Safe transmission method of physical layer in wireless communication
A technology of physical layer security and transmission method, which is applied in the field of wireless communication systems, can solve problems such as high power utilization, inability to effectively demodulate information, low power utilization, etc., and achieve the effect of high power utilization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below in conjunction with the accompanying drawings and specific examples.
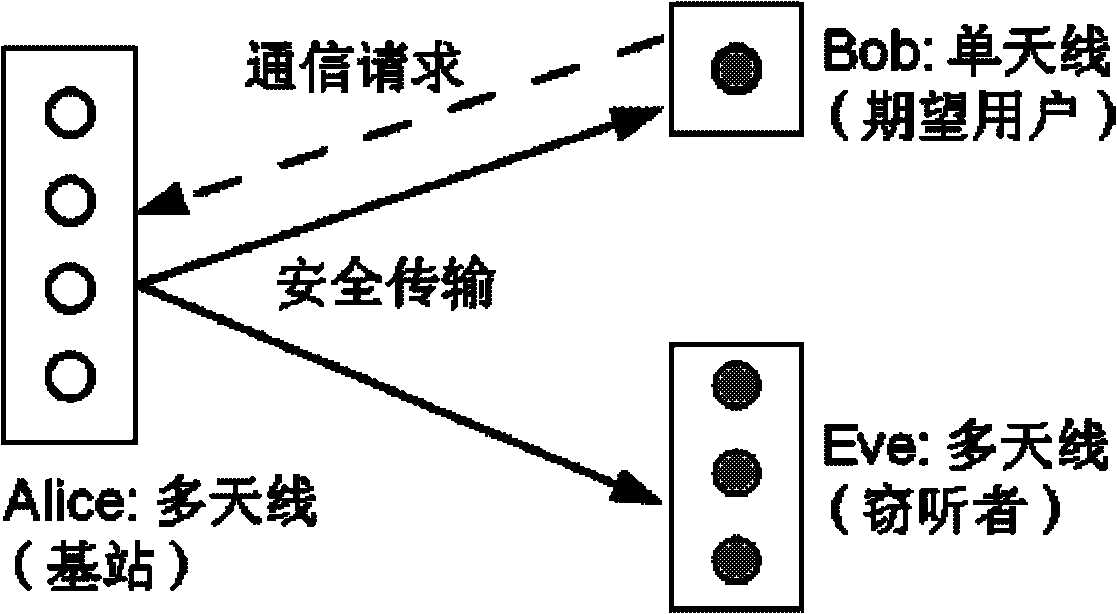
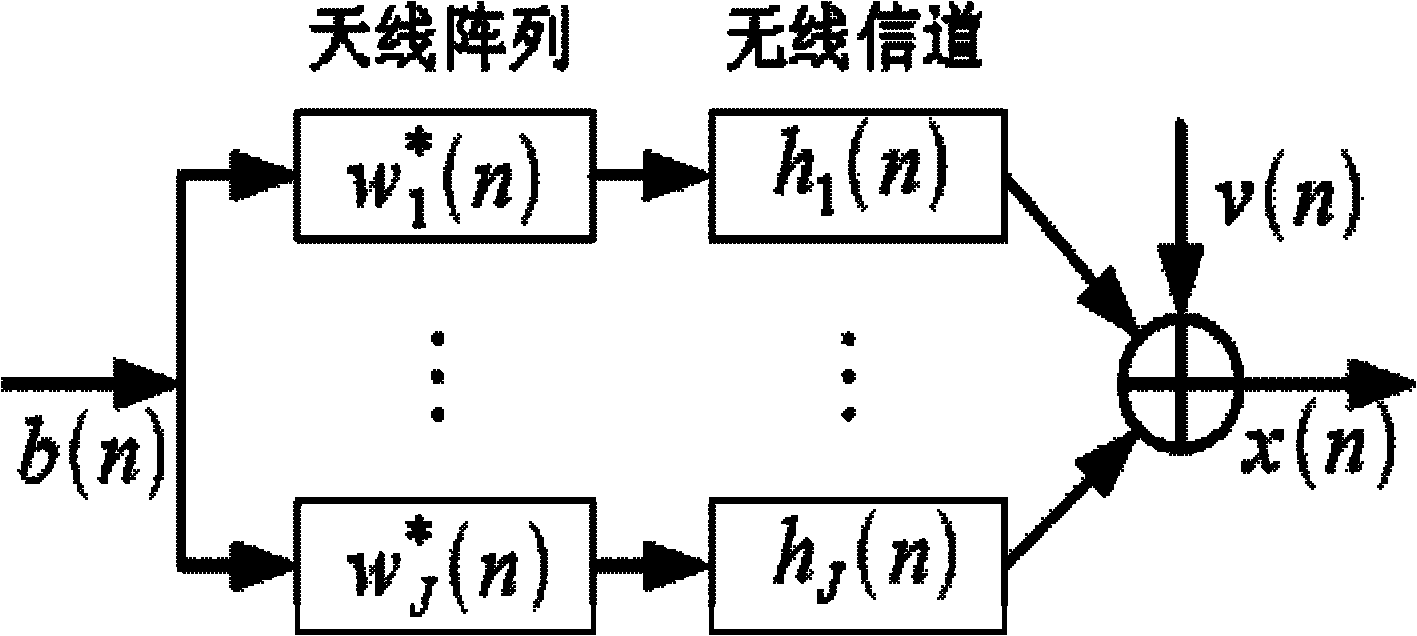
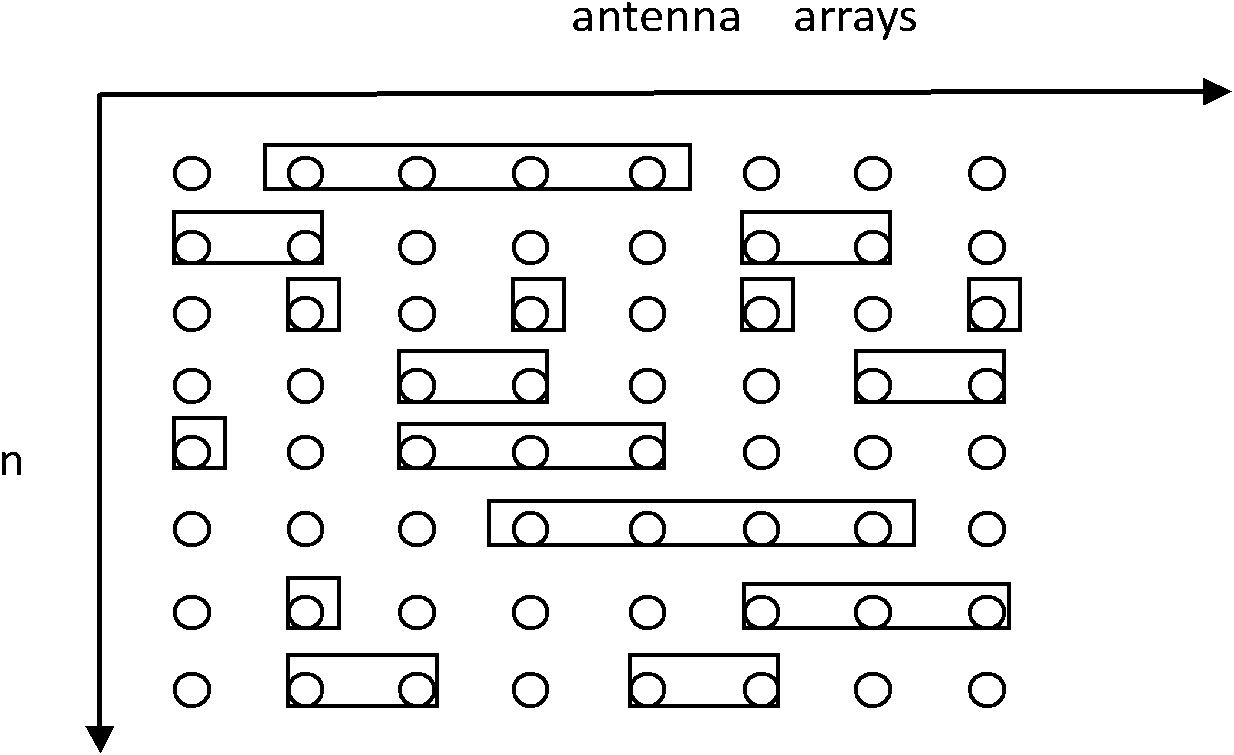
[0025] The present invention relates to a system model of secure transmission such as figure 1 As shown, base station Alice has multiple antennas, expects user Bob to use a single antenna, and eavesdropping user Eve adds multiple antennas to obtain information. In the specific implementation here, the base station J=8 antennas are selected, 1 antenna is expected for the user, and 4 antennas are used for the eavesdropping user. The significance of secure communication is that the symbols transmitted by the base station are only expected to be obtained by expected users, but not by eavesdropping users. The eavesdropping user here is passive, that is, it only eavesdrops on information and does not transmit signals into space. In addition, this wireless security transmission model generally requires the reciprocity of the sending and receiving chann...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com