Suspected network threat information screener and screening and processing method
An information screening and suspicious technology, applied in the direction of security communication devices, digital transmission systems, electrical components, etc., can solve the problems of slow protocol analysis and processing speed, low system performance, missing data packets, etc., to improve detection efficiency and processing Powerful functions, saving hardware resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
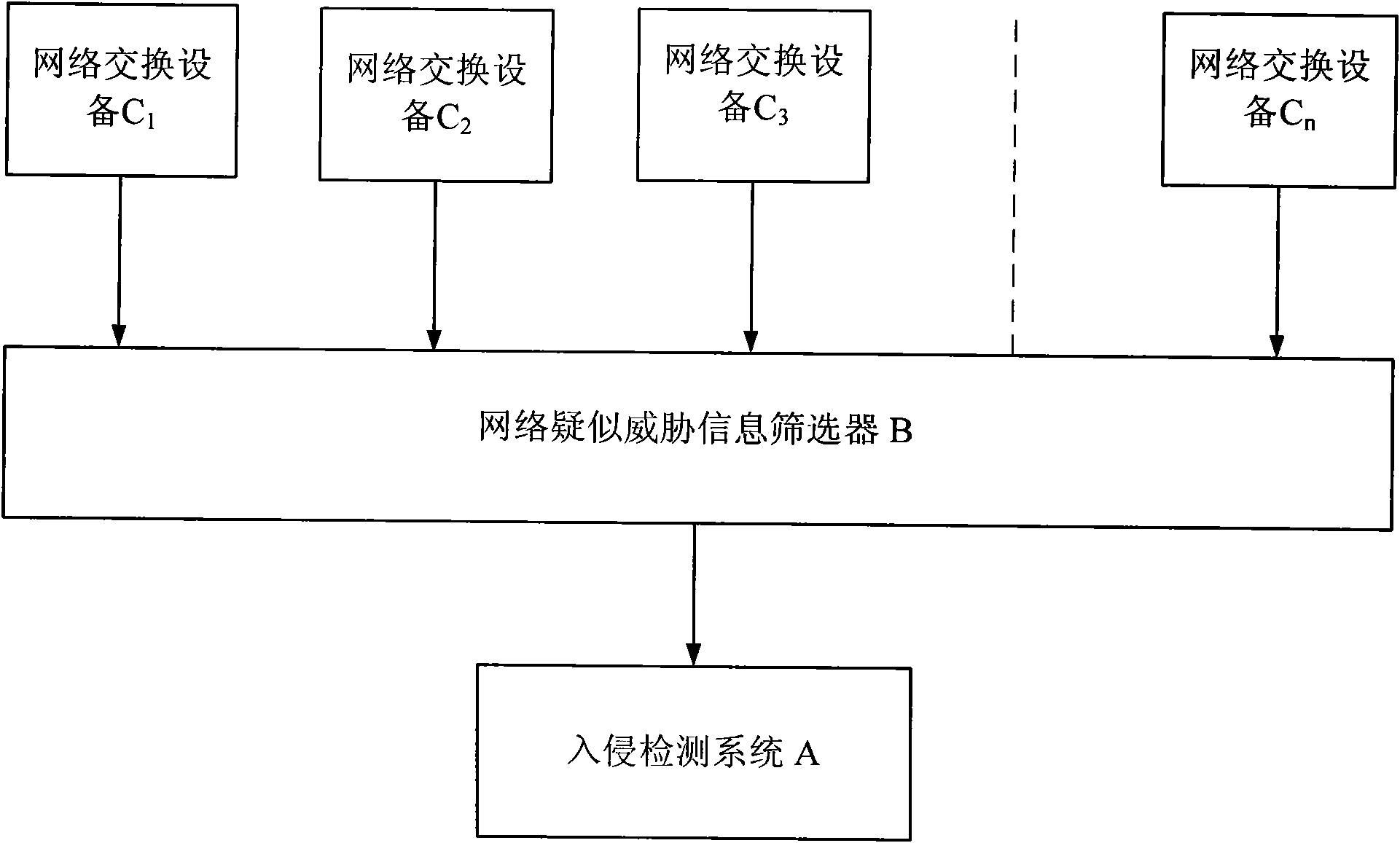
