Legitimacy confirmation system, legitimacy confirming method, information processing card, confirming device and authentication device
A technology for inspection systems and inspection equipment, applied in digital data authentication, data processing applications, computer security devices, etc., can solve problems such as improper use of passwords, users' inability to determine unauthorized terminals, stolen passwords, etc., to prevent leakage Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0107] (The structure of the authorization system)
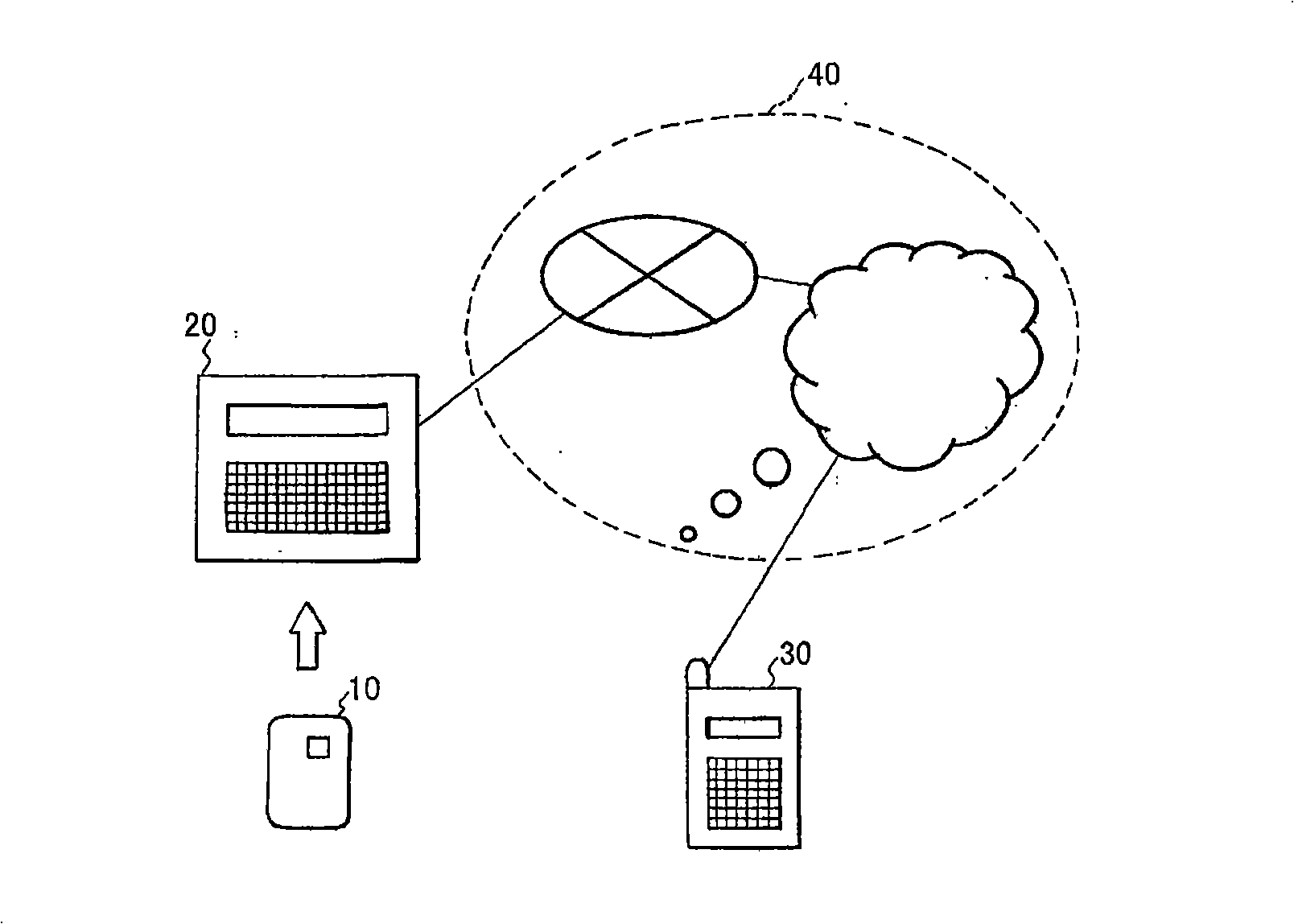
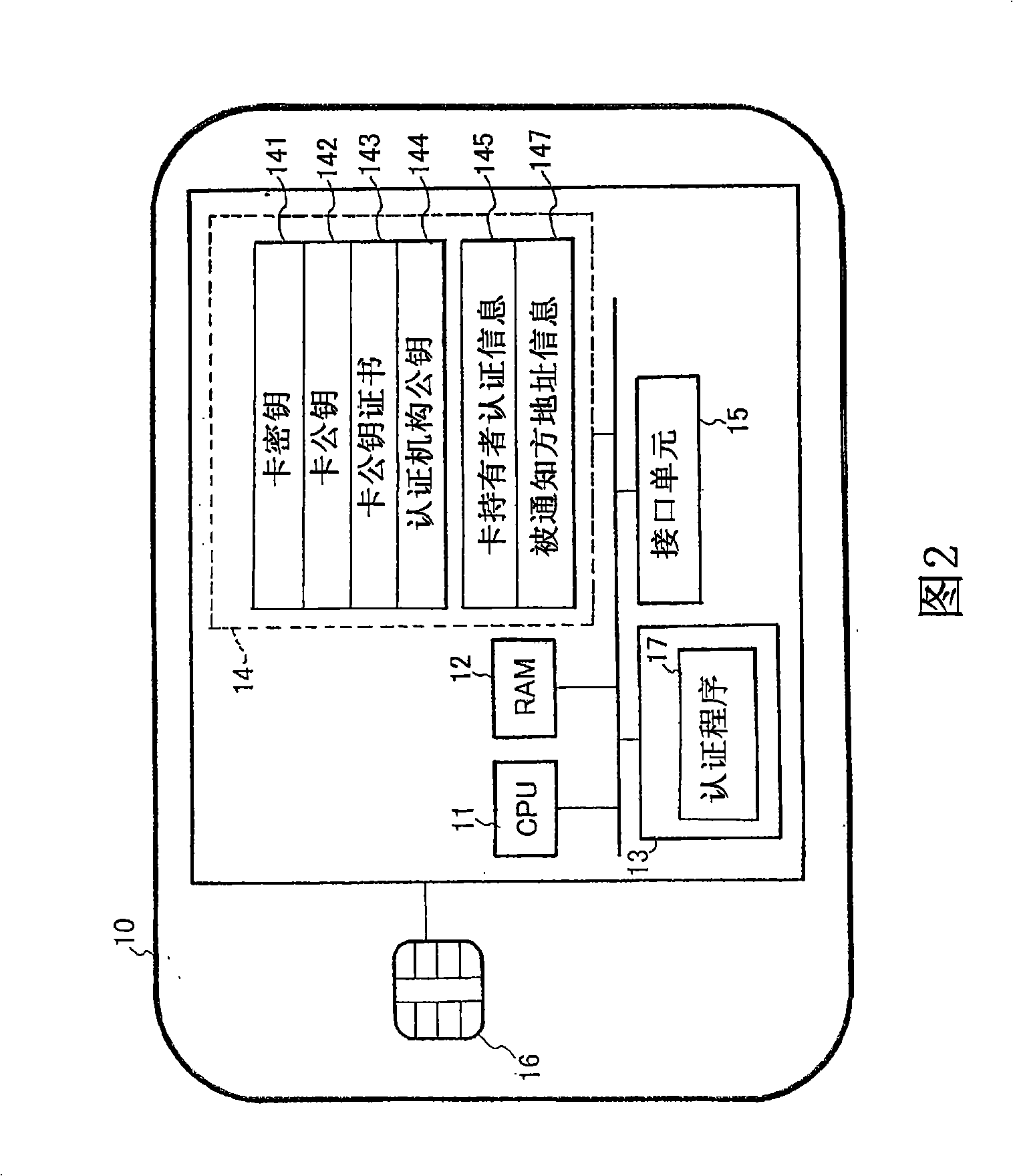
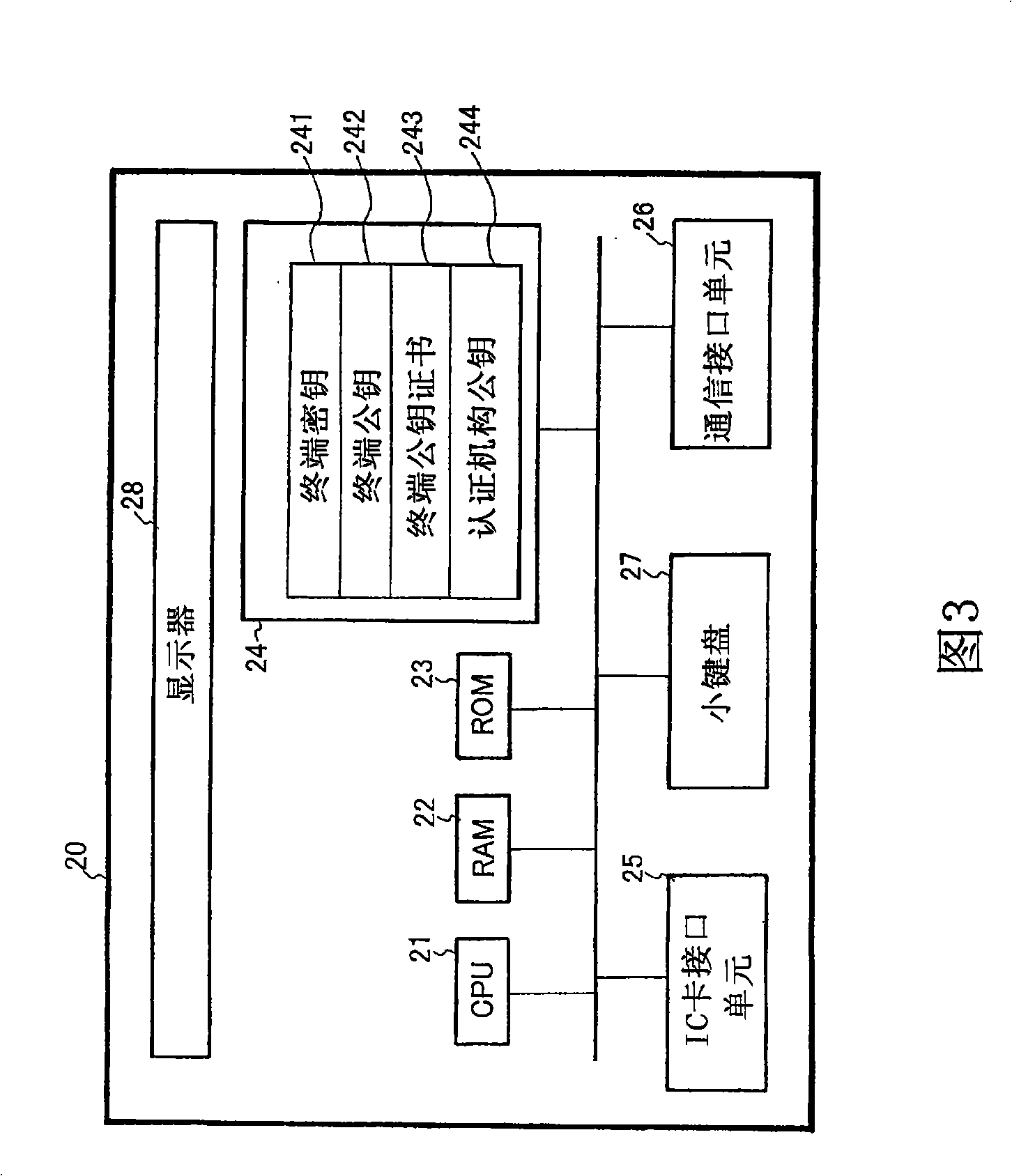
[0108] figure 1 It is a schematic diagram showing the structure of an authentication system using an IC card as the first embodiment of the present invention. figure 1 The illustrated authentication system using an