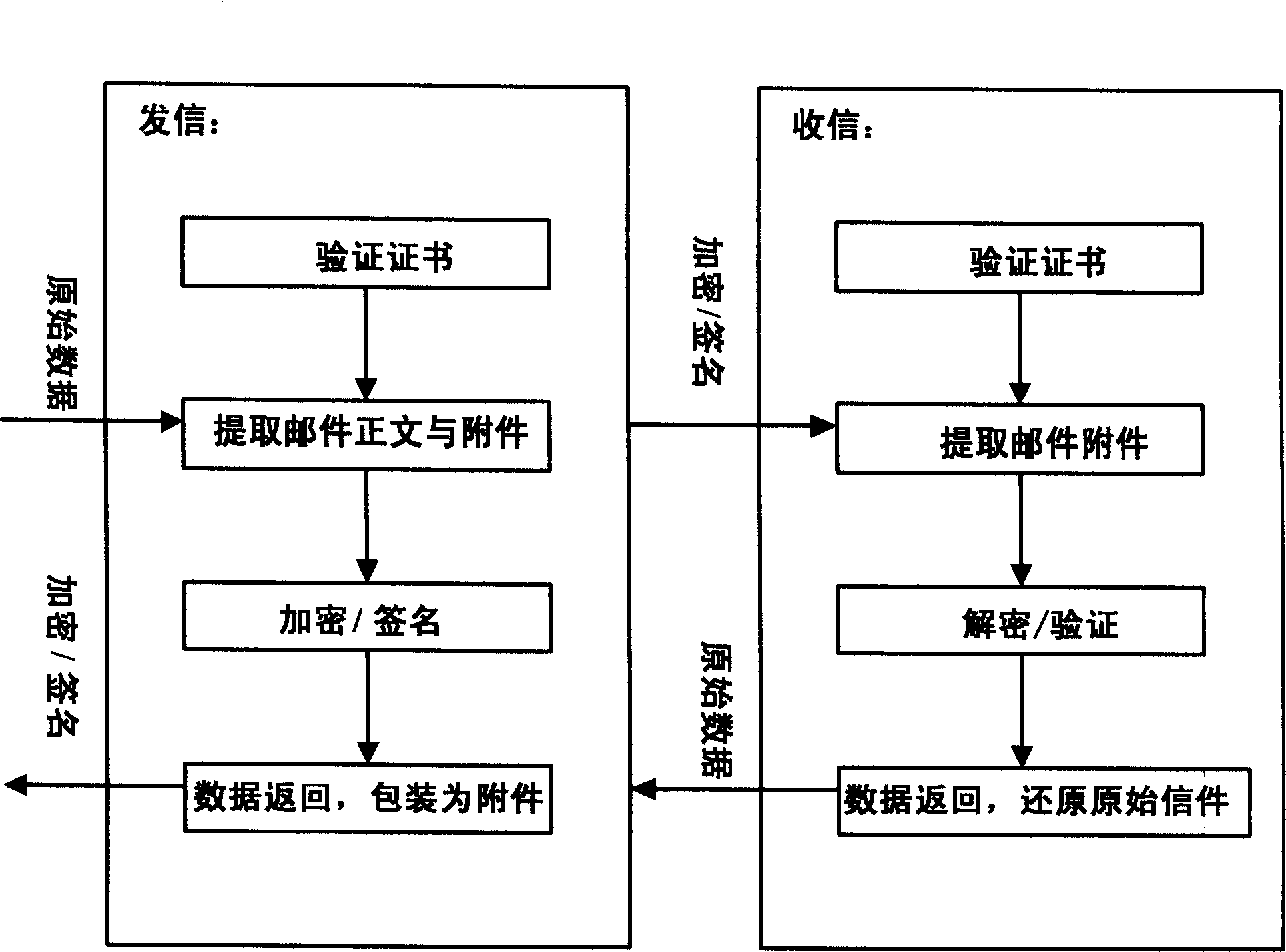
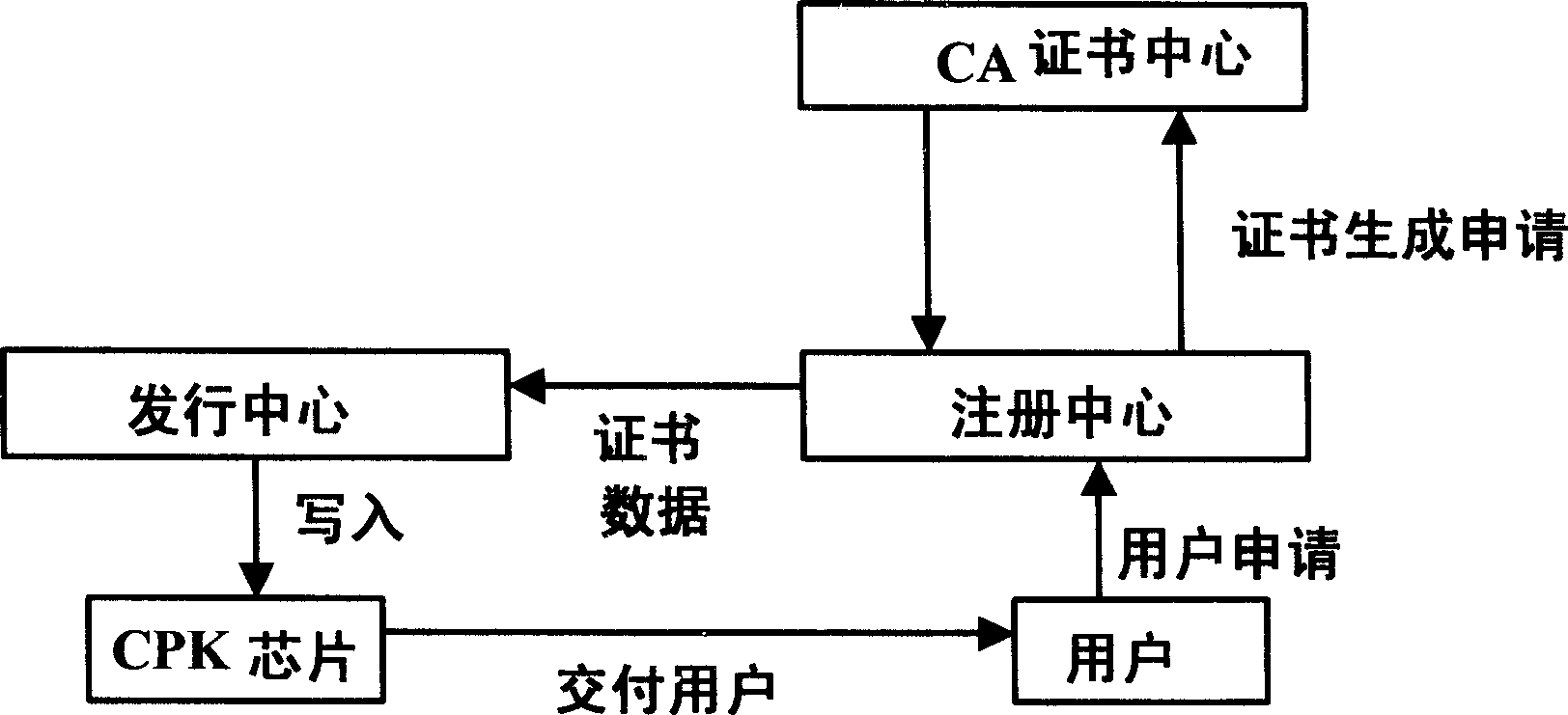
[0036] Attached below figure 1 ~ 3 further details a kind of email system and method based on CPK security authentication of the present invention.
[0037] The combined public key (Combined Public Key, CPK) security authentication algorithm is a discrete logarithm puzzle type identity-based key generation and management system. Based on the mathematical principle of the discrete logarithm problem, it constructs the encryption and decryption algorithm in the security authentication algorithm, generates the public key and private key matrix, and uses the hash function (HASH) and cryptographic transformation to map the identity of the entity to the row coordinates and column coordinates of the matrix Sequence, and select and combine matrix elements to generate a large number of public and private key pairs composed of public and private keys, so as to realize ultra-large-scale key generation and distribution based on identification.
[0038] The CPK key algorithm uses discrete ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com