Authentication method by broadcast signature and ciphering
An authentication method and user key technology, which is applied in the field of broadcast signcryption authentication, can solve the problems of high computational cost, information confidentiality, authentication and non-repudiation, and information confidentiality and authentication. Separation and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention is described in further detail below in conjunction with accompanying drawing:
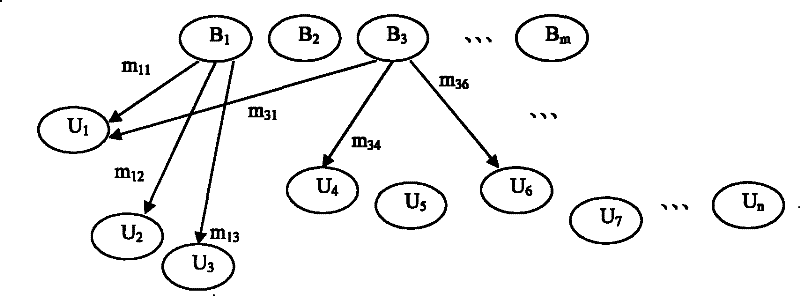
[0026] Different from the point-to-point information transmission method, the method of the present invention broadcasts the sign-encrypted video, audio, streaming media data and other message content to a specific user group through broadcasting, and the user decrypts the message through the key, and can To authenticate the message, its system structure is as follows figure 1 shown, where B 1 , B 2 ,......,B m For broadcast center, U 1 , U 2 ,......, U n For users (receivers), broadcast center B 1 and B 2 For example, B 1 message m 11 , m 12 , m 13 Respectively signcrypt broadcast to user U 1 , U 2 , U 3 , B 3 message m 31 , m 34 , m 36 Respectively signcrypt broadcast to user U 1 , U 4 , U 6 ; This broadcasting method can make full use of communication bandwidth, save costs, and greatly improve communication efficiency.
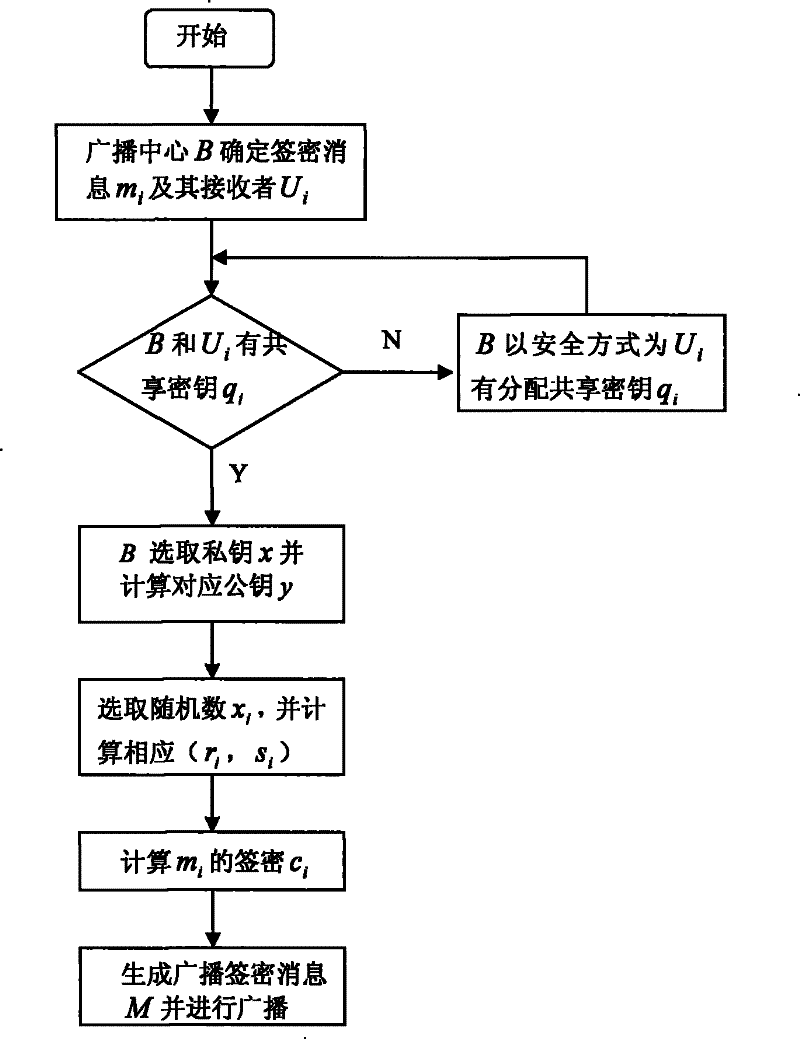
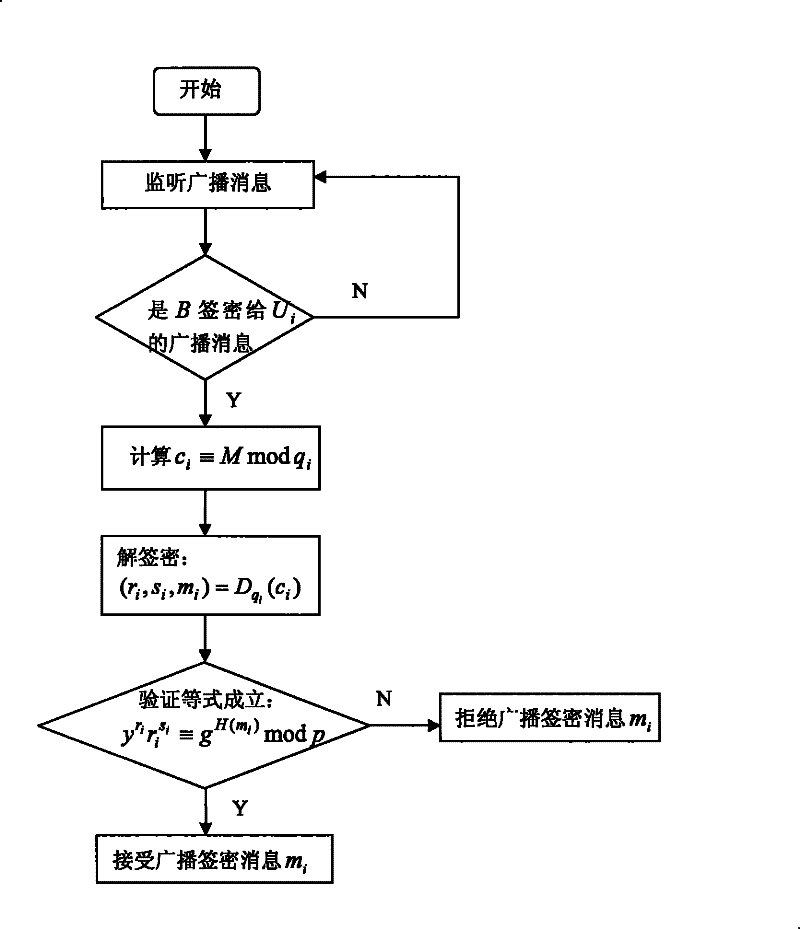
[0027] The broadcast si...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com