Fibre channel address blocking
a technology of filter channel and address block, applied in the field of filter channel computer networks, can solve the problem of unauthorized requests for private data from anyon
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
second embodiment
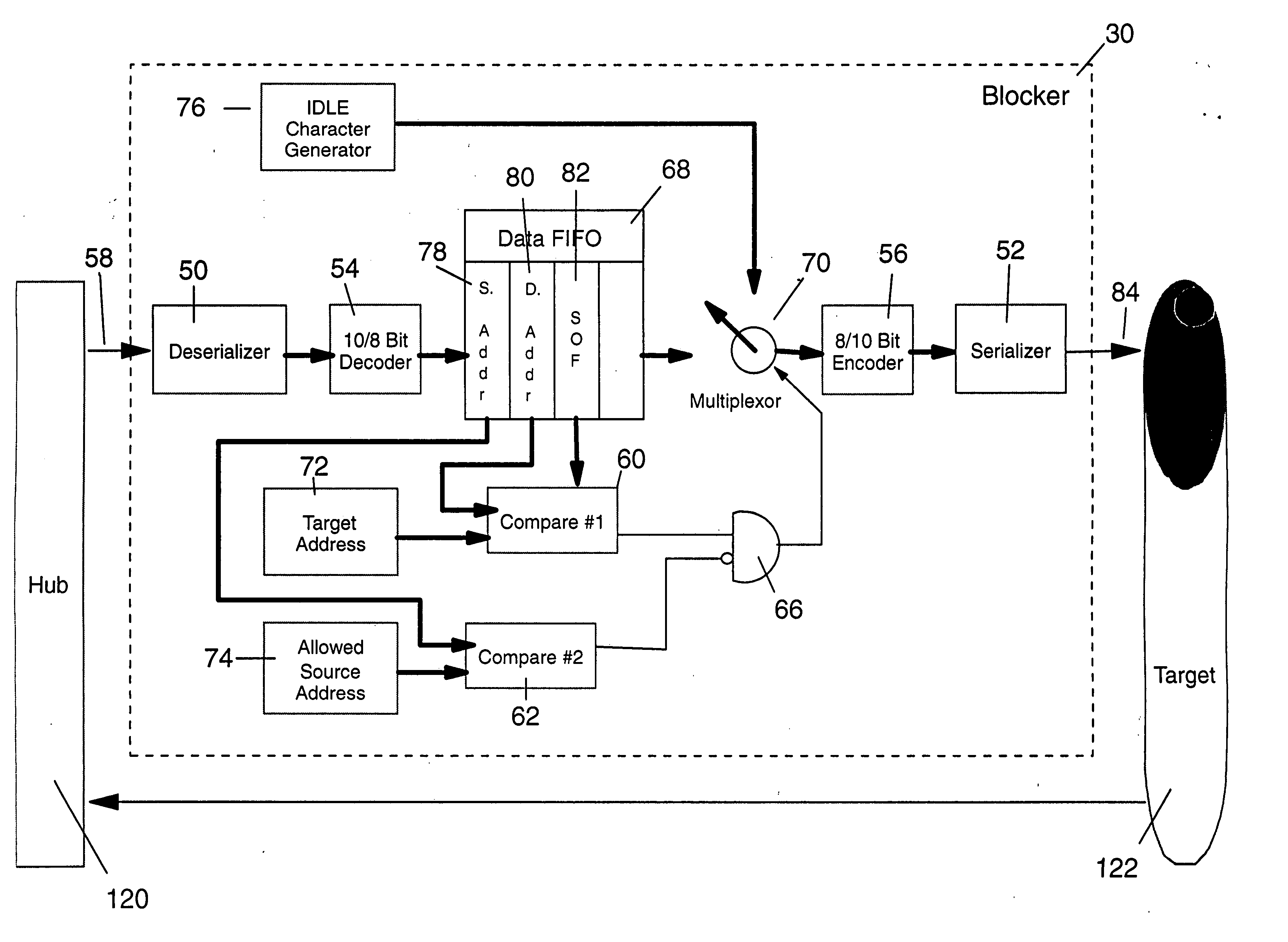
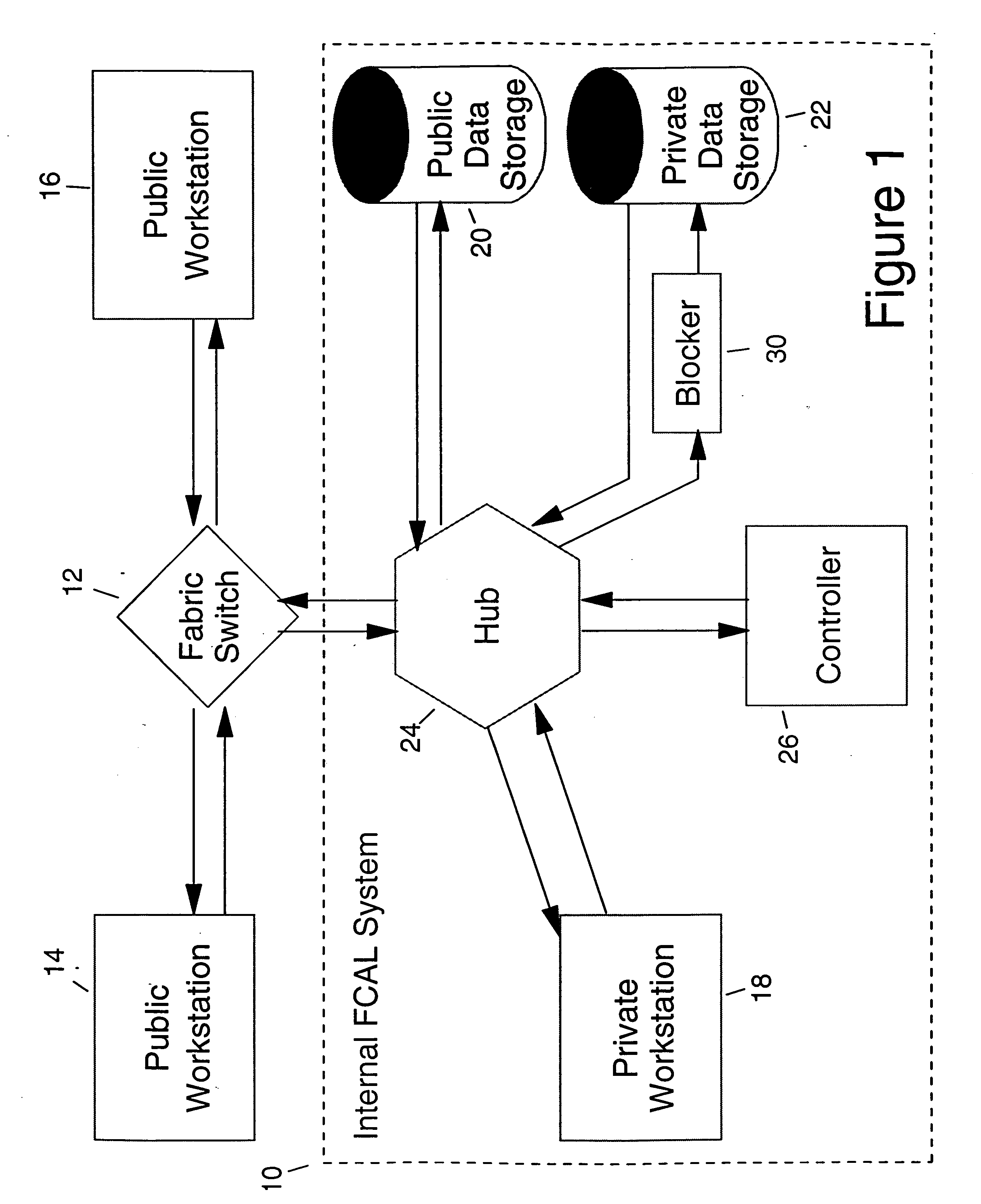
[0018] The invention concerns the address blocking in a fibre channel that blocks access by an unauthorized user to confidential data of a second user in a network. The frames of data being transmitted down the fibre channel is inspected incoming to the device that is to be protected. In one embodiment of the invention, the blocking device is placed between a private data storage system and the fibre switch of the user holding the confidential data in his private storage system. In the invention, the blocking device is placed between the fibre switch of the confidential data owner and the confidential owner's network adapter used to access the fibre channel network to the outside world. The blocker includes a comparator that checks the source and authorized addresses thereby permitting access to the owner's private data storage only to authorized users. The blocking device also checks the transmission of data from the private data storage back to the user and again compares the sour...
