Method for discovering software vulnerabilities
A software vulnerability and conditional jump technology, applied in the field of software engineering and information security, can solve problems such as difficulty in finding different data with the same verification value, difficulty in mining dynamic vulnerabilities in verification software, and damage to data integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
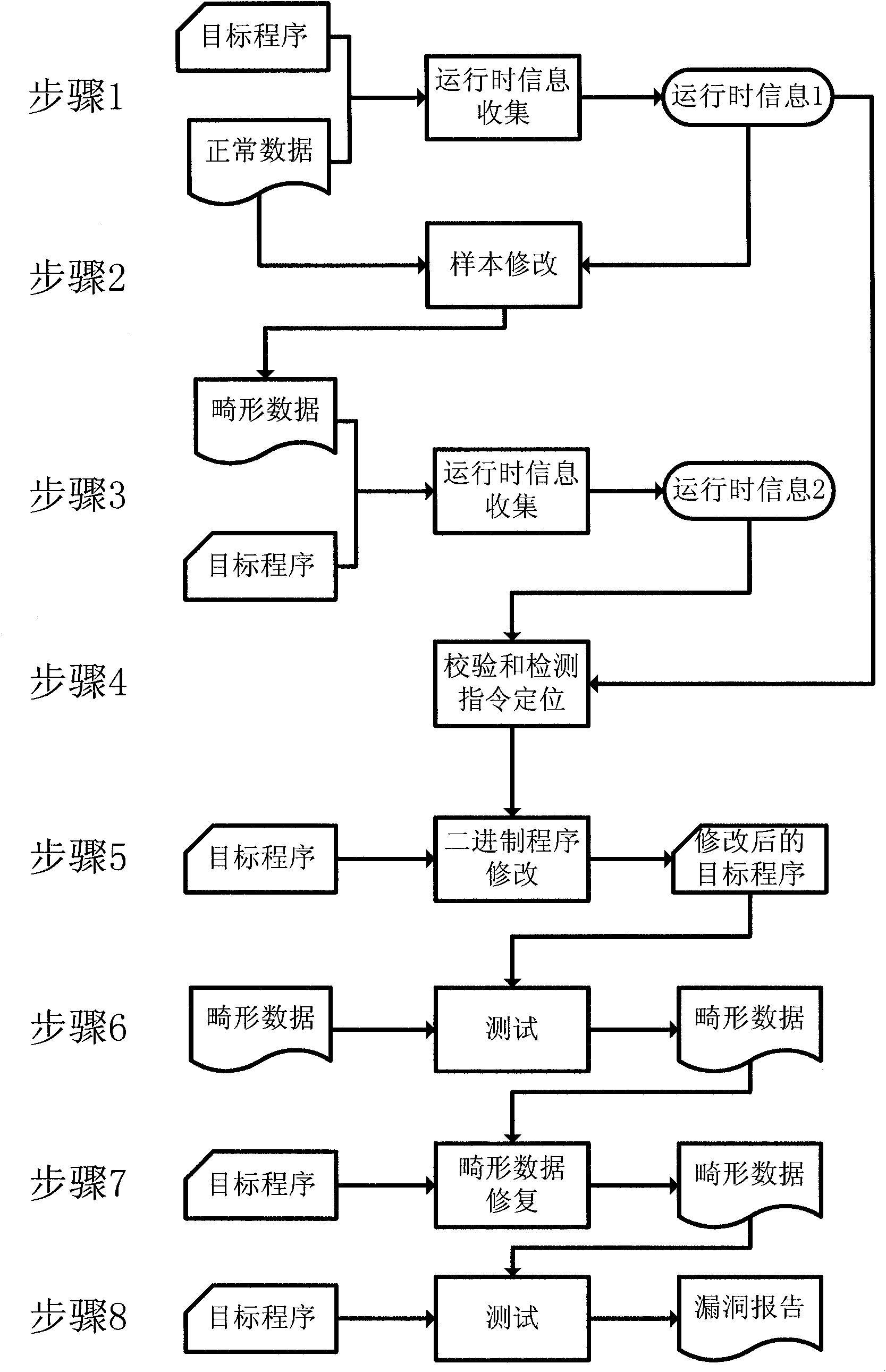
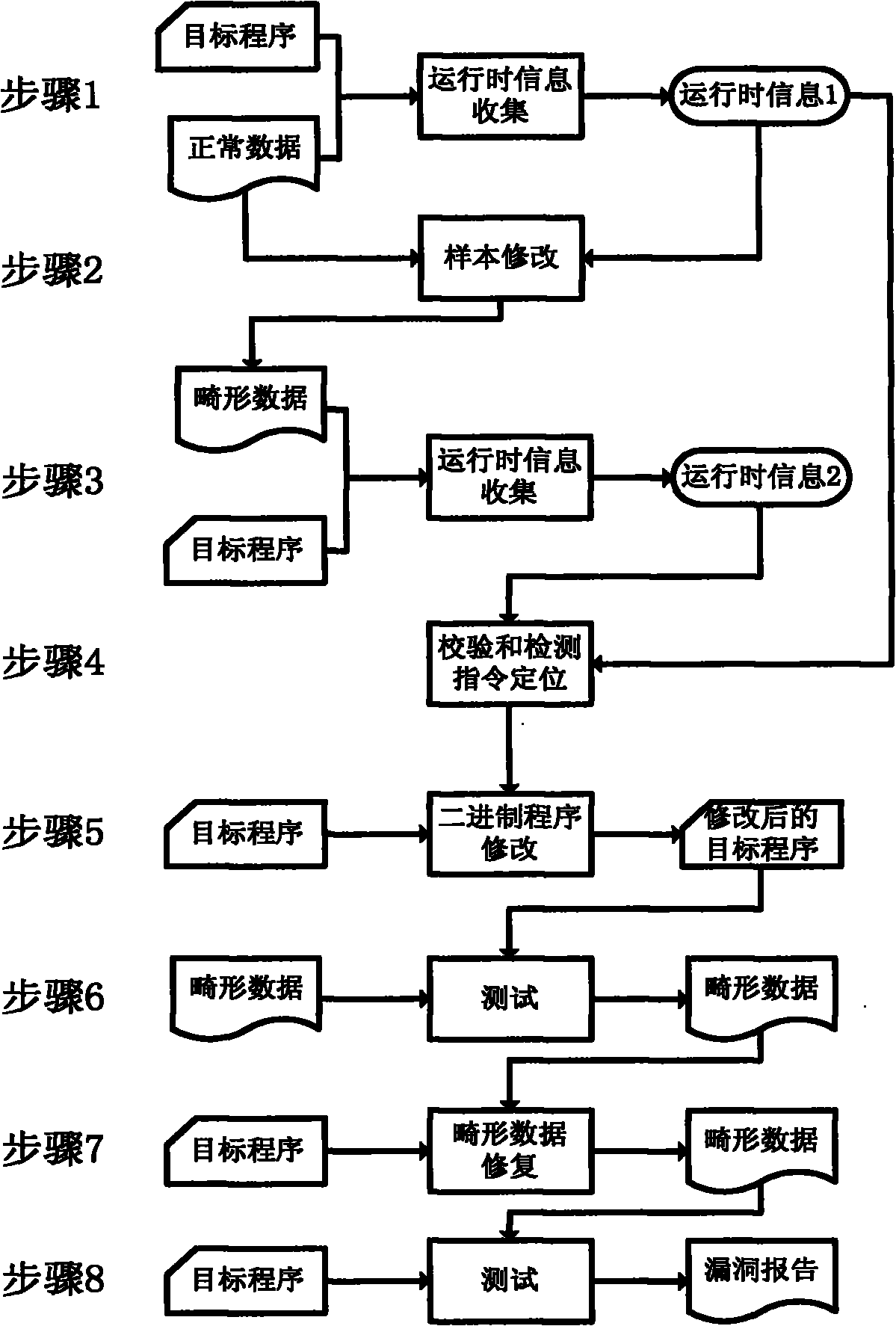
[0067] Attached below figure 1 , to describe the specific embodiment of the present invention in more detail. This implementation example uses Intel's binary implant platform PIN and Microsoft's constraint solver Z3 to give a detailed implementation and operation process, but the scope of protection of the present invention is not limited to this embodiment.
[0068] Step 1. Run normally to input data and collect sensitive information when the target program is running.
[0069] 1.a) Hijack system calls for operating system file operations and network data operations. Based on the API interfaces PIN_AddSyscallEntryFunction and PIN_AddSyscallExitFunction of the PIN platform, hijack the parameters and return values of the corresponding system calls. By hijacking the system calls of opening, reading, and closing some files, such as hijacking NtCreateFile, NtOpenFile, and NtReadFile on the Windows platform, hijacking open, read, close, seek, lseek, etc. on the Linux platform, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com