Technology for detecting fault of Linux system by using mandatory access control
A technology of mandatory access control and system failure, applied in the detection of faulty computer hardware, etc., can solve problems such as weak audit protection, security problems, verification and evaluation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
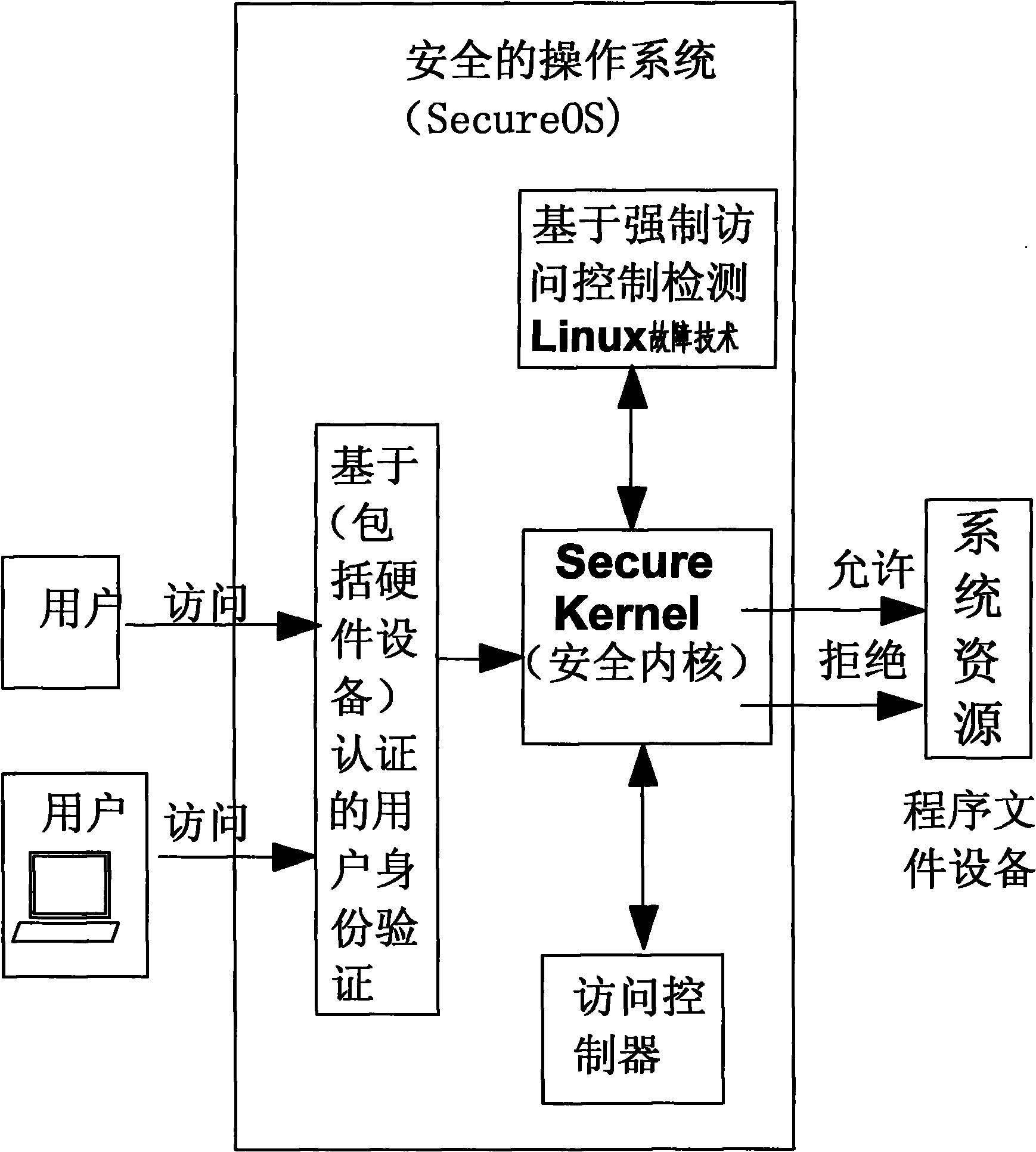
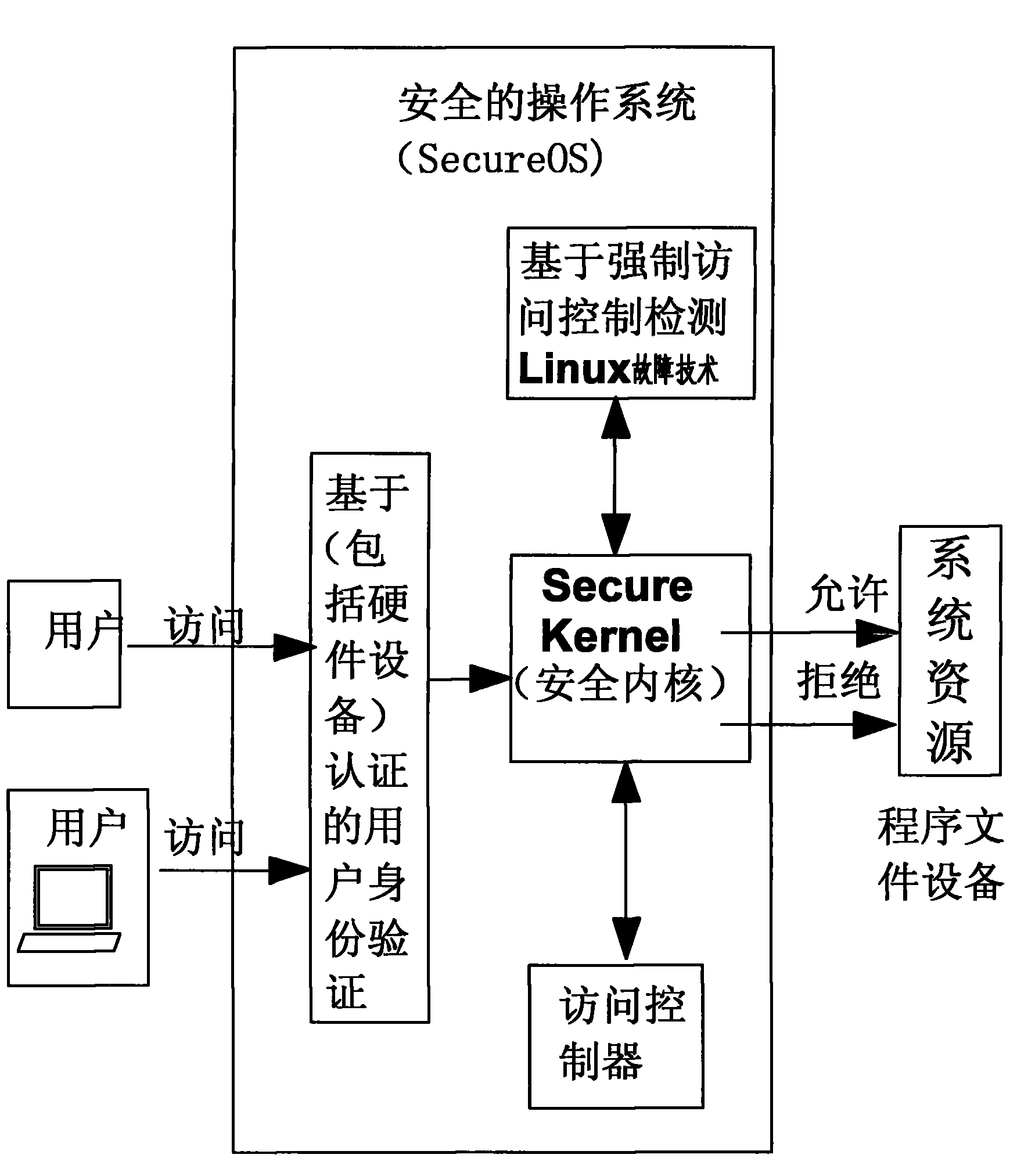
[0034] Add a secure kernel module to the driver layer (layer 0), intercept and record all kernel access paths, so as to meet the technical requirements for handling Linux server failures. The security effect achieved is similar to that of refactoring operating system code technology. The advantage is that it will not affect the customer's business continuity, and even does not require the customer to restart the system. It not only supports all applications on the upper layer, but also supports all systems and machines on the lower layer, and can guarantee the security of upper layer applications at the granularity of the operating system.
[0035] It mainly consists of the following modules:
[0036] 1. Mandatory access control MAC
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com