Data Transmission Security Improvements
a data transmission and security improvement technology, applied in the field of secure data transmission, can solve the problem that the eavesdropper cannot accurately distinguish between extraneous information and communication information, and achieve the effects of convenient, effective and relatively simple, and relatively quick recovery at the receiving terminal
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032]A more detailed description of specific embodiments of the present invention is set out below with reference to the above-described figures.
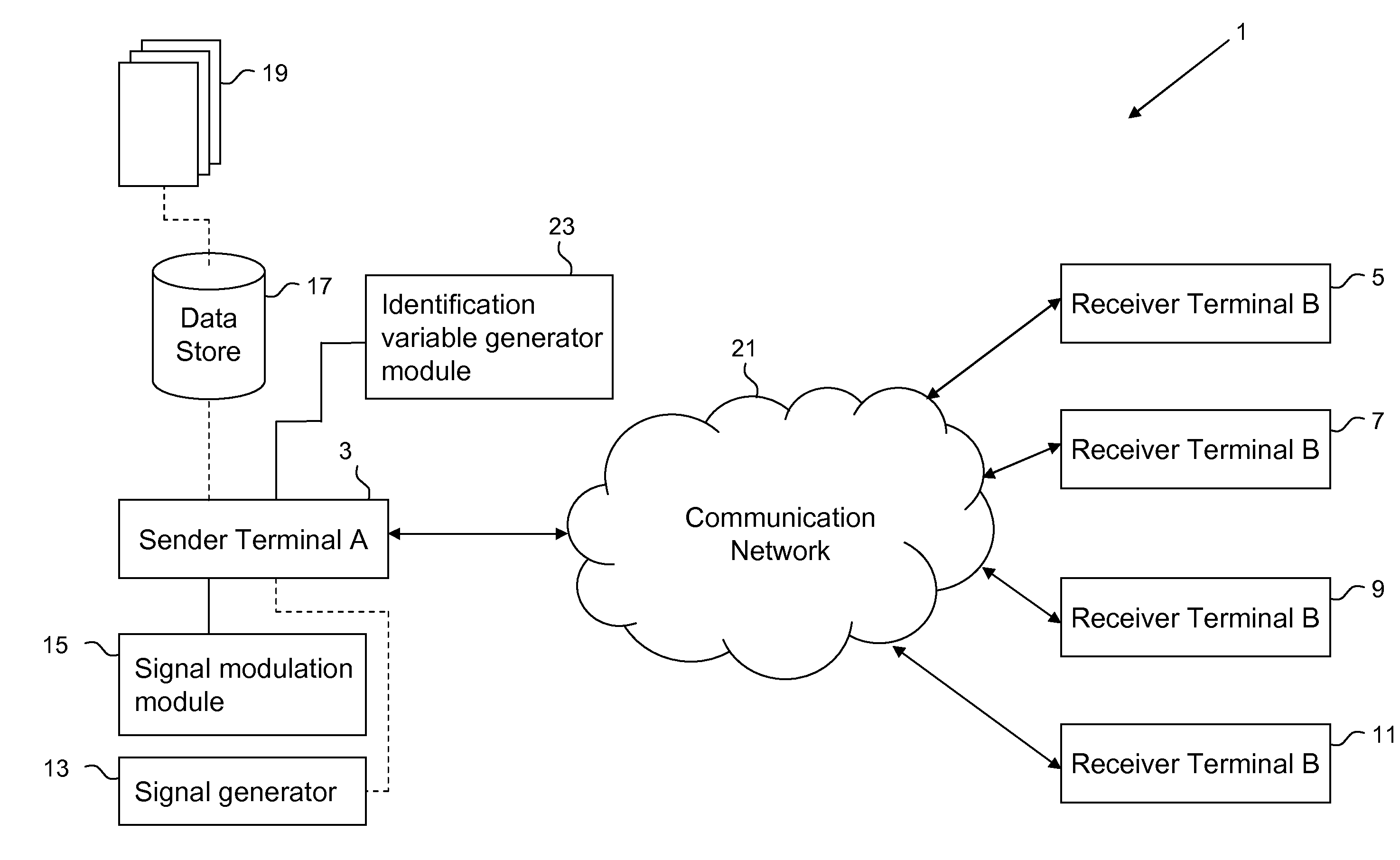
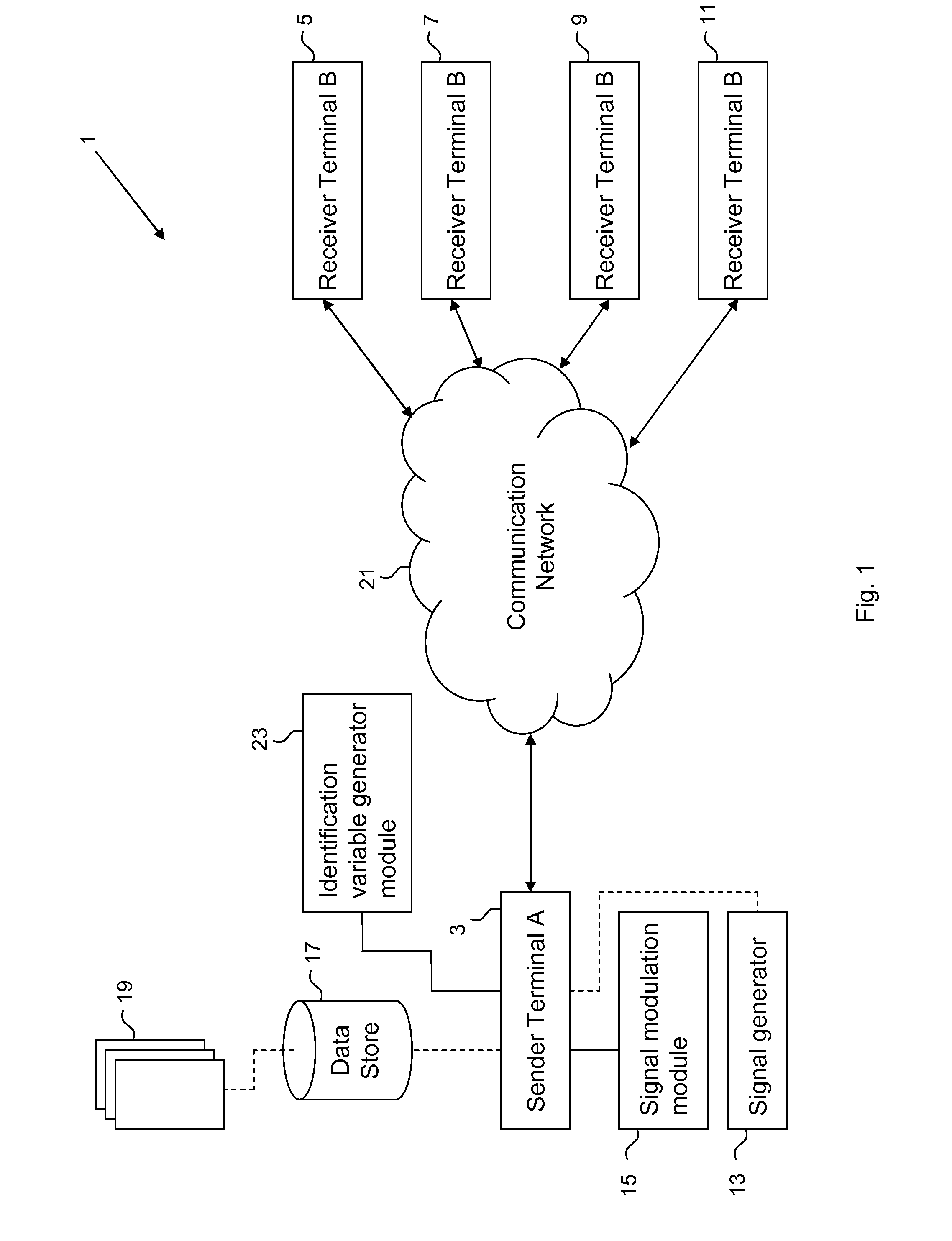
[0033]FIG. 1 is a schematic overview of a system 1 for transmitting a secure data signal comprising confidential communication information combined with extraneous information—the communication information is effectively concealed within the extraneous information. The data signal is transmitted from a sender to one or more recipient's in accordance with an embodiment of the present invention. The system 1 comprises a sender terminal 3 and one or more receiver terminals 5, 7, 9, 11. The sender terminal 3 (also referred to as terminal A in the ensuing description) may further comprise a signal generator 13, arranged to generate a carrier signal; a signal modulation module 15 for modulating a selected signal; and a data store 17. The data store 17 comprises a plurality of data 19 associated with communication information and extraneous infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com