Method and system for realizing service application safety
A technology of business application and implementation method, which is applied in the direction of security devices, transmission systems, usage of multiple keys/algorithms, etc., and can solve the problems of reduced security, insufficient security of key strength and algorithm, and difficulty in effectively guaranteeing business security, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
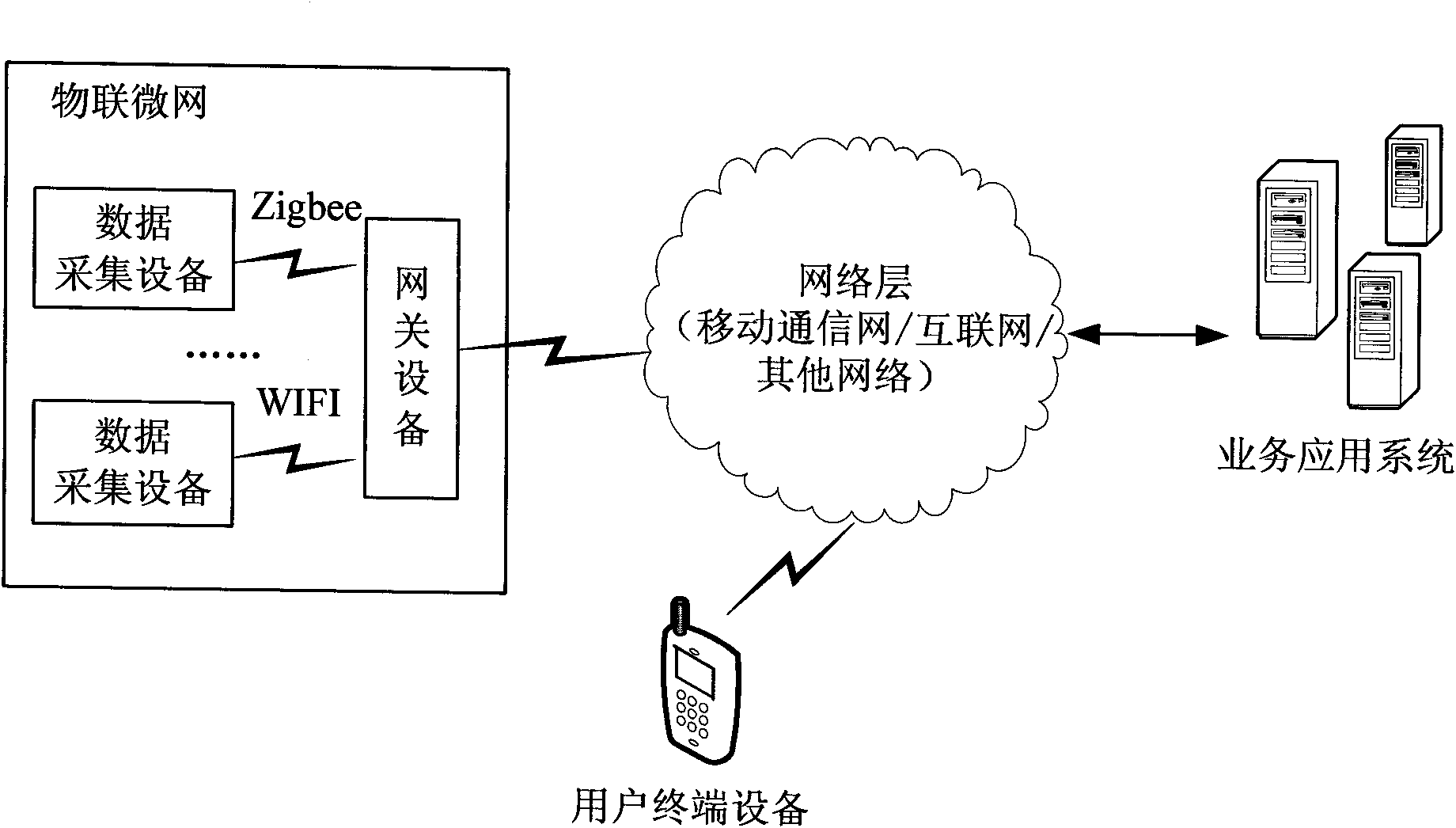
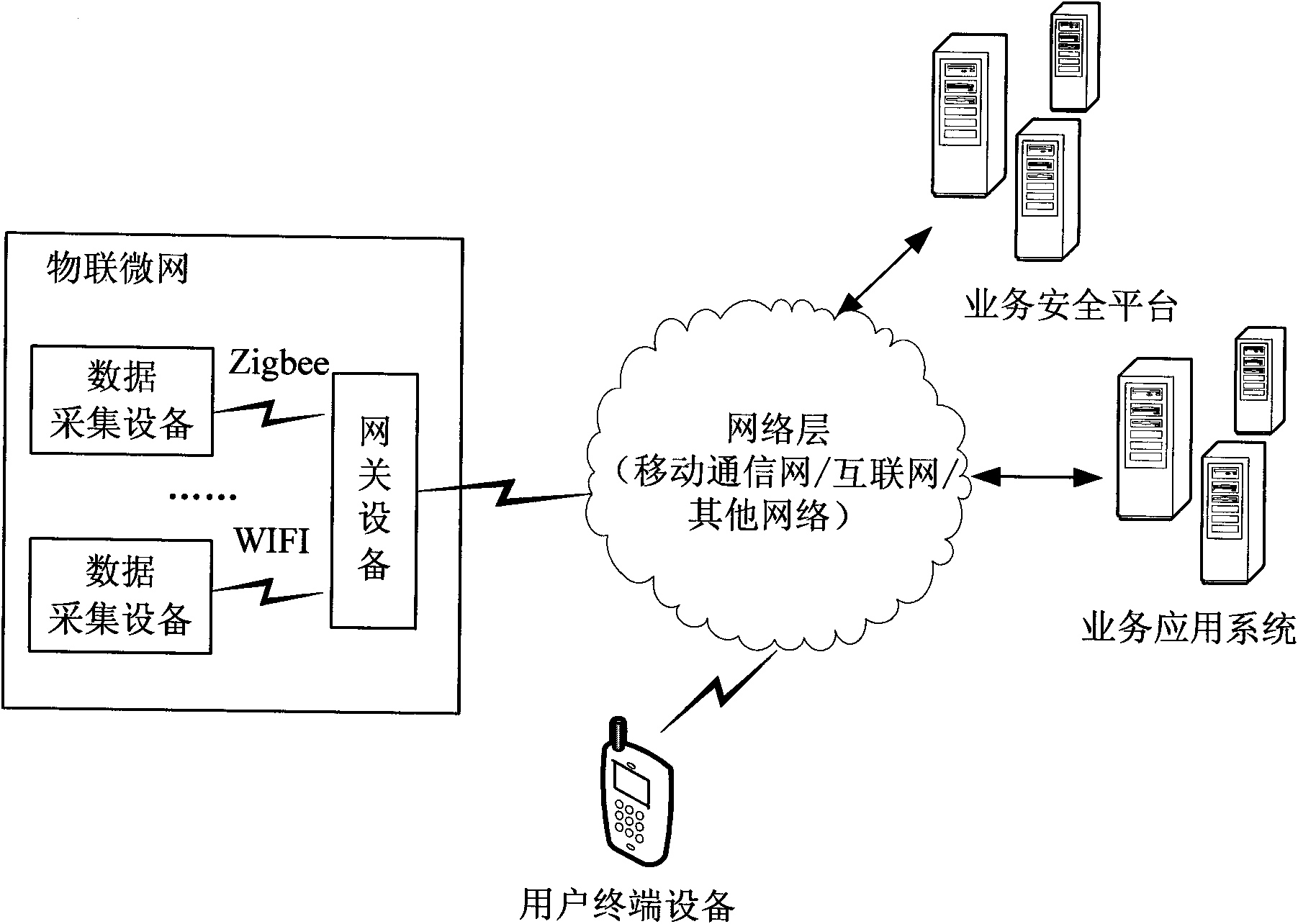
[0106] The Internet of Things business security system provided by this embodiment is as follows: figure 2 As shown, a business security platform is built in the original Internet of Things architecture, which can communicate with business application systems, wireless communication devices of the Internet of Things and user terminal devices through the network. It can also communicate with OTA (over the air) platform, BOSS (business operation support system) and other business security platforms.
