Flow limit system and method thereof based on network processor
A network processor and traffic limitation technology, applied in the field of network information security, can solve problems such as difficulty in guaranteeing QoS, lag, and inability to guarantee QoS, and achieve the effects of shortening the development cycle, ensuring QoS, and ensuring stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
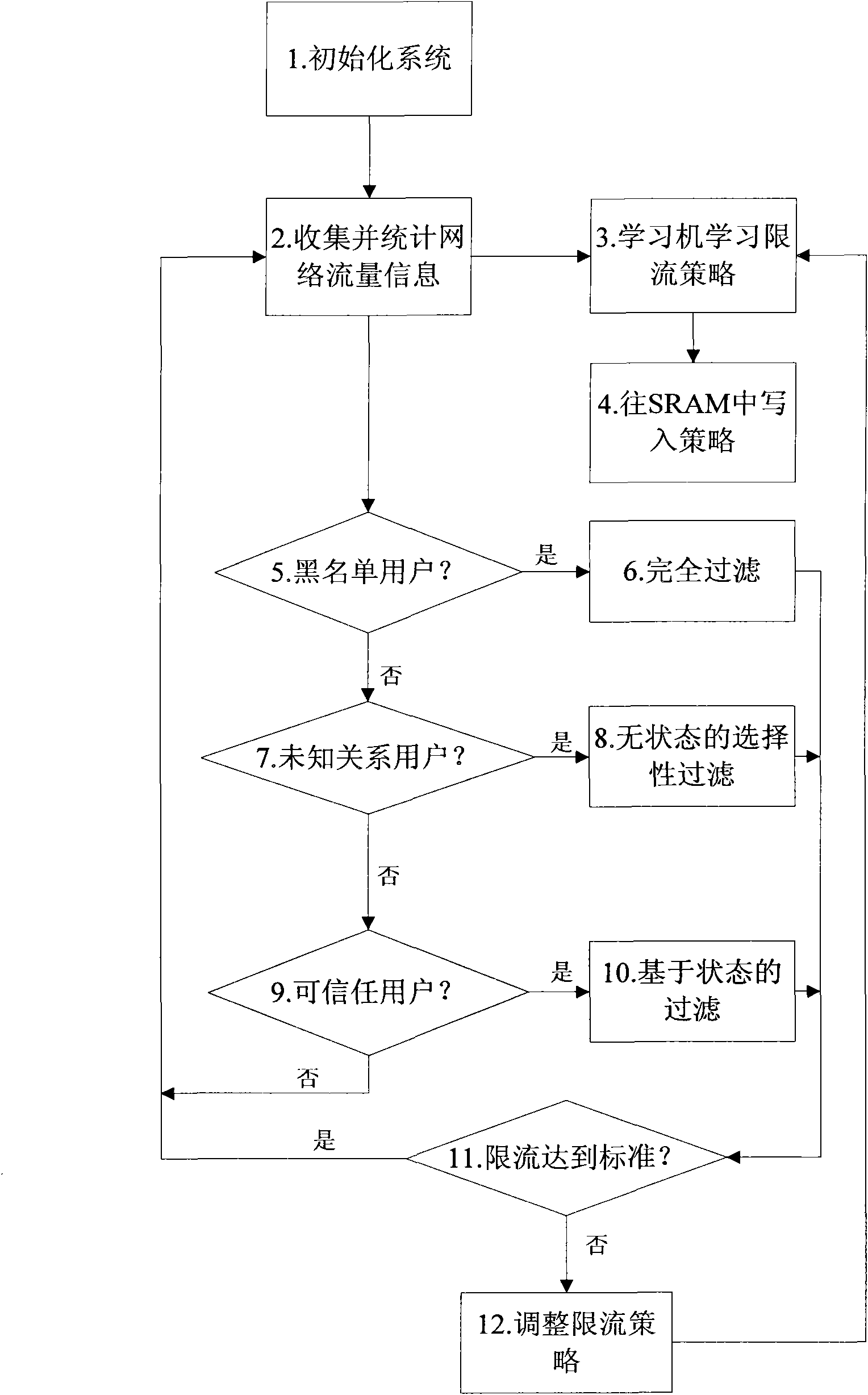
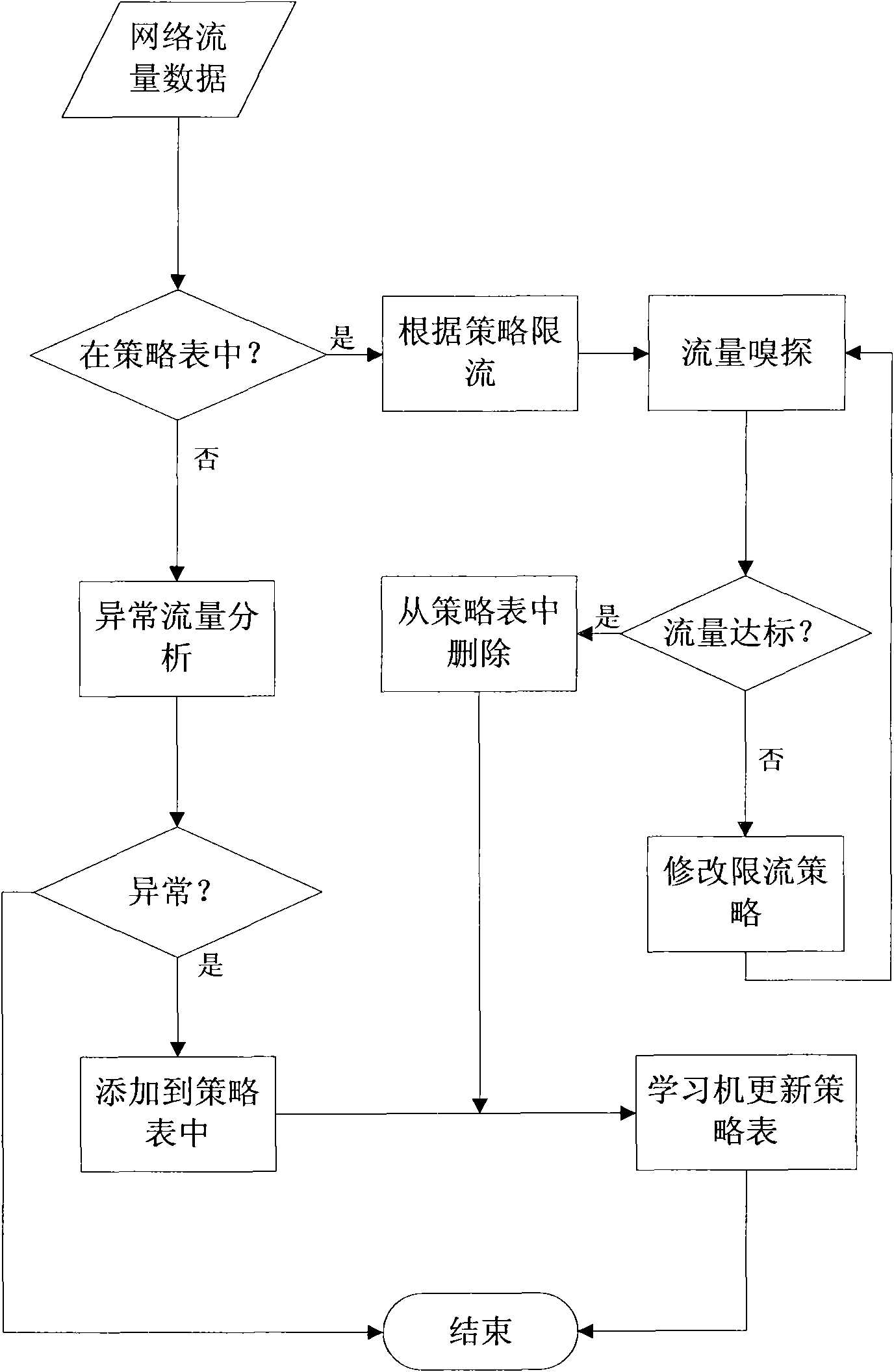
[0039] The present invention will be further described in detail below in conjunction with the embodiments and drawings, but the embodiments of the present invention are not limited thereto.
