System, method and computer program product for protecting software via continuous anti-tampering and obfuscation transforms
a technology of software protection and transforms, applied in the field of system, method and computer program products for protecting software via continuous anti-tampering and obfuscation, can solve the problems of software protection from unauthorized tampering, billions of dollars in revenue each year, and malicious attackers continue to thwart such checks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
examples and experimental
Results
[0104]Practice of the invention will be still more fully understood from the following examples and experimental results, which are presented herein for illustration only and should not be construed as limiting the invention in any way.
Example Nos. 1-16
[0105]See FIGS. 17-32, which pertain to specific exemplary (and non-limiting) embodiments as they may pertain to the approach illustrating the present invention computer method, system or computer program product embodiments of FIG. 1-16, respectively.
example no.17
Example No. 17
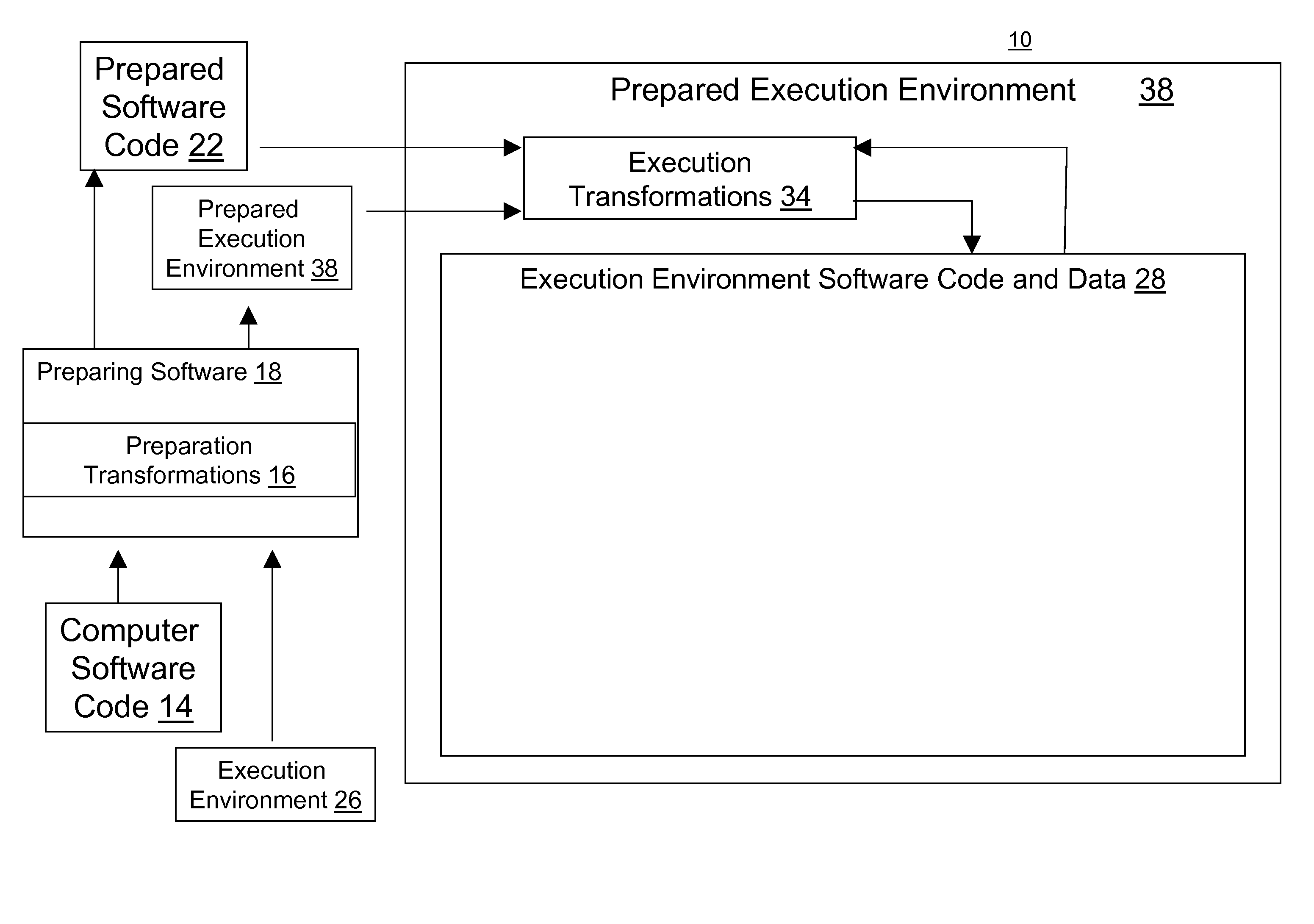
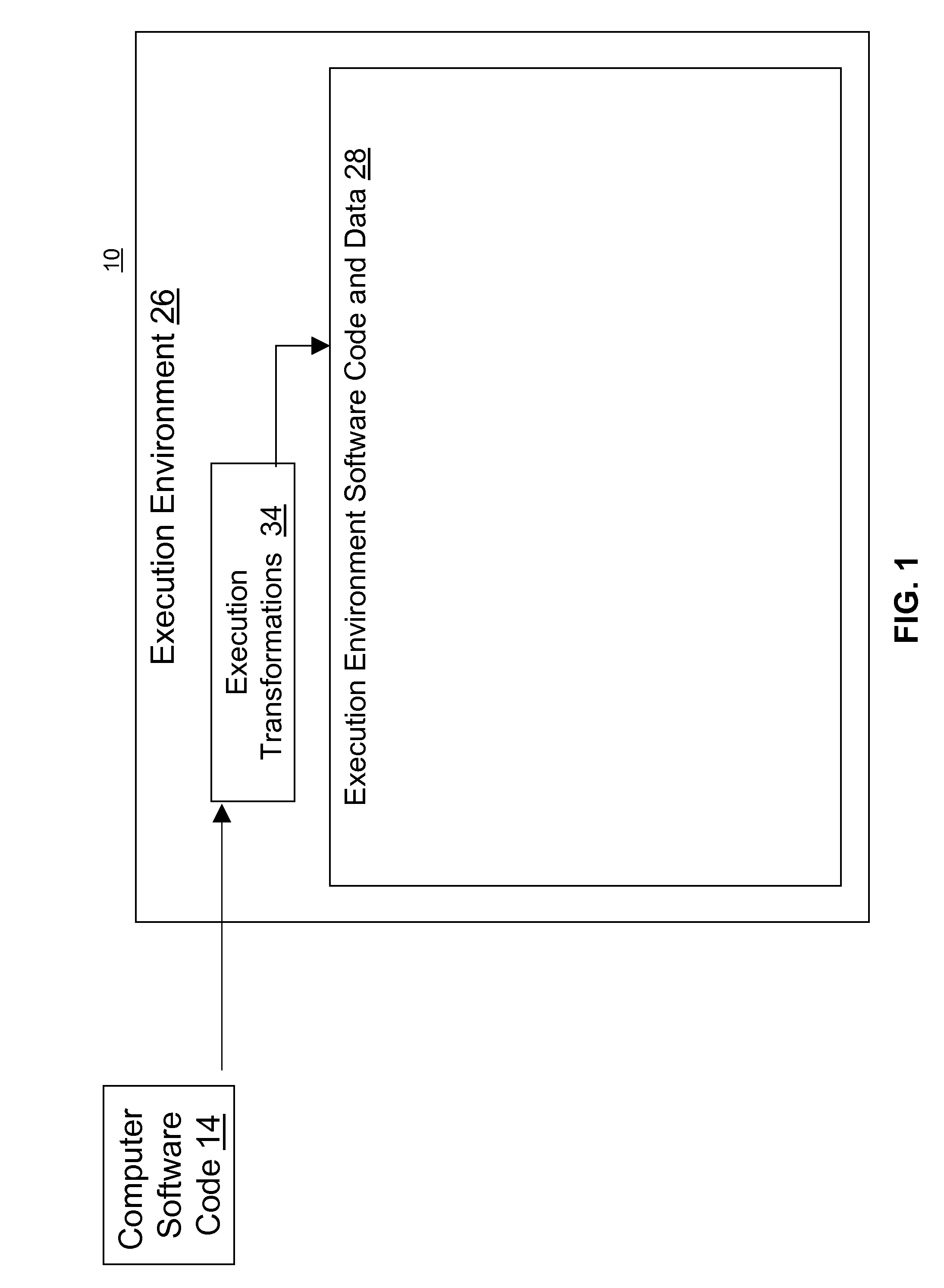
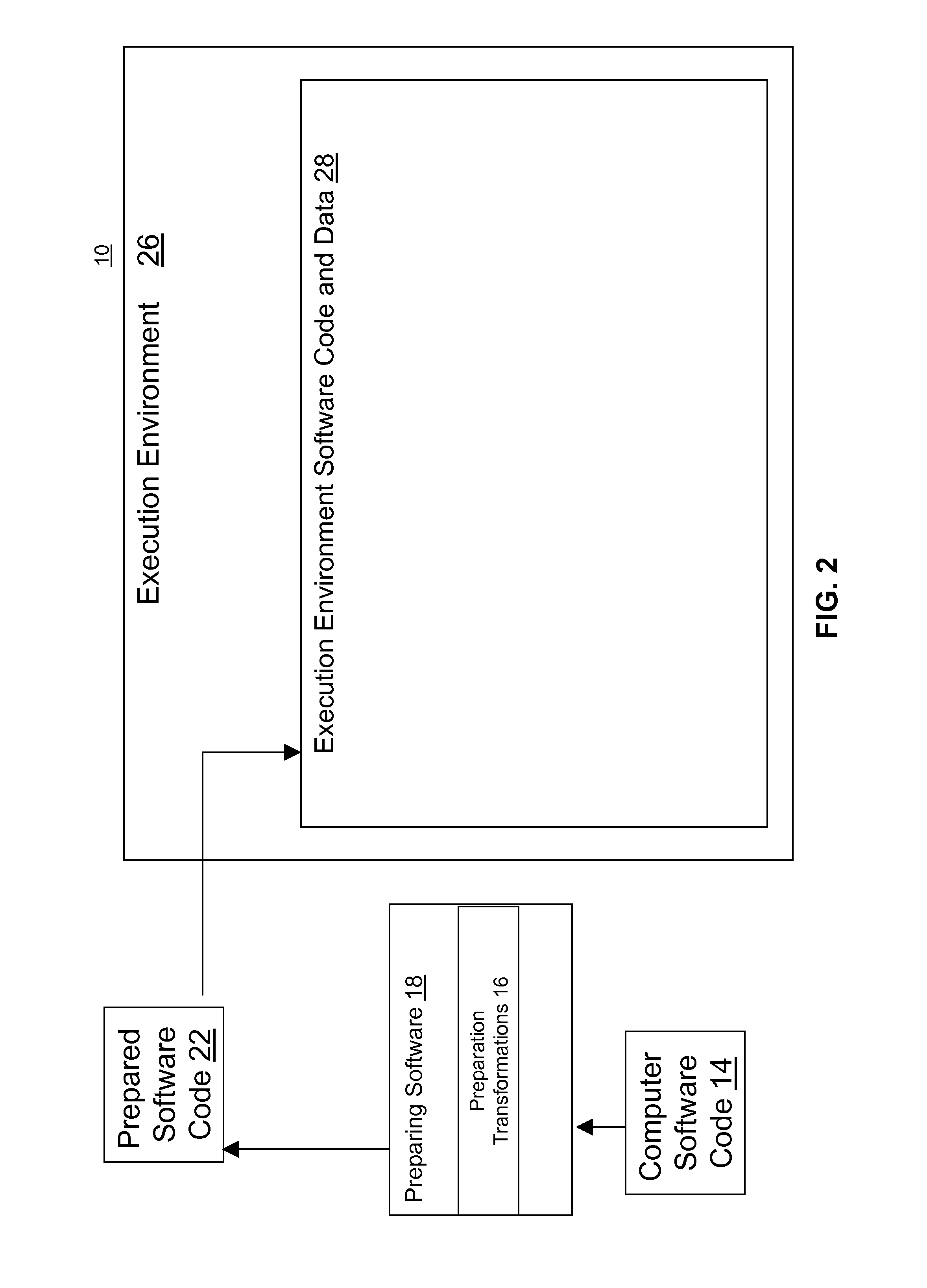
[0106]An aspect of the embodiment of the present invention provides a way to protect an application using a virtual machine and a variety of mechanisms to make sure that the virtual machine cannot be modified. First, the application's code segment is encrypted. The encrypted text has code to checksum itself and the virtual machine. As the application requests new fragments to execute, the virtual machine decrypts portions of the application's code segment, applies anti-tampering (including dynamic self-checksumming) and obfuscation (including dynamic resistance to disassembly, dynamic control flow graph hiding, dynamic instruction isomorphisms, dynamic dead code, and dynamic code scheduling) techniques to prevent revealing the application's instructions during execution. Combined with frequent flushing of the virtual machine's fragment cache, this invention provides significantly stronger protection than statically-applied anti-tampering and obfuscation alone.
[0107]Mos...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com