Data-base malevolence transaction method and system thereof
A transaction processing and database technology, applied in the field of enhancing database system security, can solve problems such as low response efficiency and weak attack security, and achieve the effect of ensuring correctness and availability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
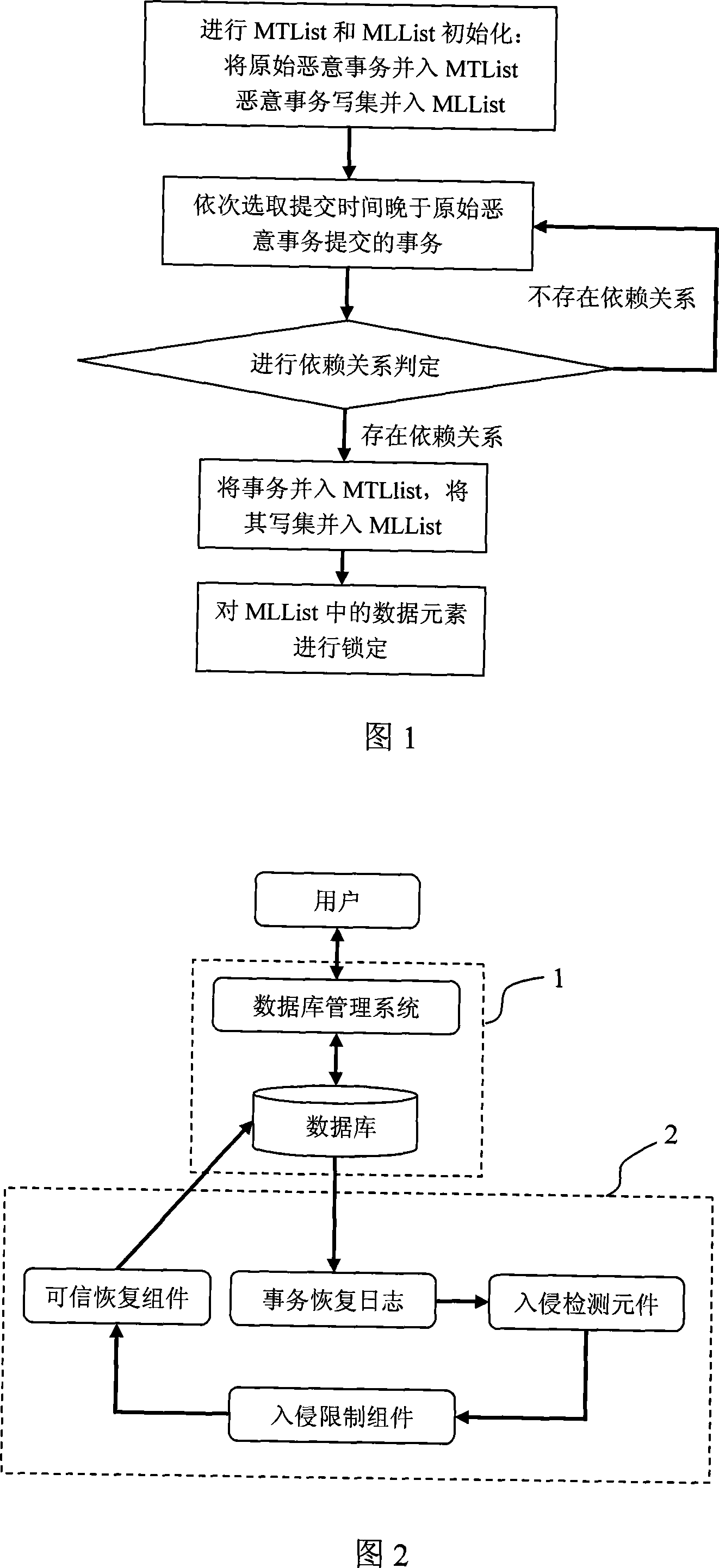
[0054] The present invention will be described in further detail below with reference to the accompanying drawings and an example, but the scope of the present invention is not limited in any way.
[0055] In this example, it is assumed that the database only includes 5 data elements, and the value of each data element in the initial state is 2:
[0056] Data Element Identifier
[0057] Assume that the user submits four transactions to the database through the database management system: T1, T2, T3 and T4, and each transaction performs the following operations, as listed in the following table:
[0058] transaction ID
[0059] As shown in Figure 2, the database generates four transaction recovery log records for the above four transactions respectively. The transaction recovery log libraries are listed below:
[0060] transaction ID
[0061] Assume that at time 2007-10-26, 12:04, the intrusion detection component detects that T1 is an original ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com