[0107] In order to improve the security of data transmission between devices, this embodiment realizes the safe storage and distribution of keys through the business security platform. Due to the great uncertainty and unpredictability of the relationship between the devices used together, such as A controlled device with positioning function is built in a pet collar, and the key can be preset in the device. After the user purchases the pet collar, he can determine to use, for exa...
no. 2 example
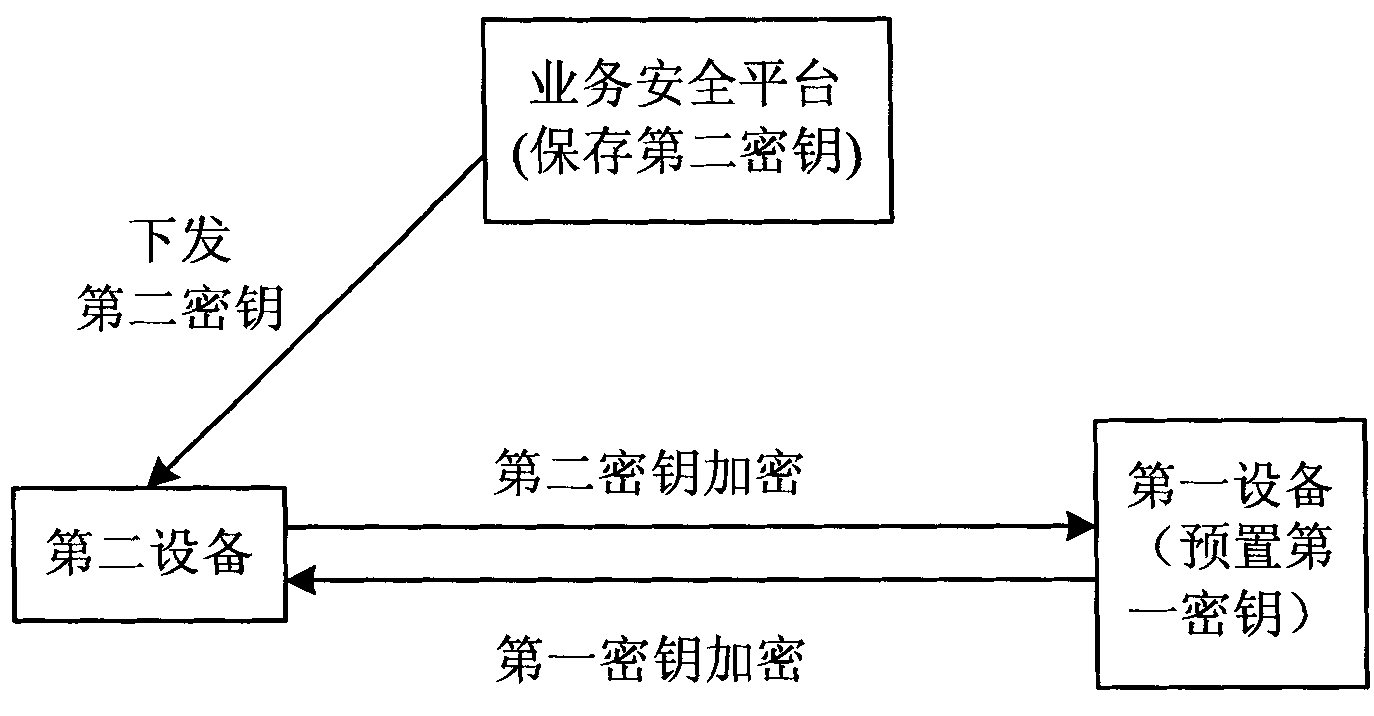
[0156] The IoT service security system of this embodiment is the same as the first embodiment, and also has a service security platform. The process of key generation, storage and distribution in this embodiment is different from that in the first embodiment, and the schematic diagram is as follows Image 6 shown. The corresponding process is as Figure 7 shown, including:
[0157] Step 210, generating the first key and the second key by a trusted institution, same as step 110;
[0158] Step 220, saving the first key and the second key in the service security platform and establishing an association relationship with the security module identifier of the first device;
[0159] The security module identification is preferably generated or acquired by the organization that generates the first key and the second key, and then provided to the operator who manages the service security platform.
[0160] Step 230, the service security platform receives an association request for...
no. 3 example
[0179]The IoT service security system of this embodiment is the same as the first embodiment, and also has a service security platform. The key generation, storage and distribution process of this embodiment is different from the first and second embodiments, the schematic diagram is as follows Figure 8 shown. The corresponding processes include:
[0180] Step 1, the first device generates a first key and a second key for use together;
[0181] Step 2: The first device saves the generated first key, encrypts the second key and the preset security module ID of the device and uploads it to the service security platform, and the service security platform saves the second key and the security module ID after decryption. The module identifies and establishes the relationship between the two;
[0182] The first device can use the public key used by the service security platform for data transmission to encrypt, and the service security platform can use its own private key for da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com