File processing system and file processing method
A document processing and document technology, applied in electronic digital data processing, special data processing applications, digital data processing components, etc., can solve the problems of imperfect page layering technology, easy to find, difficult to find k, etc. The effect of historical traces
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
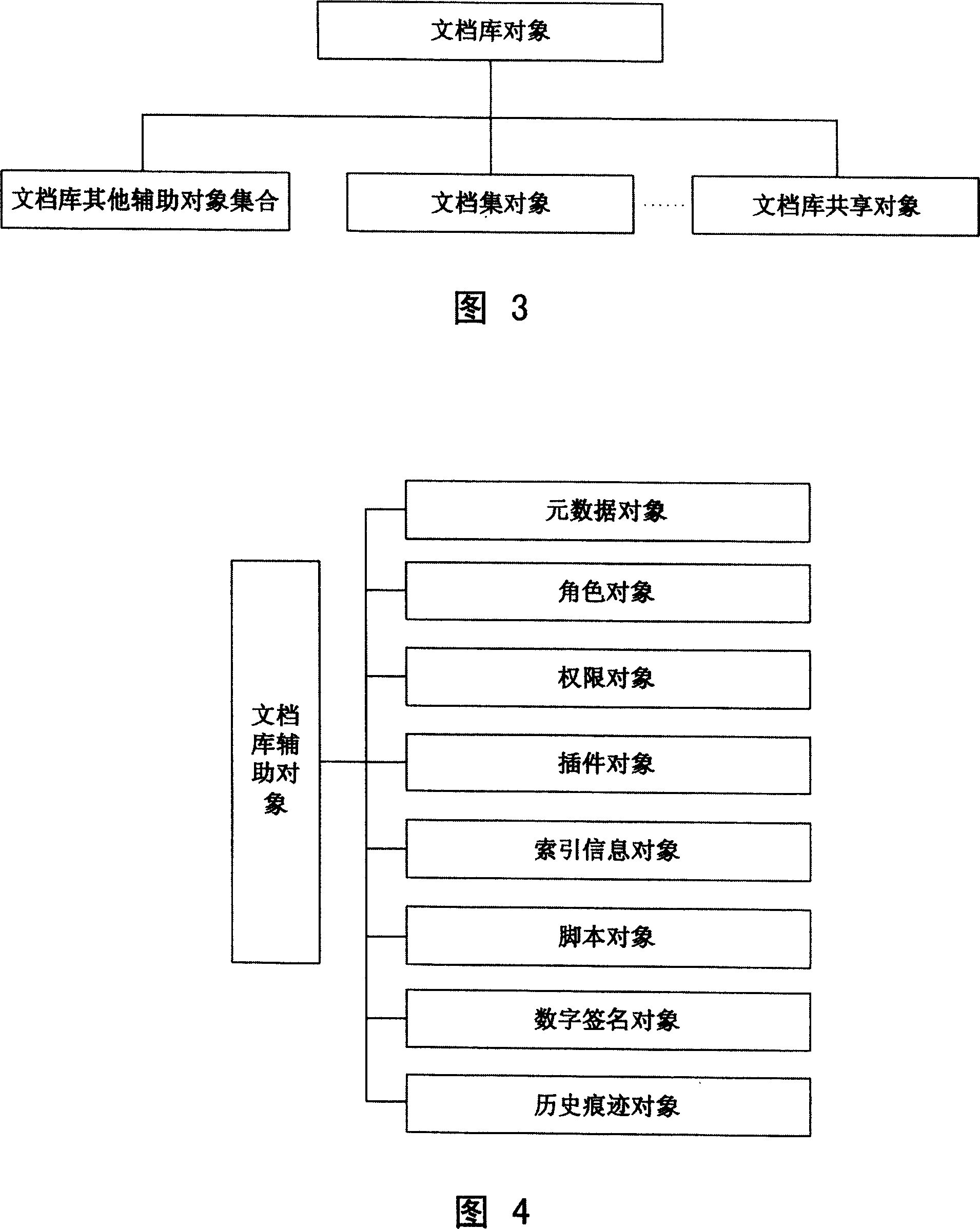
[0796] A role consists of a unique ID number and a pair of unique PKI keys, but only its ID number and public key are stored in the role object, and the private key is mastered by the application software. The ID number can be any number or character string, as long as different roles are assigned different IDs. The PKI algorithm can be one of ECC and RSA.
[0797] The security management function is composed of a role management unit, a secure session channel unit, an identity authentication unit, an access control unit, and a signature unit.
[0798] The whole process of logging in with a certain role (or multiple roles), performing a series of operations, and finally logging out is called a session. A session includes a session flag, a list of login roles. Sessions can be conducted over a secure session channel. A secure session channel has a session key that is used to encrypt data passed between the two parties. Asymmetric keys can be used as session keys, but symmetr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com