Method for protecting chip internal information security based on JTAG port control
A technology for internal information and port control, applied in computer security devices, internal/peripheral computer component protection, instruments, etc., can solve problems such as non-compliance, long cycle, difficult embedded software development, etc., to facilitate online upgrades, guarantee safe effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
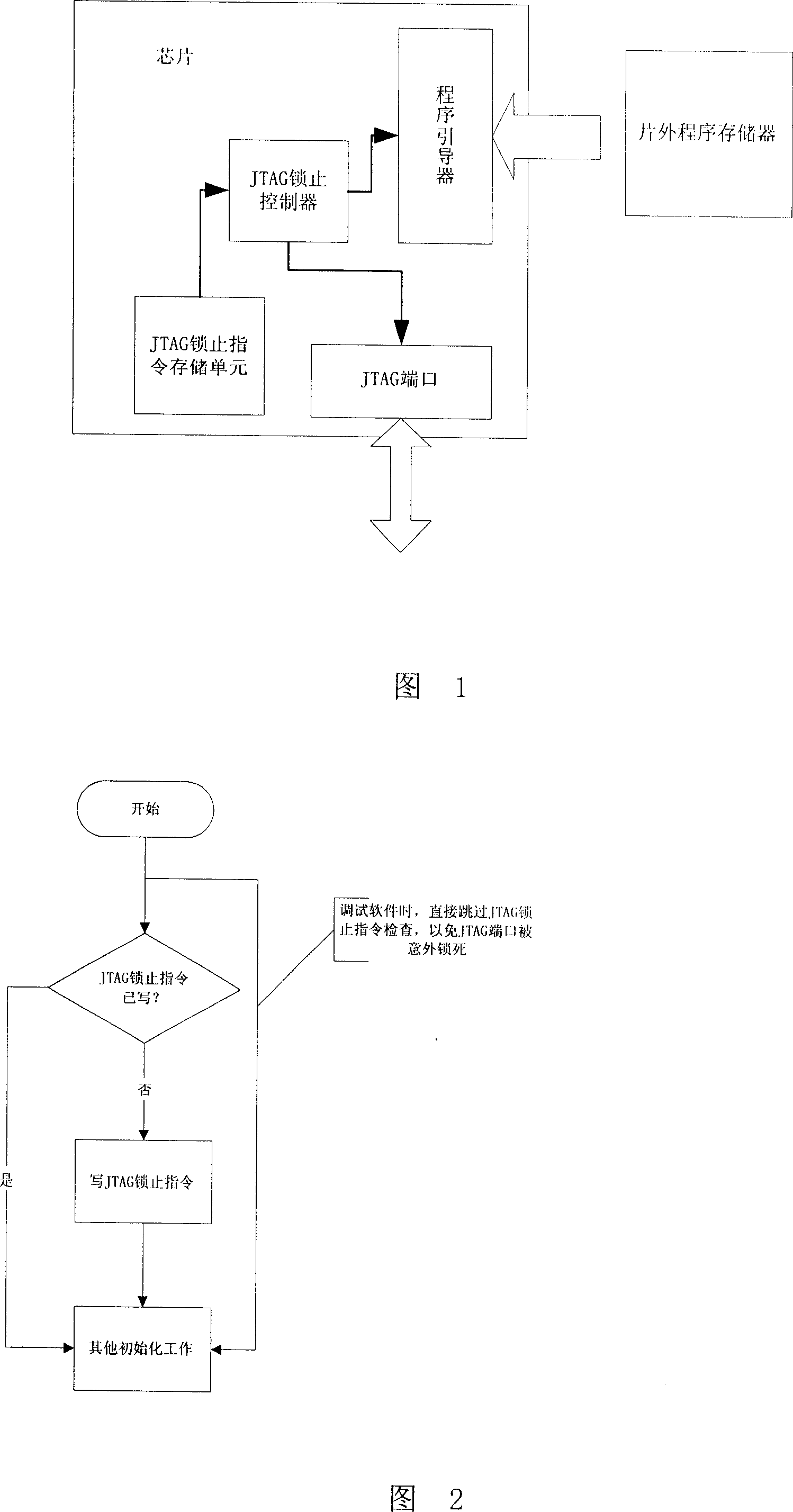
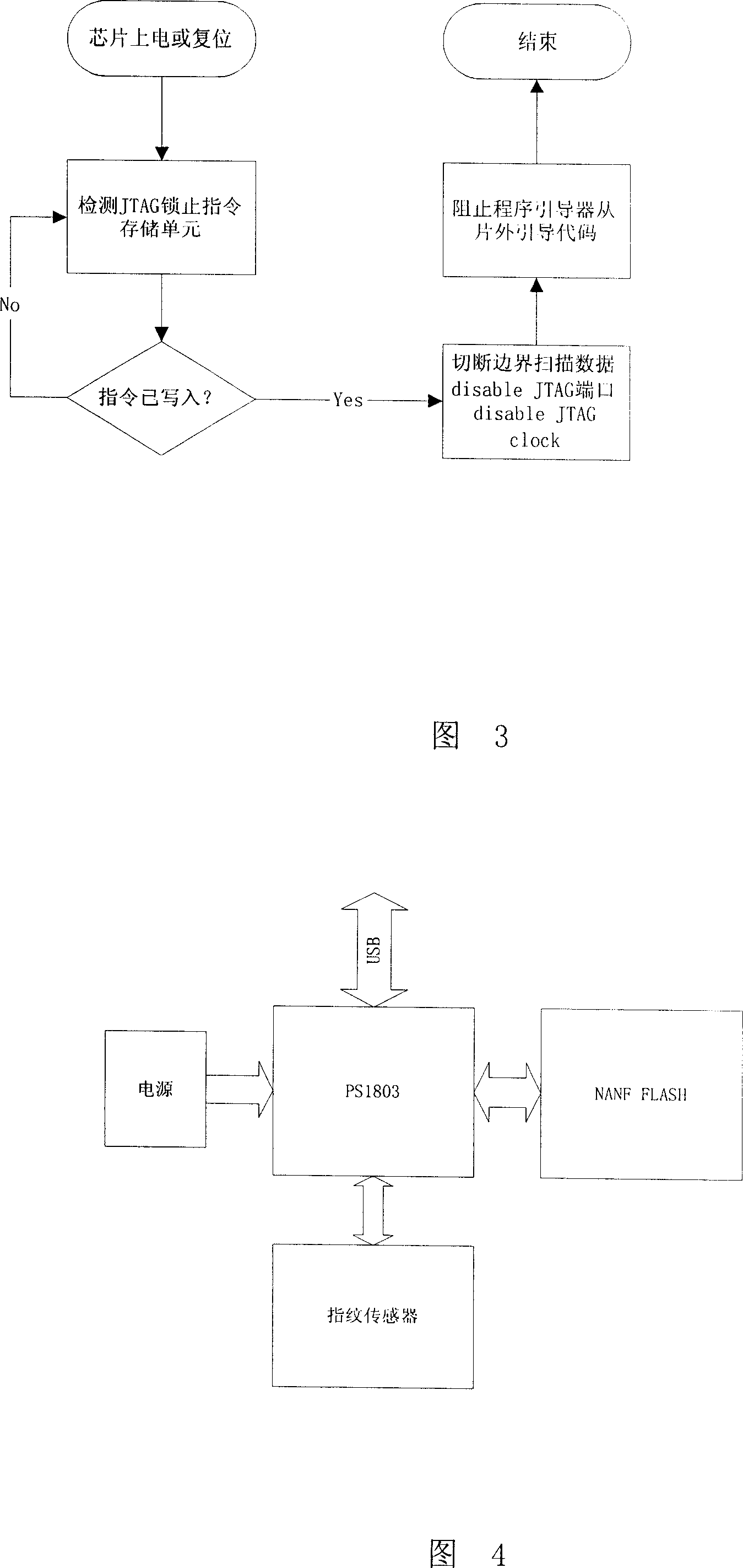
