Network resource access control method in reliable access
A technology for access control and network resources, applied in the field of network communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
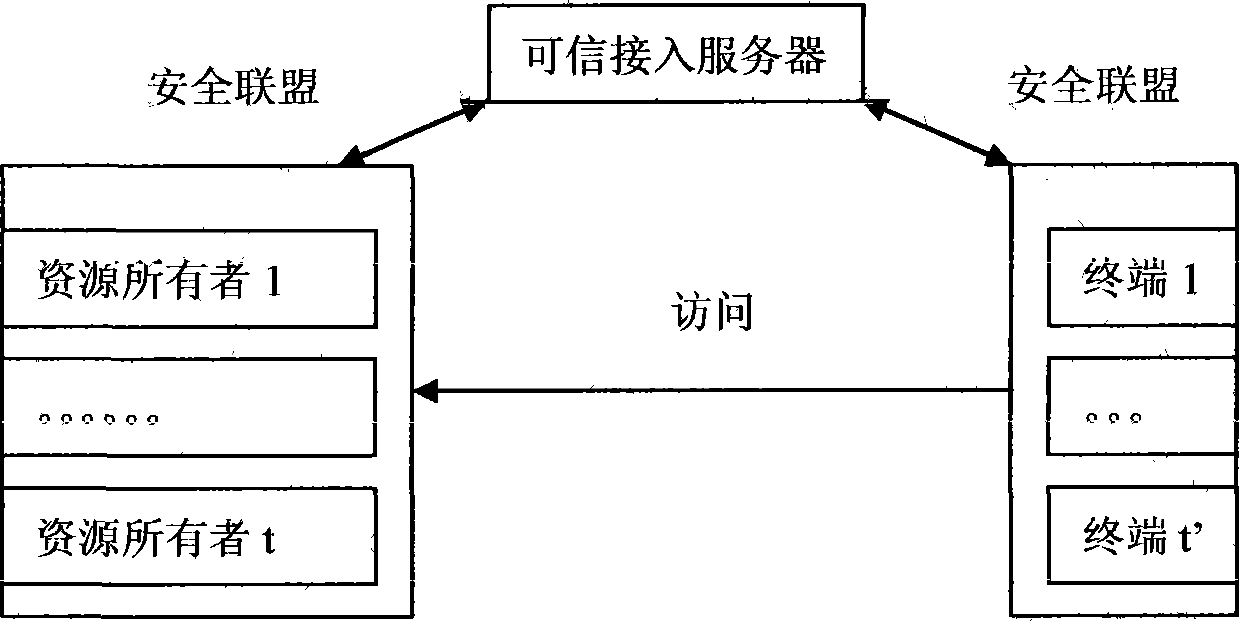
[0030] Such as figure 1 As shown in the network resource access control model diagram, the trusted access server is the security center of the entire system, and is also a network entity trusted by resource owners and terminals, responsible for the management and distribution of security materials.
[0031] To implement this method, a security association must be established between the trusted access server, the resource owner and the terminal, and the trusted access server distributes key materials to the resource owner and the terminal under the protection of the security association. The trusted access server assigns a key material to each resource owner, and temporarily generates an access token for the terminal to access the corresponding resource according to the credibility of the terminal. Only terminals holding valid tokens can access specific resources.
[0032] The invention proposes a network resource access control method in trusted access, the main steps of whic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com