[0025] In this embodiment, there are 10 sets of network switching equipment (C 1-10 ) and the corresponding intrusion detection system A as an example:
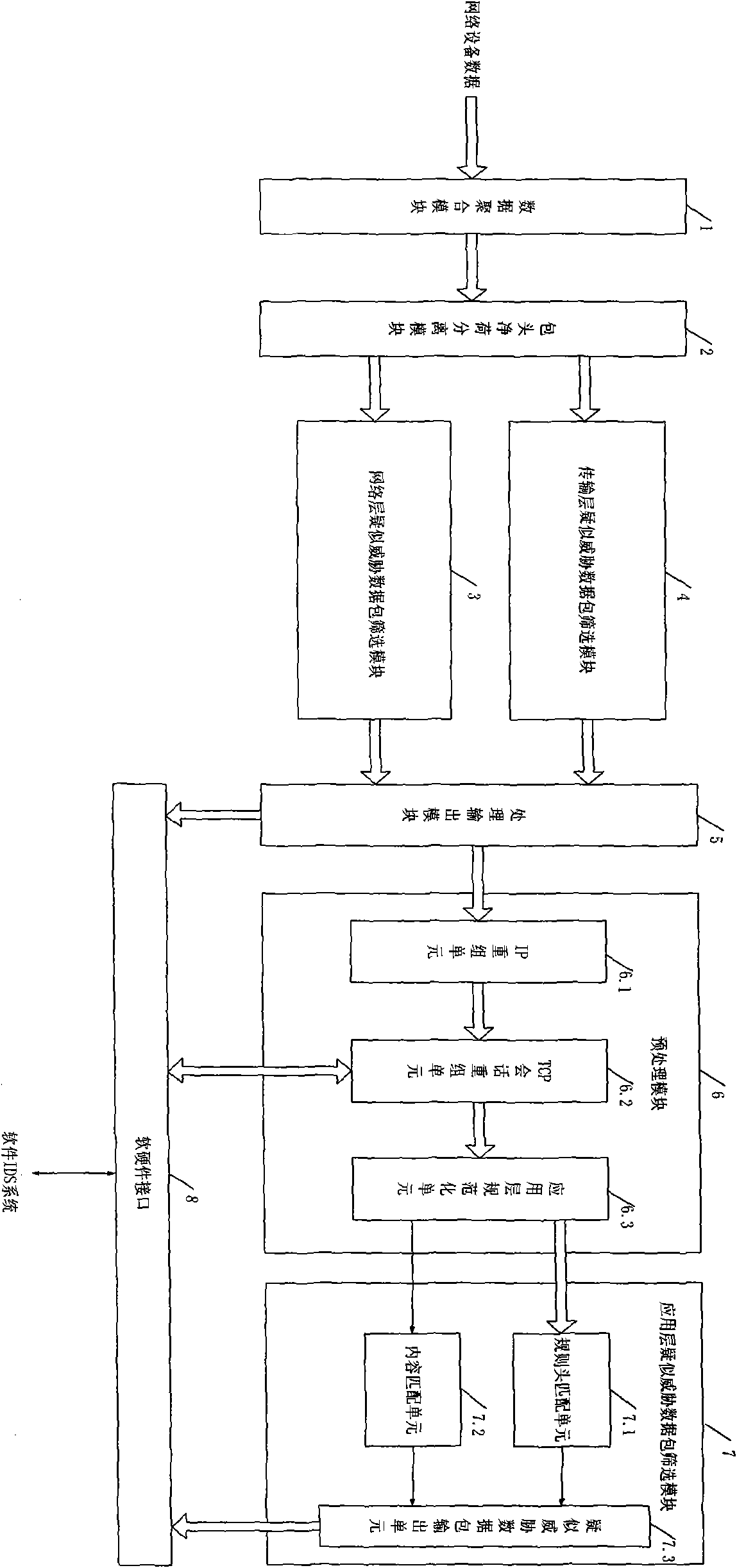
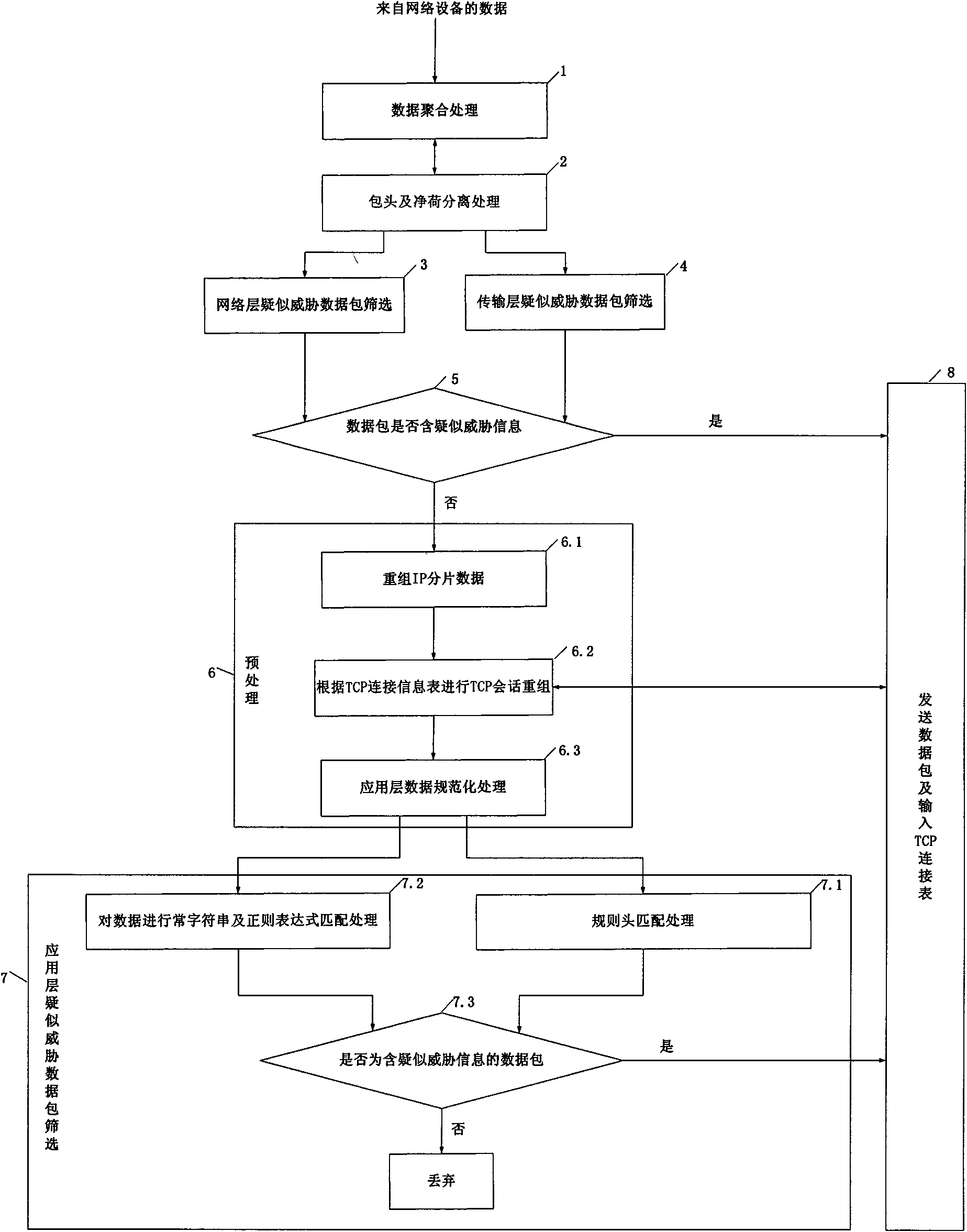
[0026] The filter B in the present embodiment adopts the STRATIX III EP3SL150F FPGA (Field Programmable Gate Array) device produced by ALTERA Company as the filter body, wherein it is set: data aggregation module 1 resource configuration 1500 logic units and 0.5 megabit RAM ; The packet header and payload separation module 2 resource configuration is 600 logical units; the network layer suspected threat data packet screening 3 resource configuration is 1500 logical units; the transmission layer suspected threat data packet screening module 4 resource configuration is 1500 logical units; processing output Module 5 resource configuration is 150 logical units; in preprocessing module 6: IP reassembly unit 6.1 resource configuration is 2000 logical units and 5 Mbit RAM, TCP session reassembly unit 6.2 resource configuration is 20...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com