Computer remote security control method
A security control and computer technology, applied in the direction of user identity/authority verification, transmission system, electrical components, etc., can solve the problems of lack of authority control information transmission, lack of identity authentication of participating nodes, etc., to ensure system security and legitimacy , the effect of ensuring stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
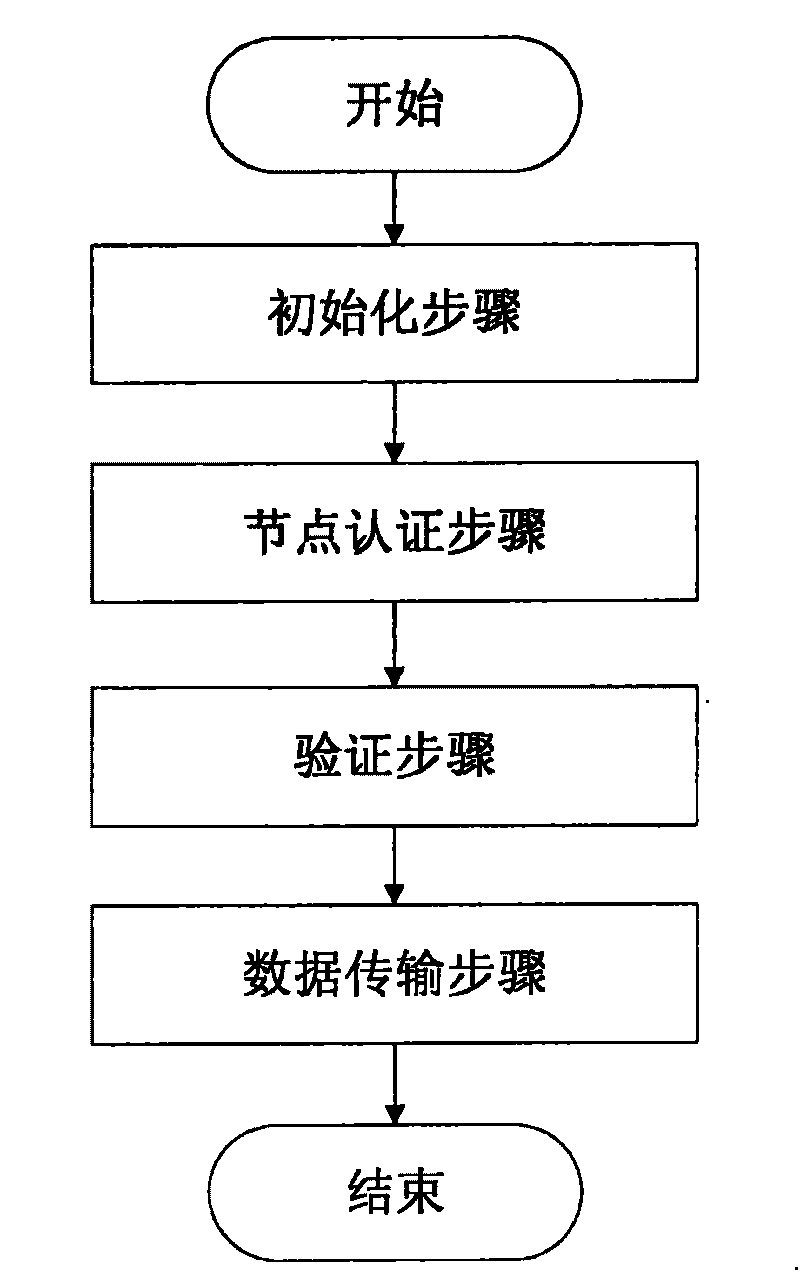
[0065] Such as figure 1 Shown, the present invention carries out following steps in sequence:
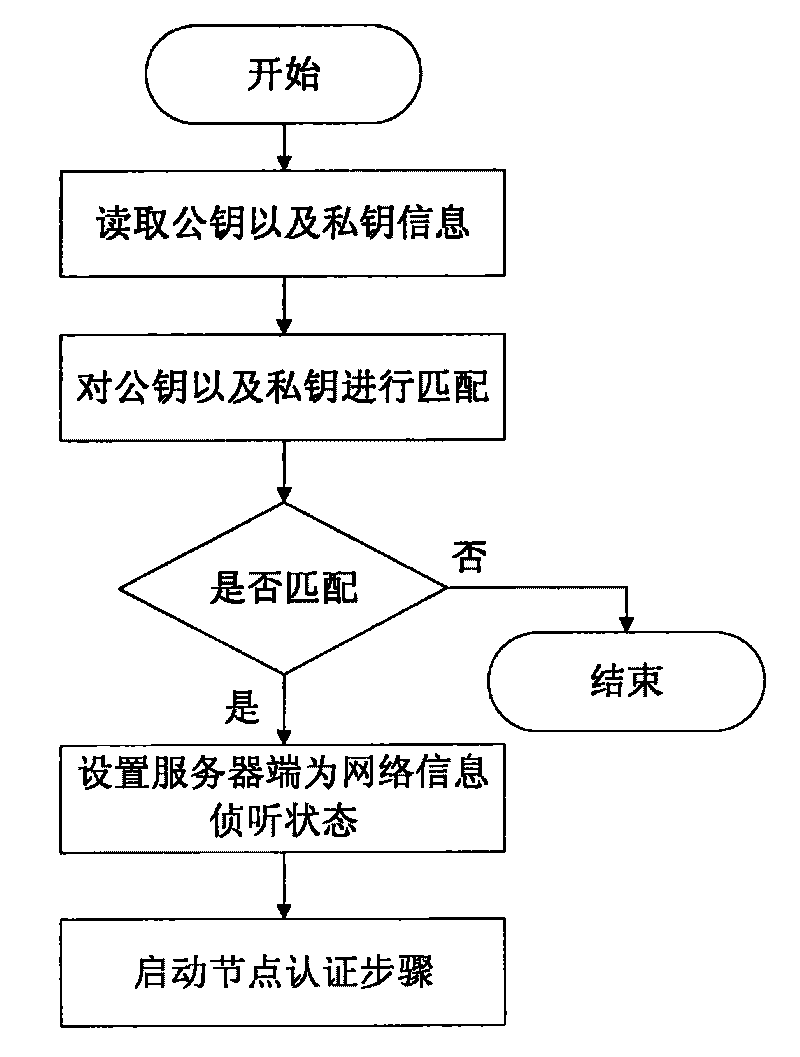
[0066] The initialization step of A mainly includes verifying the matching situation of the certificate file; setting the server side so that the server side is in the state of link listening.