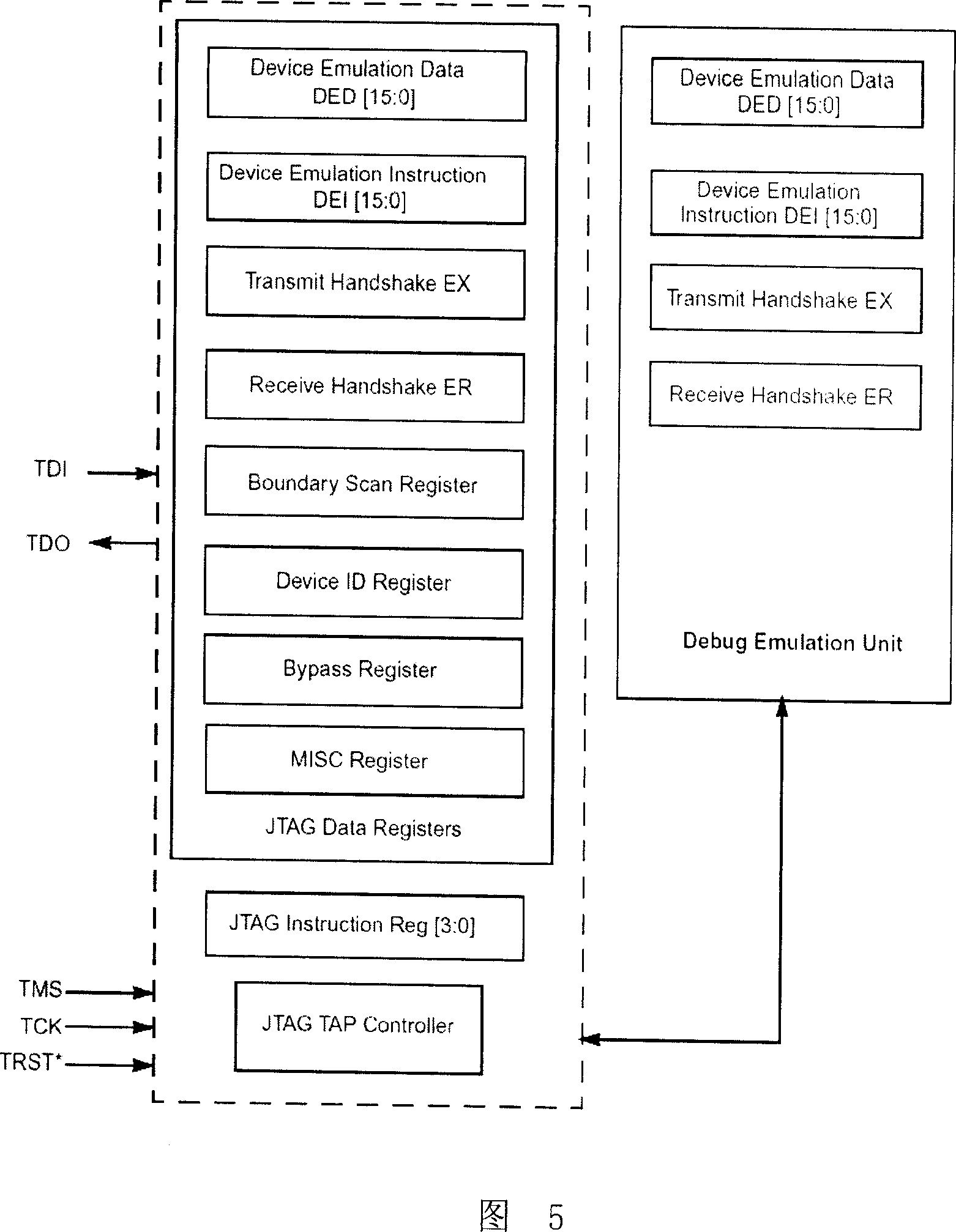
[0039] The present invention will be further described below in conjunction with the accompanying drawings.
[0040] The specific realization and the effect of realization of the present invention will be described below by taking the PS1803DSP safety microcontroller chip as an example.
[0041] PS1803 is a DSP microcontroller designed on the basis of ZSP400 core. It integrates 128K bytes of embedded FLASH, 156K bytes of RAM, and also integrates USB port, UART, SPI, I2C port, and NAND FLASH interface , can be attached to fingerprint sensor, NANDFLASH and other peripheral devices at the same time. As long as the firmware is written into the on-chip FLASH, a dedicated SOC can be constructed.
[0042] The entire set of software of the fingerprint electronic signature device is very complicated, including not only encryption and decryption algorithms, but also image processing and fingerprint recognition algorithms, as well as the simulation and control of U disk. Fingerprint el...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com