Method for implementing transport layer safety of SIP network based on sharing cryptographic key
A transport layer security and shared key technology, applied in the field of transport layer security implementation in SIP networks, can solve problems such as implementation difficulties, dropped messages, communication failures, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
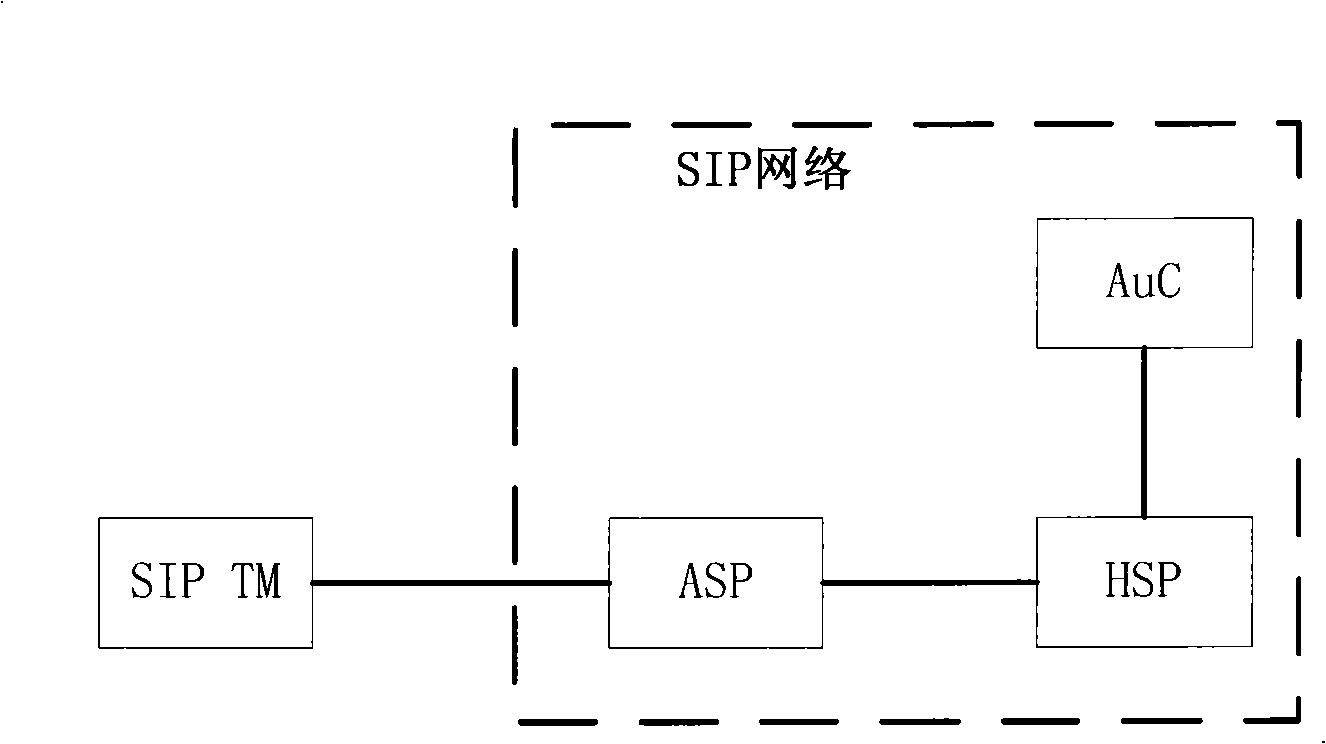
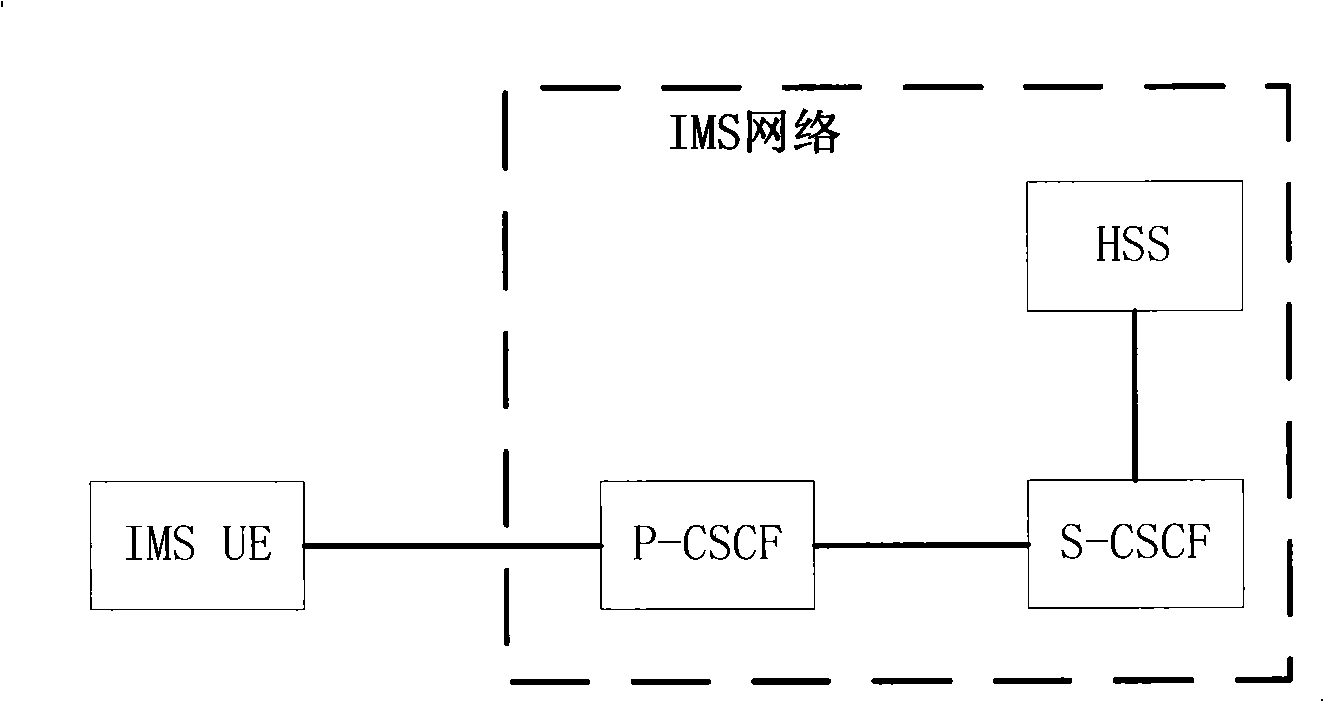
[0080] This embodiment takes the IMS network as an example, figure 2 Schematic diagram of the system architecture for realizing SIP transport layer security, where SIP TM takes IMS UE (User Equipment) as an example; ASP takes P-CSCF (Proxy Call Session Control Function) in IMS network as an example, between IMS UE and P-CSCF The transport layer security connection is established between CSCFs; the HSP takes the S-CSCF (Serving Call Session Control Function) in the IMS network as an example; the AuC takes the home subscriber server HSS in the IMS network as an example.
