Security for cloud systems and virtualization cloud systems, mobile cloud systems and mobile virtualization cloud systems, and computer clusters and mobile device clusters
a cloud storage environment and cloud technology, applied in the field of cloud storage and virtualization cloud systems, mobile cloud systems and mobile virtualization cloud systems, computer clusters and mobile device clusters, can solve the problems of unresolved need, inability to ensure the integrity, confidentiality, and privacy of critical business information deployed in cloud storage environments, and online fraud has grown into a sophisticated underground economy that requires infrastructure on a massive scal
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
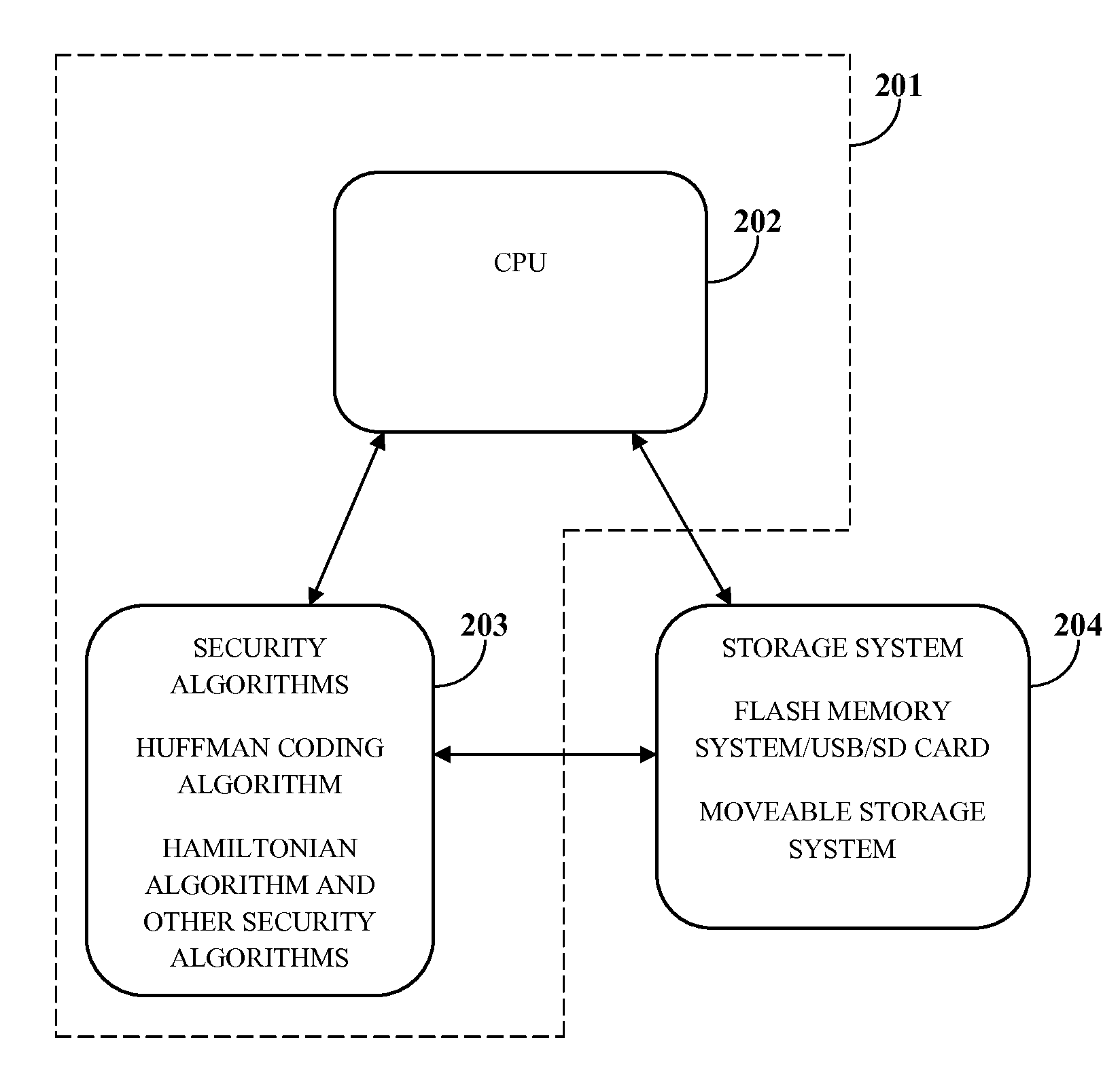
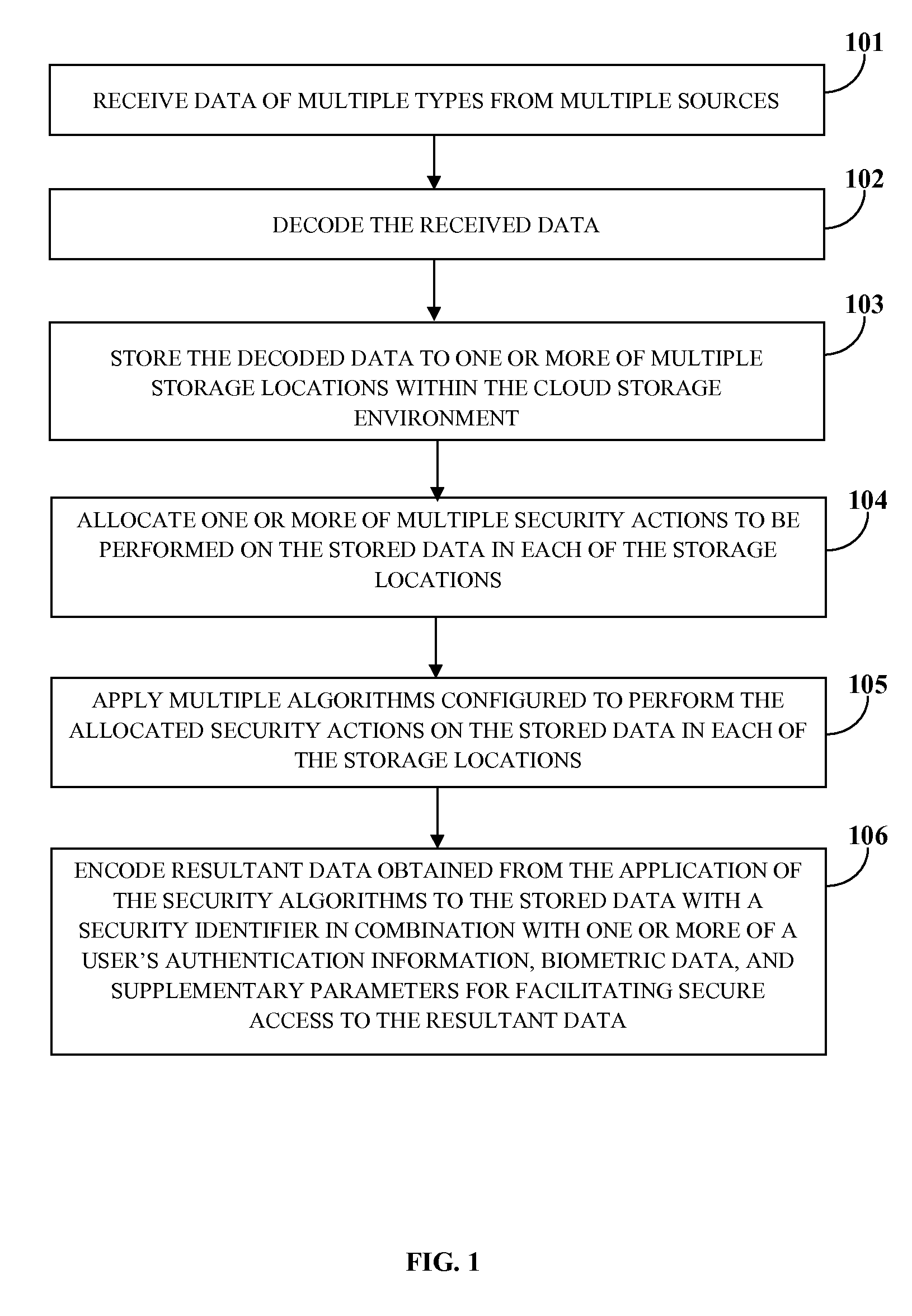
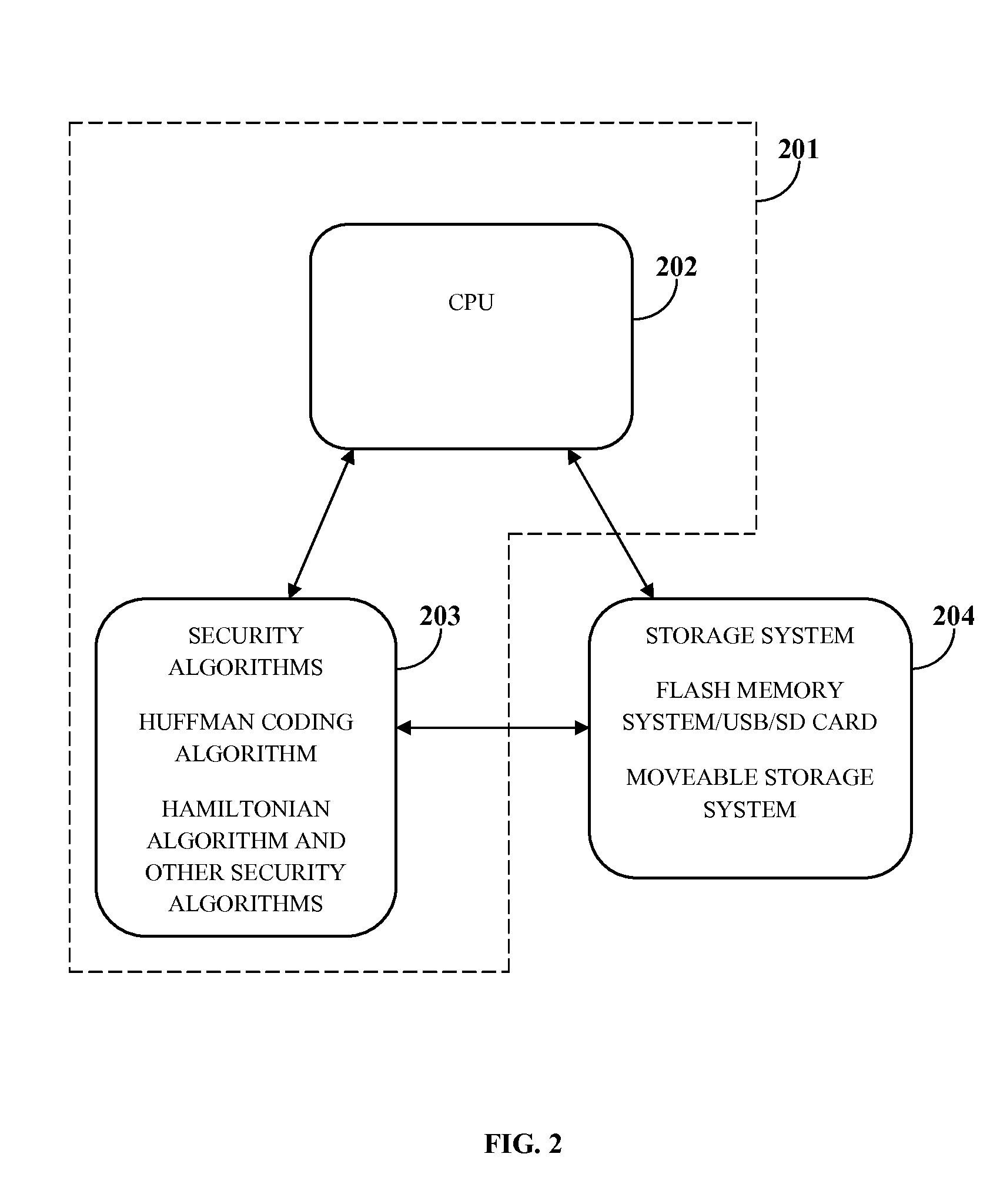
[0024]FIG. 1 illustrates a computer implemented method for securing data in a cloud storage environment. As used herein, “securing data” refers to protecting data, for example, medical information, legal information, financial information such as certified public accountant (CPA) information, personal information, etc., from unwanted actions by unauthorized users. Also, as used herein, “cloud storage environment” refers to a data storage environment where data from different computing devices such as personal computers, mobile devices, etc., is stored in cloud computing systems comprising, for example, virtualization cloud systems, mobile cloud systems, mobile virtualization cloud systems, computer clusters, mobile device clusters, etc. The computer implemented method disclosed herein employs a cloud security system comprising at least one processor configured to execute computer program instructions for securing data in a cloud storage environment. In an embodiment, the cloud secur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com