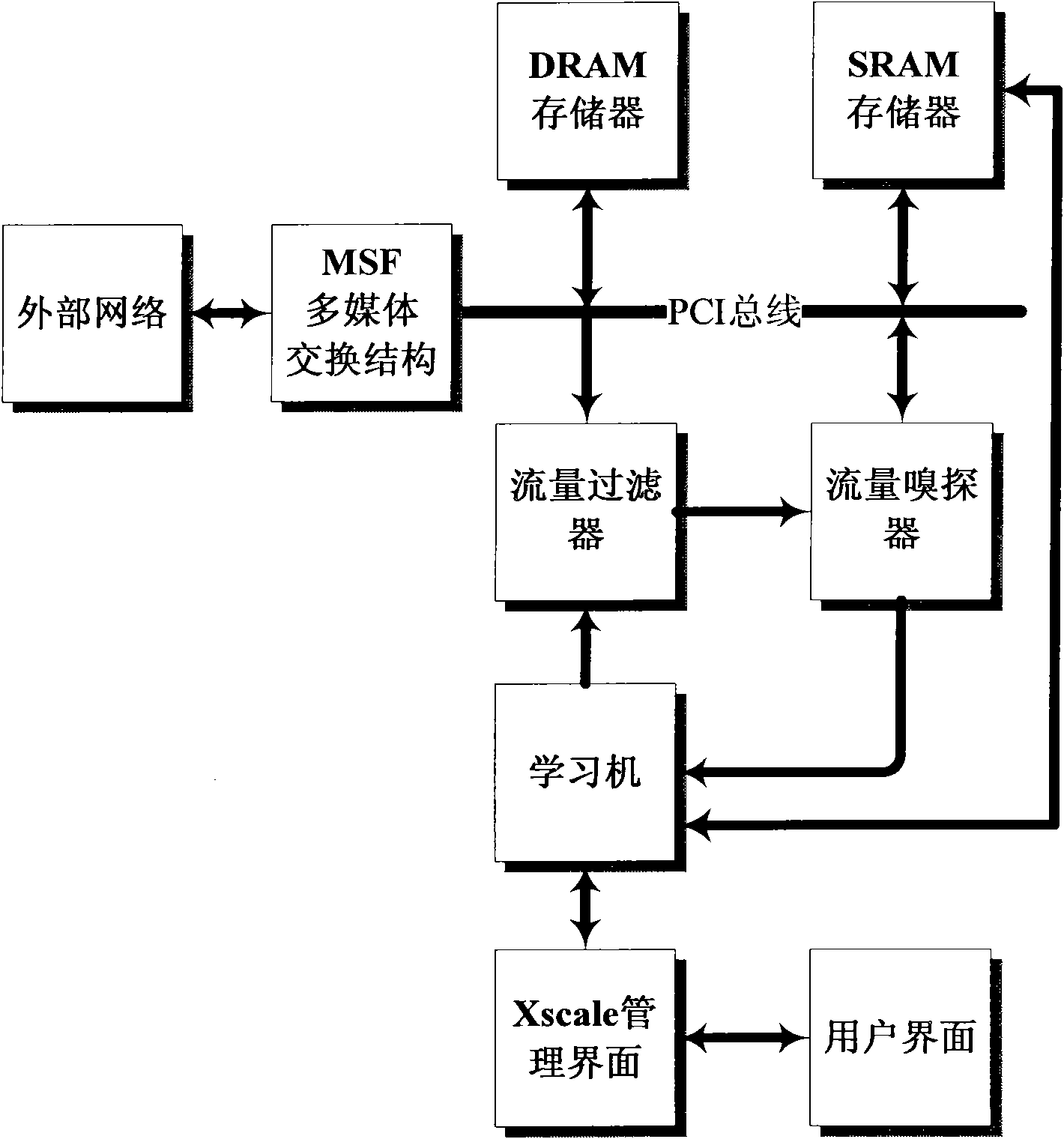
[0040] like figure 1 As shown, a flow limiting system based on a network processor includes a network processor and a host computer; the network processor is connected with a DRAM memory and an SRAM memory.
[0041] Among them, the DRAM memory is used to store the original information of the data packet, including source address, destination address, source port number, destination port number, protocol type and data packet size, etc.; Status information includes flow size and time, etc.
[0042] The network processor is composed of micro-engine cluster, Xscale Core and MSF switching structure in hardware.
[0043] The software of the network processor includes MSF switching structure, traffic sniffing micromodule, traffic filtering micromodule, learning machine and Xscale management i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com