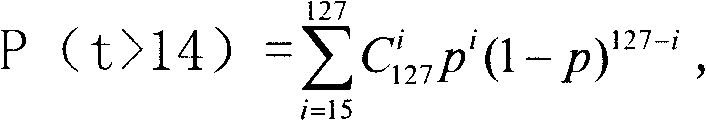Method for generating and authenticating frailty watermark based on error correction encoding
A fragile watermark and authentication method technology, applied in the field of image processing, can solve the problems of no way to accurately locate the tamper position, insufficient anti-tamper performance, no repair, etc., to facilitate decoding error correction, increase security, and simplify parameter management Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
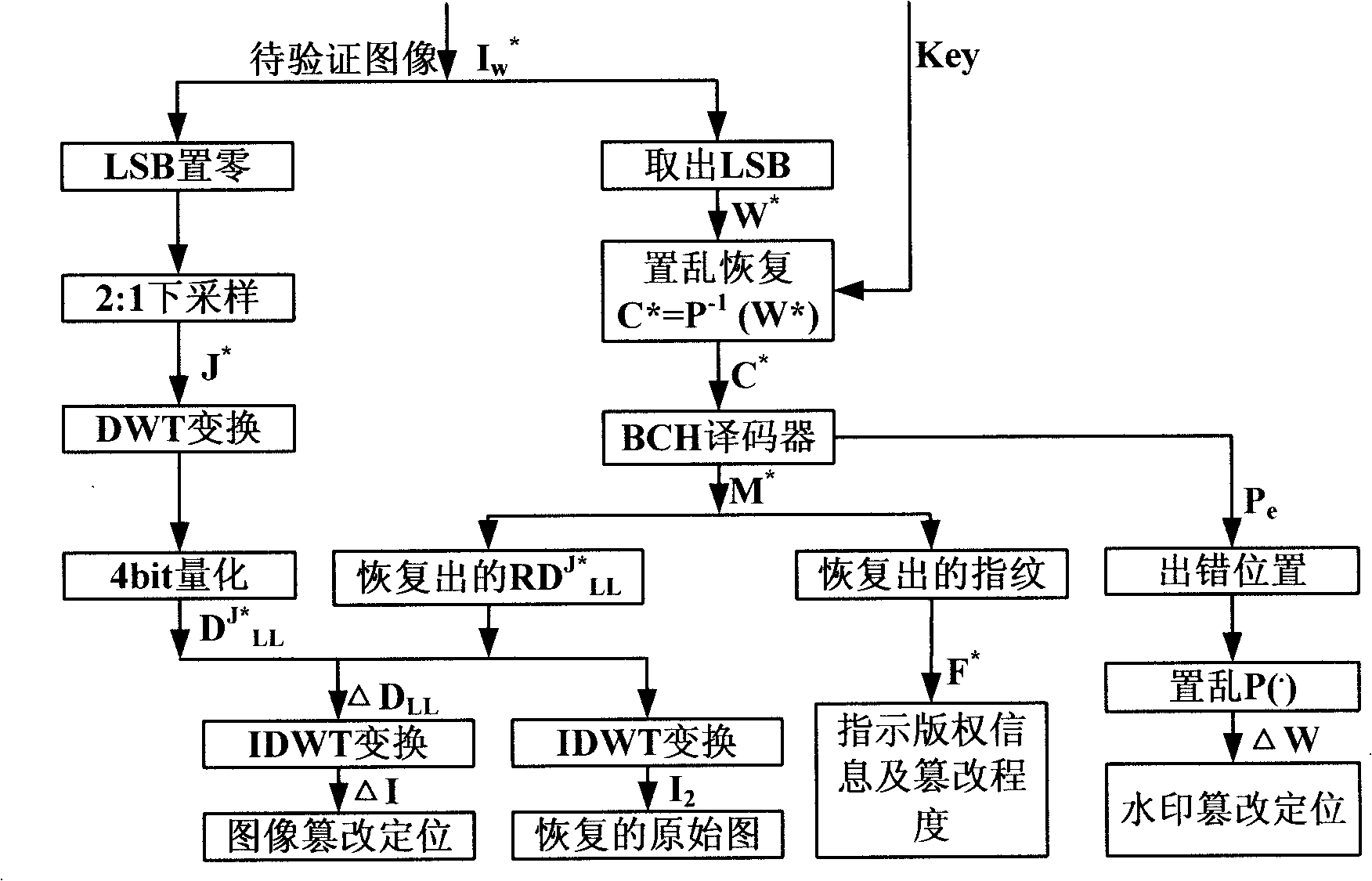
[0035] A fragile watermark generation and authentication method based on error correction coding includes a fragile watermark generation method and a fragile watermark authentication method, the specific content and steps are as follows:
[0036] 1. Watermark generation and embedding:
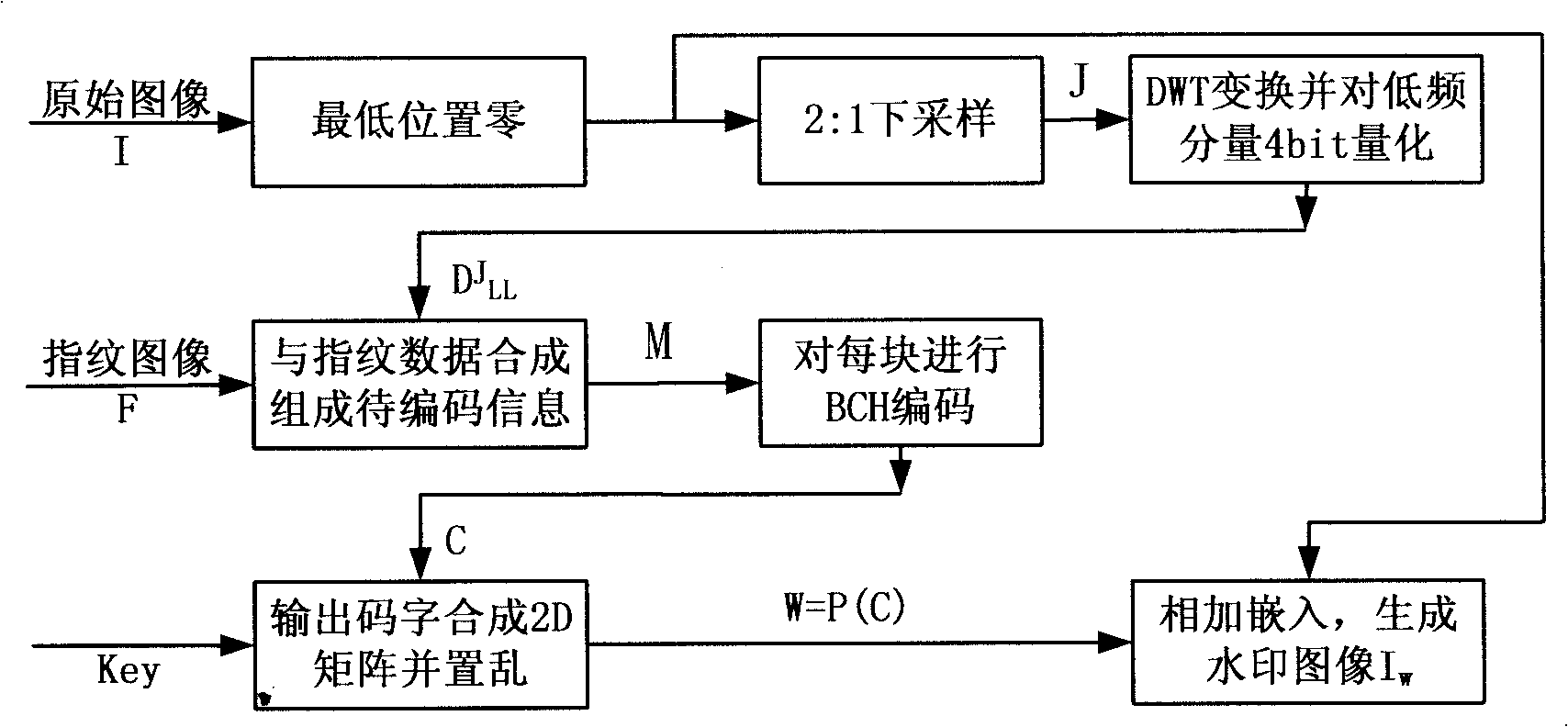
[0037] Such as figure 1 As shown, the watermark generation and embedding process is:
[0038] 1. Do a 2:1 downsampling after the lowest position of the original image is zeroed to generate a reduced image J whose length and width are respectively 50% of the original. Perform two-dimensional one-level discrete wavelet transform (DWT) on the reduced image J, decompose to obtain wavelet coefficients {LL, LH, HL, HH}, and perform 4-bit quantization on its low-frequency coefficient LL to form a binary bit stream D J LL . For the first-level wavelet transform, the maximum value of the original image is 255, and the maximum wavelet coefficient is 512, so quantization with a step size of 32 can ens...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com