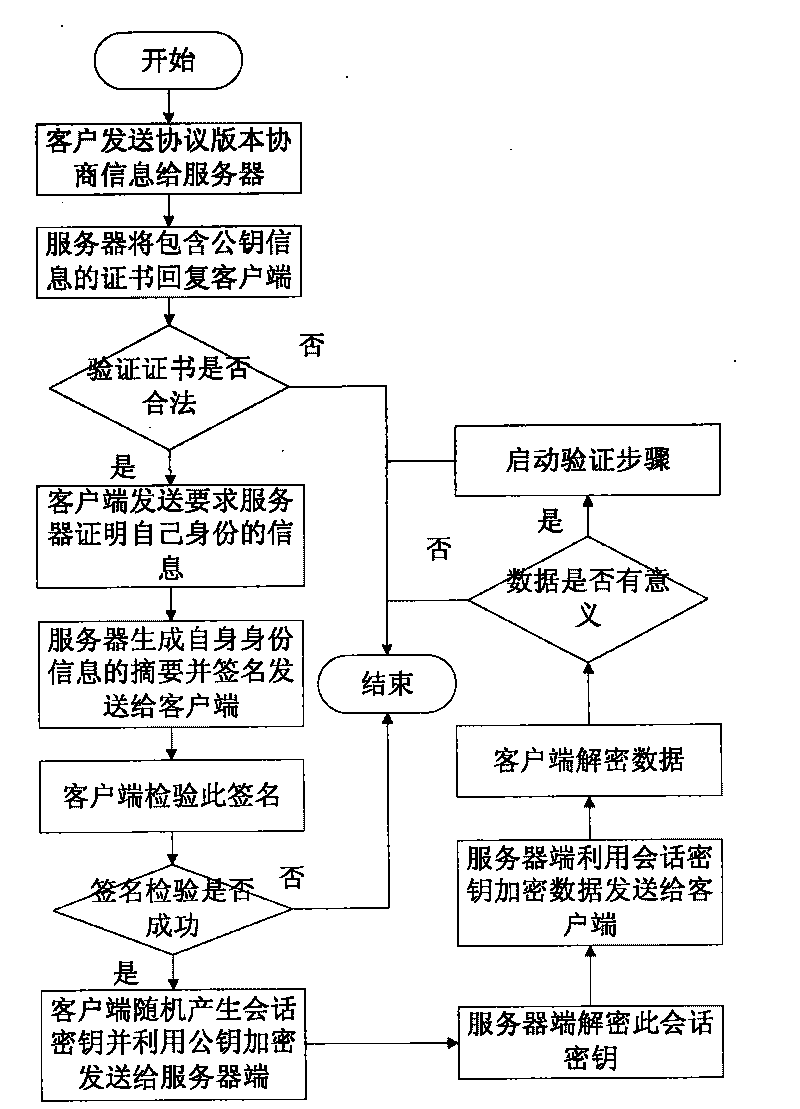
[0067] In the node B authentication step, the client sends information to the server, and the server sends its own certificate to the client. The client verifies the server's certificate and asks the server to verify its identity. The server sends information signed by the private key to the client to verify its identity. Finally, the client sends the session key information encrypted with the public key to the server. If the server can use this session key to communicate with the client, the authentication between nodes is successful.
[0068] In step C of verification, the server generates a random number and sends it to the client, and the client uses the user's login password to encr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com