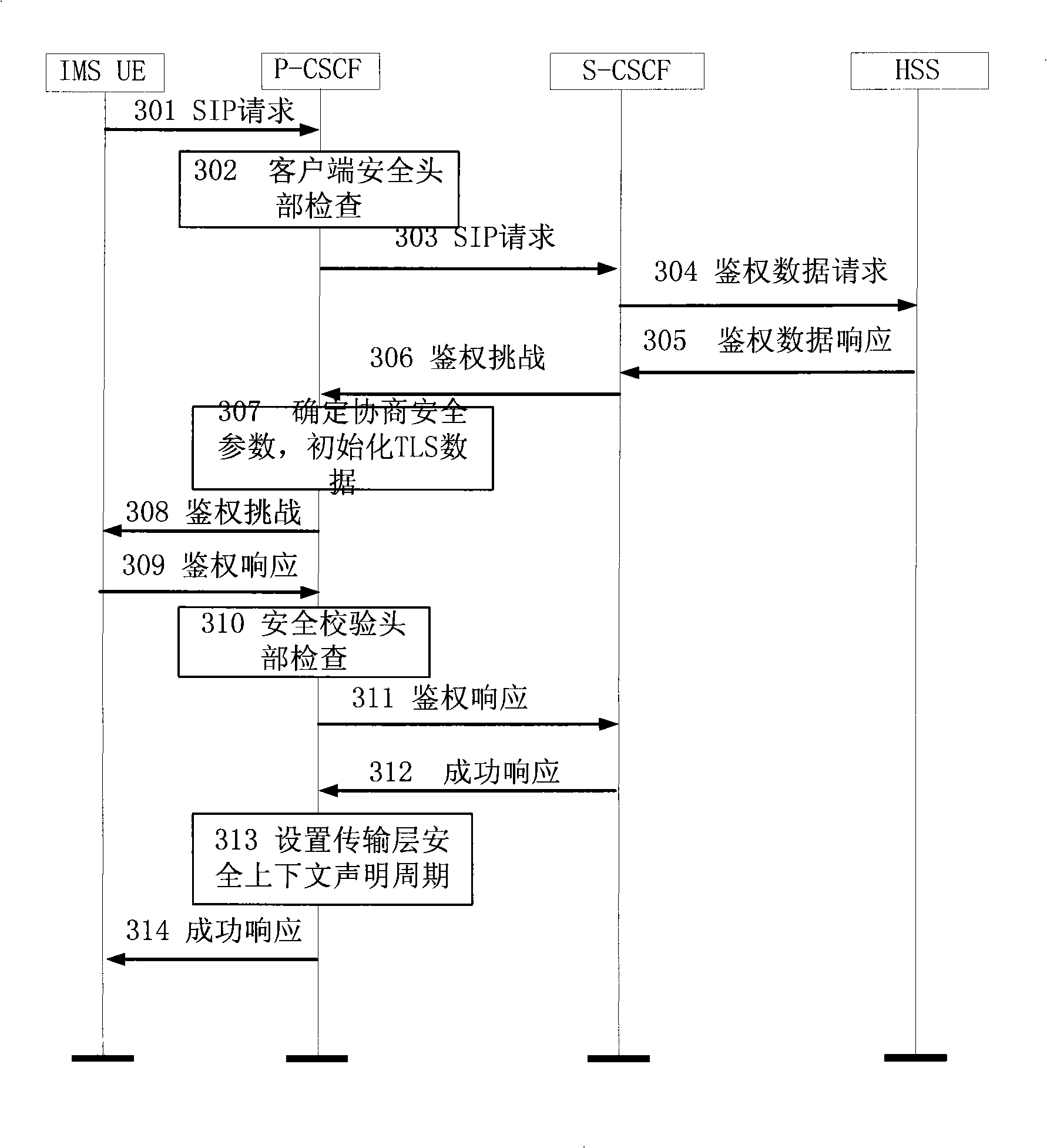
[0081] In this embodiment, take the IMS network as an example to realize the flow chart of TLS negotiation, as shown in image 3 As shown, there may be other IMS network elements such as I-CSCF (inquiry call control function) between P-CSCF and S-CSCF in the figure, but this embodiment has no impact and is ignored in the figure. The process includes the following steps:
[0082] Step 301, the IMS UE selects a...
no. 2 example
[0099] Figure 4 Shows the embodiment of the transport layer security negotiation in the ordinary SIP network (referring to the network using SIP as the control protocol except softswitch and IMS), the SIP server in the figure includes figure 1 ASP and HSP in the general framework, process and image 3 basically the same, except image 3 The functions performed by the P-CSCF and the S-CSCF respectively in this embodiment are independently performed by the SIP server.
[0100] As shown, the process includes the following steps:
[0101] Step 401, the SIP terminal initiates a request to the SIP server, and the SIP message contains one or more Security-Client headers, one of which indicates the supported transport layer security parameters, including transmission type, encryption, integrity protection algorithm, client and listening port number, etc.;
[0102] Step 402, the SIP server receives the request, checks whether the algorithm indicated by the Security-Client header i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com