IC card includes an IC card 10, an authentication system terminal 20, a portable inspection device 30, and a communication line 40 connecting the authentication system terminal 20 and the portable inspection device 30. The IC card 10 is used as an information processing card having an information processing function.
[0109] The communication line 40 is a telephone line, the Internet, a radio wave connection (wireless communication), or the like.
[0110] When receiving various services using the IC card, the user inserts the IC card 10 into the authentication system terminal 20, and inputs a password (equivalent to authentication information) through the keypad of the authentication system terminal 20.
[0111] T...
no. 2 example
[0216] Next, a second embodiment of the present invention will be described with reference to the drawings.
[0217] Picture 9 It is a schematic diagram of the structure of an authentication system using an IC card according to the second embodiment. Picture 9 The illustrated authentication system using an IC card includes an IC card 10a, an authentication system terminal 20a, and a portable inspection device 30a.
[0218]In order to receive various services through the IC card 10a, the user inserts the IC card 10a into the authentication system terminal 20a. After the IC card 10a is returned from the authentication system terminal 20a, the user inserts the IC card 10a into the portable inspection device 30a. In accordance with the information displayed on the portable inspection device 30a, the user inputs a password (or authentication information) through the keypad of the authentication system terminal 20a.
[0219] Using the entered password, the authentication system termi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com