Method for implementing coexistence of various cryptographic algorithm in wireless LAN
A technology of wireless local area network and encryption algorithm, which is applied in the field of realizing the coexistence of multiple encryption algorithms of wireless local area network, which can solve the problems of the wide application limitation of wireless local area network devices and the inability of wireless local area network devices to communicate with each other, and achieve the effect of fast encryption and good versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
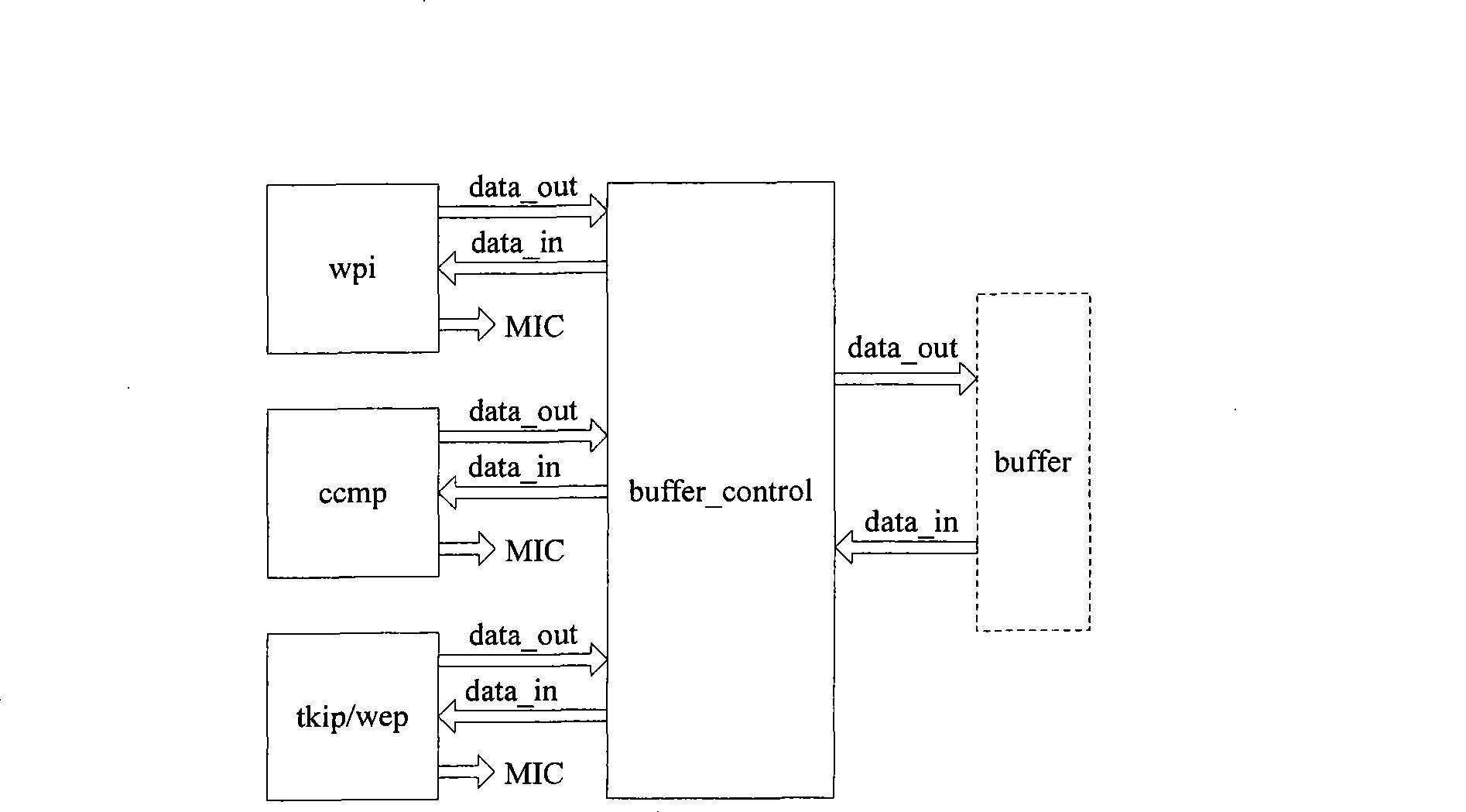
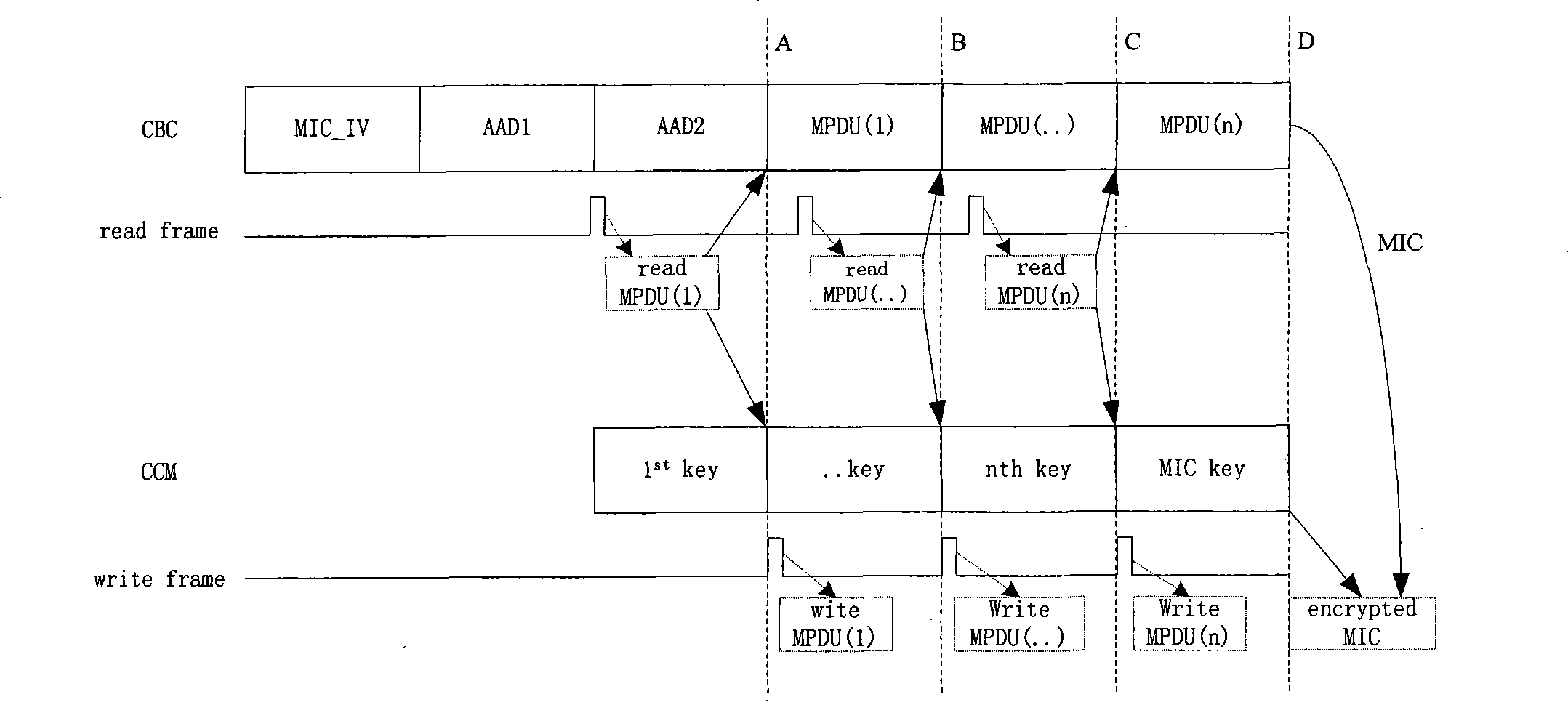
[0011] The present invention will be described in detail below in conjunction with the accompanying drawings. In order to better illustrate the intent of the present invention, the specific implementation of the present invention takes security protocols wapi and 802.11i as examples. The algorithm for data encryption and integrity verification in the wapi security protocol is wpi, the algorithm for data encryption and integrity verification in the 802.11 protocol is the wep encryption algorithm, and the algorithm for data encryption and integrity verification in 802.11i is tkip (an upgraded version based on wep) and ccmp.
[0012] The invention provides a method for realizing the coexistence of multiple encryption algorithms in the wireless local area network, in order to realize the dual-mode of the wireless local area network equipment and improve its versatility. The invention includes a structure for realizing the coexistence of multiple encryption algorithms and a method...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com