first embodiment
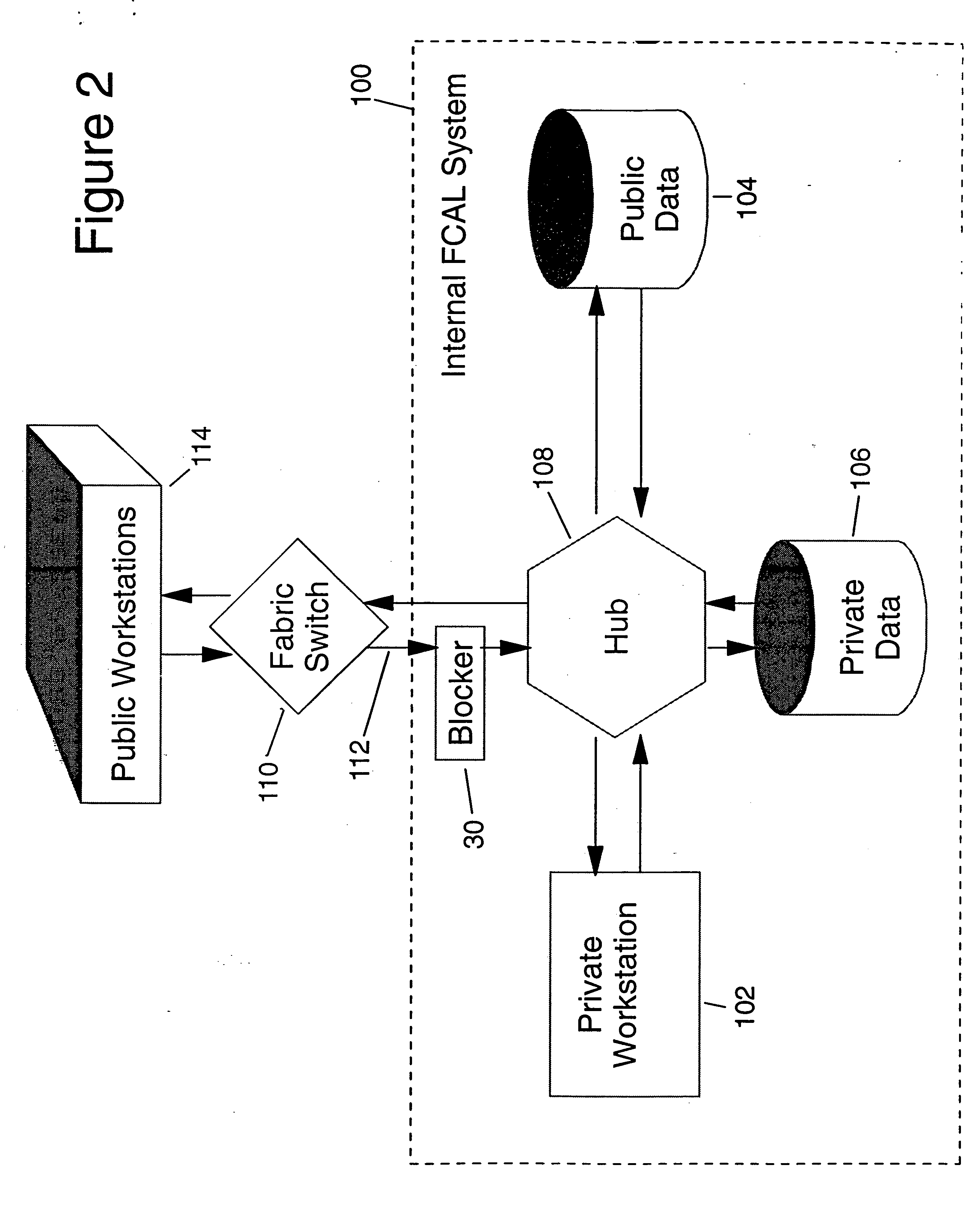
[0020] Referring now to FIG. 2, an internal FCAL system 100 is shown including a private workstation 102, a public data storage 104 and a private data storage 106 all interconnected to a FCAL loop technology in a hub 108. The blocker 30 of the present invention is shown positioned between a fabric switch 110 and the internal FCAL system 100 on an input fibre channel 112. The fibre switch 110 is shown interconnected through fibre channels to a plurality of public workstations 114. The fabric switch 110 represents an interconnection to many workstations and data storages all external to the internal FCAL system 100. In the embodiment shown in FIG. 2, the invention disclosed in blocker 30 is shown positioned between the incoming fibre channel 112 from the fabric switch 110 and intercepts the frames of data on the fibre channel directed towards the hub 108. In this embodiment, the invention is positioned between the FCAL target represented by the internal FCAL system 100 and the fabric ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com